Seccubus v2.53.1 releases: automated vulnerability scanning, reporting and analysis
Seccubus

Image: avleonov
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on repeated scans.
On repeated scan delta reporting ensures that findings only need to be judged when they first appear in the scan results or when their output changes.
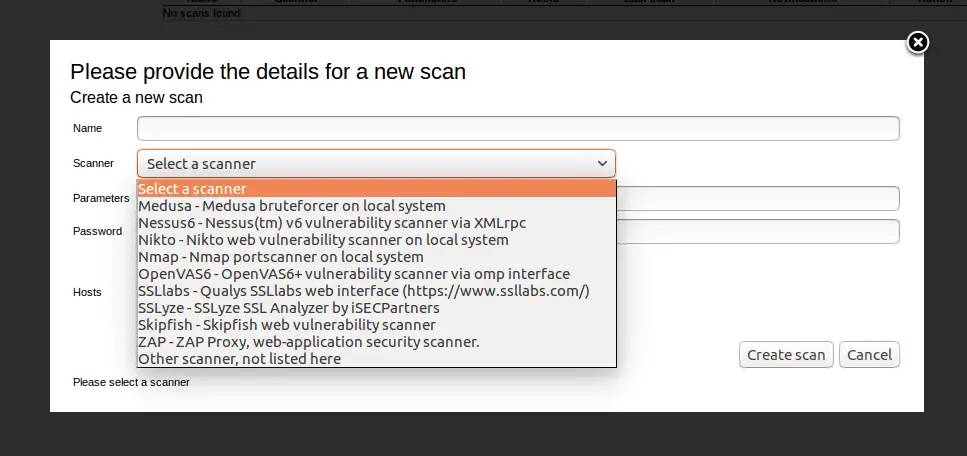
Seccubus V2 works with the following scanners:
- Nessus
- OpenVAS
- Skipfish
- Medusa (local and remote)
- Nikto (local and remote)
- NMap (local and remote)
- OWASP-ZAP (local and remote)
- SSLyze
- Medusa
- Qualys SSL labs
- testssl.sh (local and remote)
It runs vulnerability scans at regular intervals and compares the findings of the last scan with the findings of the previous scan. The delta of this scan is presented in a web GUI where findings can be easily marked as either real findings or non-issues. Non-issues get ignored until they change. This causes a dramatic reduction in analysis time. Before the results of a vulnerability scan are imported into Seccubus they are first converted to the Intermediate Vulnerability Information Language (IVIL) format to make sure Seccubus can work with many different scanners.
Changelog
v2.52
Enhancements
- Integration tests (testssl.sh and ssllabs) now only run when commits are merged into master
- Switched from mysql-server to mariadb-server as a dependancy on Debian based systems
- Online version check is now served from the main seccubus.com website
Bug Fixes
- #678 – Works on Mojolicious 8 again
- #680 – RPMs are now signed again
- #685 – Test 54 did not initialize DB before test start
- #686 – New key staplingRevocationStatus added to ssllabs scanner
- #688 – RPM now requires openssl so fresh installs on EL listen on https too
Lead developer and original author: Frank Breedijk





