The SAMSAM ransomware that attacked the Atlanta City System in the United States earlier, the attacker has received a $6 million ransom in the past two years.

SAMSAM attack method:
Unlike normal ransomware attacks, SAMSAM does not infect regular household users through a wide-spreading way because the success rate of blackmail is too low.
This professional criminal gang focuses on the ransomware business and uses social engineering to carefully select targets and then launch attacks in a targeted manner.
For example, in the current dark market black market, look for the RDP remote protocol password of the target organization, or violently crack the server that forcibly logs in to the victim.
If the infection is successful, all the documents are immediately encrypted with high intensity, forcing the victim to pay the ransom to the criminal gang to obtain the file decryption key.
Unlike WannaCry, which has a wide range of ransomware, SAMSAM ransomware has neither worm modules nor virus-like features.
That is to say, SAMSAM relies entirely on human attackers to manually infect rather than worms to automate attacks, which is also a typical feature of SAMSAM.
Carefully selected targets for huge ransoms:
At present, the ransomware industry has dropped significantly in the mining tide from the end of last year to the beginning of this year, because many entry-level hackers have abandoned ransomware.
The main reason is that many ordinary home users do not care about encrypted files. They encounter ransomware and do not pay the ransom.
For example, WannaCry, which infected more than 200,000 computers last May, only received a $150,000 ransom, which is no match for SAMSAM.
SAMSAM will ask for a ransom of up to $50,000 after successfully infecting large enterprises and institutions, which is hundreds of times more than the industry average.
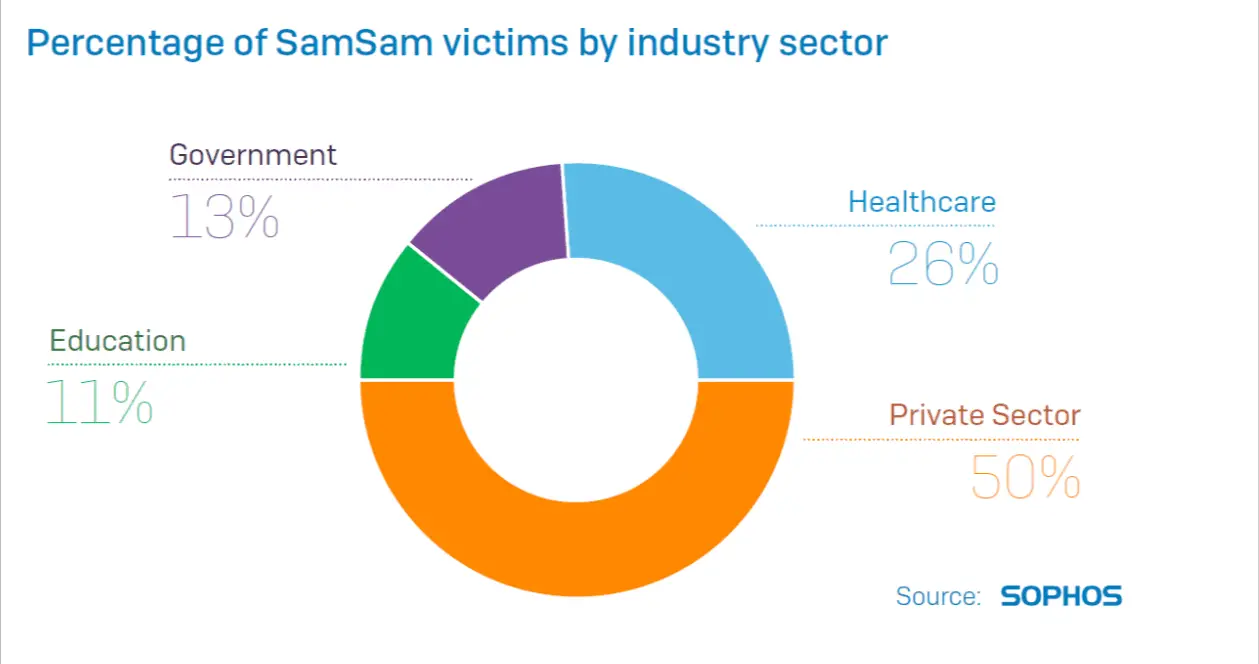
Due to the carefully selected targets that make SAMSAM a very successful rate, most organizations pay ransom after being infected, except Atlanta City.
Earlier, the Atlanta municipal system was directly attacked and lost as much as $2.7 million, but the city did not believe that it could not encourage hackers to be arrogant and then not pay the ransom.
A $6 million ransom in two and a half years:
After a long-term follow-up, the foreign security company SOPHOS analyzed and counted the bitcoin wallet address used by the criminal gang and the flow of bitcoin.
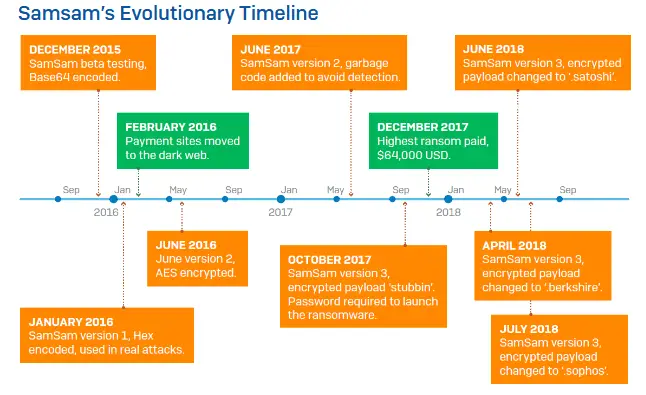
It was finally determined that SAMSAM had received a $6 million ransom since its launch in December 2015, and an average of $10,000 in ransom payments per day.
One of the victims was also carefully selected by the SAMSAM gang, who eventually paid the band for up to $64,000 in ransom.
Daily safety precautions reminder:
The best solution for ransomware attacks is naturally to do an excellent job of data backup every day, which can not only deal with ransomware but also other accidents.
At the same time, the server tries to enable key login or 2-step verification. Both Windows Server and Linux distributions support 2-step verification.
There are also servers that use high-intensity passwords and modify the default port number as much as possible to avoid being hacked and hacked into the server by criminal gangs.
Of course, the extra reminder is that you don’t trust the various download stations, crackers or plug-ins to prevent carrying backdoors.