The Rust infostealer attack
Sophos X-Ops has spotlighted a concerning trend in the exploitation of vulnerabilities within ConnectWise ScreenConnect installations, a widely used remote monitoring and management software. The recently disclosed vulnerabilities in ScreenConnect (CVE-2024-1709, CVE-2024-1708) necessitate immediate action. Widespread exploitation targeting on-premises installations calls for swift patching, proactive threat hunting, and enhanced network defenses.
On February 19, 2024, ConnectWise sounded the alarm on two critical vulnerabilities affecting older versions of its ScreenConnect software. These vulnerabilities, if left unpatched, could grant attackers the capability to execute remote code or access confidential data. Designated as CVE-2024-1709 and CVE-2024-1708, these flaws involve authentication bypass and path traversal issues within the server software, posing a severe threat to organizations using the affected software versions.
- CVE-2024-1709: An authentication bypass using an alternate path or channel, earning a base CVSS score of 10, signaling a critical threat level.
- CVE-2024-1708: An improper limitation of a pathname to a restricted directory (“Path Traversal”), with a base CVSS score of 8.4, classified as a high priority.

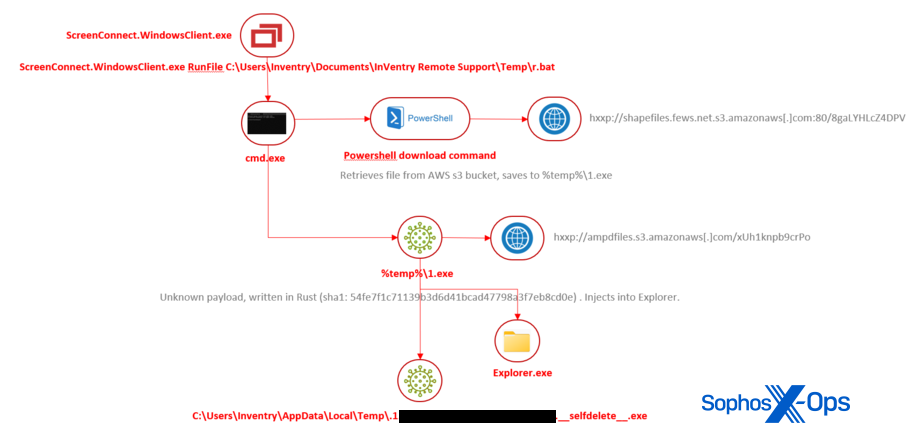
Sophos has confirmed that attackers have been actively exploiting them to deploy malware on both servers and client machines running ScreenConnect. This highlights the urgent need for affected organizations to patch their installations or face potentially devastating consequences.
Sophos X-Ops has observed several attacks leveraging these vulnerabilities, including the deployment of LockBit ransomware via a leaked malware builder tool. These attacks underscore the vulnerabilities’ severity and the sophistication of threat actors seeking to exploit them. In addition to ransomware, attackers have utilized ScreenConnect vulnerabilities to deliver a range of malware, including AsyncRAT and various data stealers.
In response to these vulnerabilities, ConnectWise has issued patches for ScreenConnect, recommending that all users upgrade to version 23.9.8 or later. For those unable to upgrade immediately, an interim version (22.4) is available, which addresses the critical CVE-2024-1709 vulnerability. However, this is only a temporary solution, and a full upgrade is strongly advised to ensure comprehensive protection.