ScarCruft Strikes: North Korea’s Cyber Espionage Against Media and Experts Unveiled
In the intricate web of global cyber espionage, the activities of state-sponsored Advanced Persistent Threat (APT) groups like ScarCruft, a suspected North Korean entity, stand out for their precision and strategic focus. Recently, SentinelLabs, in collaboration with NK News, has unraveled a campaign orchestrated by ScarCruft targeting media organizations and experts on North Korean affairs. This operation, characterized by persistence and sophistication, reflects the nuanced power play in cyber warfare.
Over two months, SentinelLabs observed ScarCruft persistently targeting the same individuals, offering a glimpse into the APT’s dedication and resourcefulness. This targeting involved experts from South Korea’s academic sector and a news organization specializing in North Korean affairs. The precise nature of these attacks points to ScarCruft’s strategic objectives: gathering intelligence and influencing perceptions.

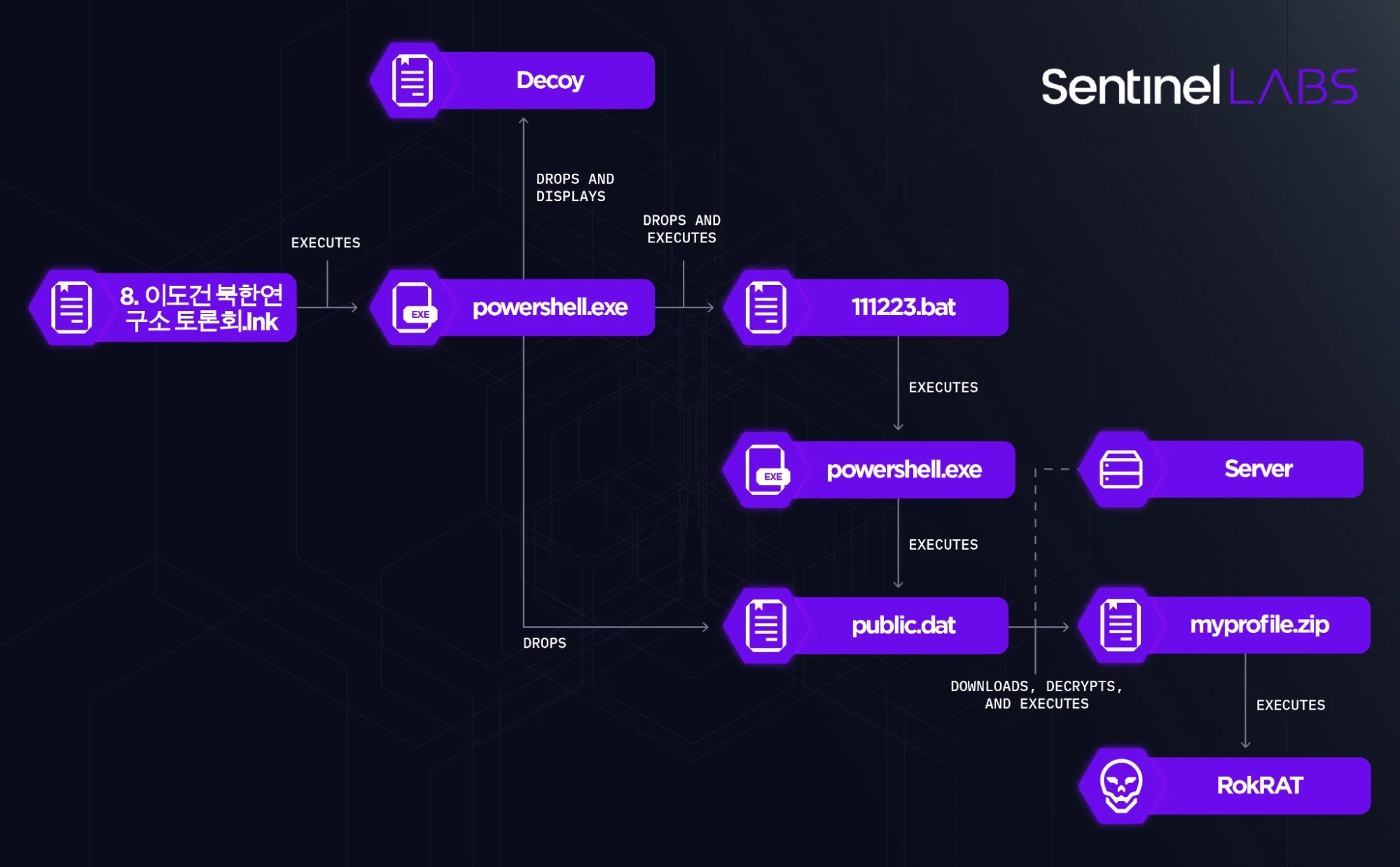
Infection chain
ScarCruft, also known as APT37 and InkySquid, wields a variety of tools and methods in its arsenal. This campaign featured the use of a custom-written backdoor, RokRAT, a fully-featured surveillance tool capable of conducting effective espionage on targeted entities. The group’s infection chains involve multi-stage mechanisms and multiple executable formats, employing evasion techniques to remain undetected.
The primary goal of ScarCruft’s targeting high-profile experts and news organizations is to gather strategic intelligence. This information provides the adversary with insights into the international community’s perceptions of North Korea, feeding into the decision-making processes of the secretive state. By focusing on consumers of technical threat intelligence reports, ScarCruft aims to gain insights into non-public cyber threat intelligence and defense strategies.
One of the most intriguing aspects of ScarCruft’s operations is the use of decoy documents relevant to targeted individuals, signifying a blend of technical sophistication and psychological manipulation. For instance, they use a technical threat research report on Kimsuky, another suspected North Korean threat group, as a decoy document, exhibiting their deep understanding of their targets’ interests and activities.
As SentinelLabs continues to track ScarCruft and other suspected North Korean threat actors, it becomes evident that these groups are increasingly focusing on mimicking cybersecurity professionals and businesses. This strategic shift is indicative of their intent to refine operational and evasive approaches, broadening their targeting spectrum.
The revelation of ScarCruft’s latest campaign serves as a stark reminder of the evolving nature of cyber threats, especially from state-sponsored actors. Understanding the adversary’s attack and infection methods is crucial for effective defense.





