sandmap v1.2.0 release: network and system reconnaissance using the massive Nmap engine
Sandmap is a tool for supporting network and system reconnaissance using the massive Nmap engine. It provides a user-friendly interface, automates and speeds up scanning and allows you to easily use many advanced scanning techniques.
Key Features
- simple CLI with the ability to run pure Nmap engine
- predefined scans included in the modules
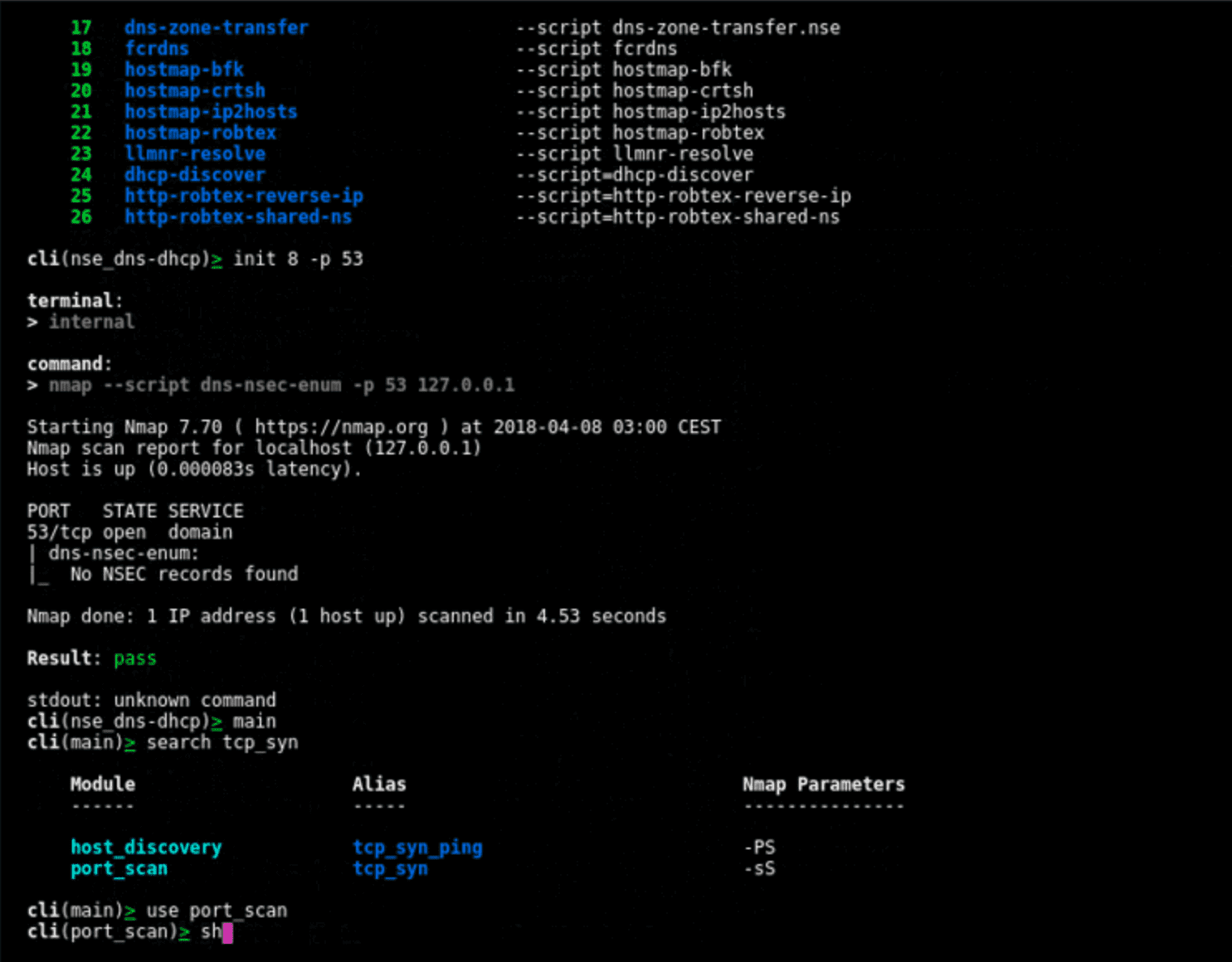
- support Nmap Scripting Engine (NSE) with scripts arguments
- TOR support (with proxychains)
- multiple scans at one time
- at this point: 31 modules with 459 scan profiles
Modules
Available modules: 31
Available scan profiles: 459
Installation
Requirement
git clone https://github.com/trimstray/sandmap
cd sandmap
./setup.sh install
Configuration file
The etc/main.cfg configuration file has the following structure:
Usage
Logging
After running the script, the log/ directory is created and in it the following files with logs:
- <script_name>.<date>.log – all _logger() function calls are saved in it
- stdout.log – a standard output and errors from the _init_cmd() function are written in it. If you want to redirect the output from command, use the following structure: your_command >>”$_log_stdout” 2>&1 &
Copyright (C) trimstray
Source: https://github.com/trimstray/





