Sandbox Scryer
The Sandbox Scryer is an open-source tool for producing threat hunting and intelligence data from public sandbox detonation output. The tool leverages the MITRE ATT&CK Framework to organize and prioritize findings, assisting in the assembly of IOCs, understanding attack movement, and threat hunting. By allowing researchers to send thousands of samples to a sandbox for building a profile that can be used with the ATT&CK technique, the Sandbox Scryer delivers an unprecedented ability to solve use cases at scale.
The tool is intended for cybersecurity professionals who are interested in threat hunting and attack analysis leveraging sandbox output data. The Sandbox Scryer tool currently consumes output from the free and public Hybrid Analysis malware analysis service helping analysts expedite and scale threat hunting.

Operation
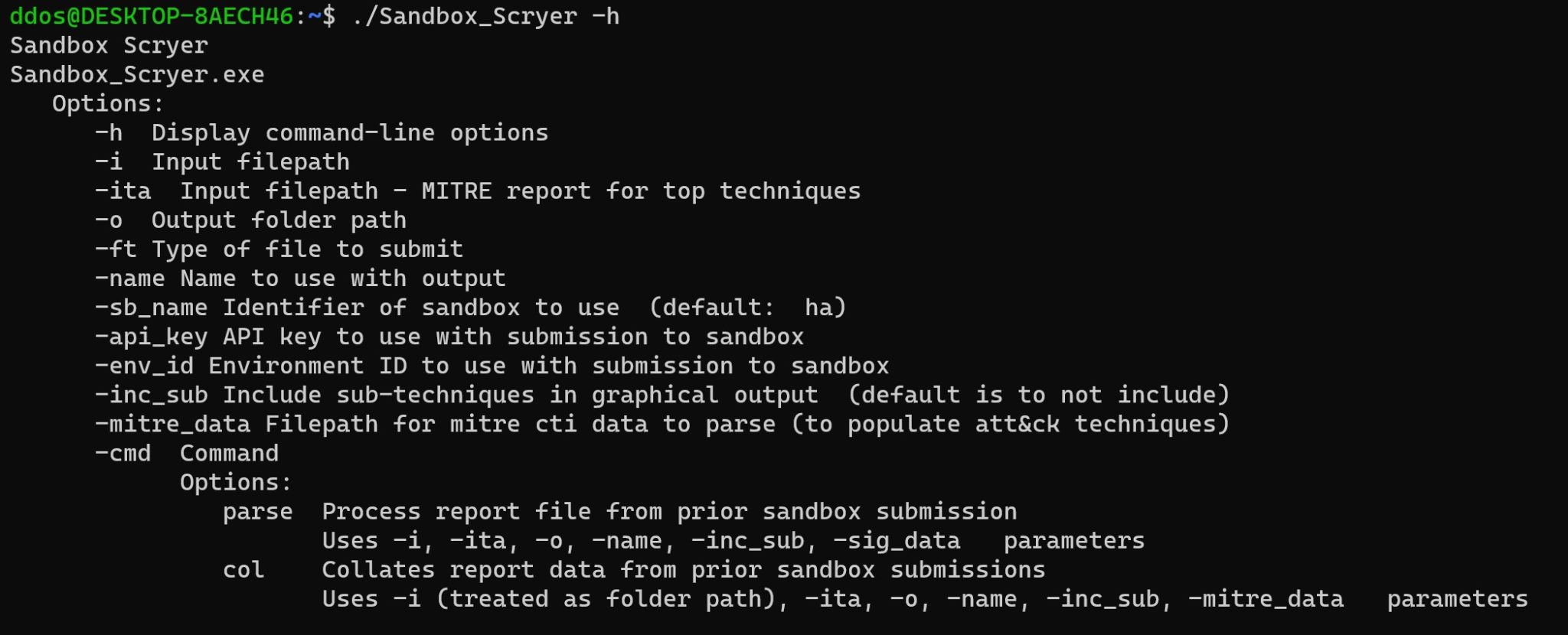
The Sandbox Scryer is intended to be invoked as a command-line tool, to facilitate scripting
The operation consists of two steps:
- Parsing, where a specified report summary is parsed to extract the output noted earlier
- Collation, where the data from the set of parsing results from the parsing step is collated to produce a Navigator layer file
Invocation examples:
-
Parsing
-
Collation
Once the Navigator layer file is produced, it may be loaded into the Navigator for viewing via https://mitre-attack.github.io/attack-navigator/
Within the Navigator, techniques noted in the sandbox report summaries are highlighted and shown with increased heat based on combined scoring of the technique ranking and the count of hits on the technique in the sandbox report summaries. Howevering of techniques will show select metadata.
Download
Copyright (C) 2022 PayloadSecurity