Image: Inde
Security researcher Chris Campbell at Inde has provided an in-depth analysis of SectopRAT, a Remote Access Trojan (RAT) that has been active since early 2019. This malware, built on the .NET framework, is known for its evasive techniques and extensive capabilities for data exfiltration.
SectopRAT employs a range of sophisticated techniques to avoid detection and carry out its malicious activities. According to the analysis, “The malware implements robust anti-analysis features, including anti-VM and anti-emulator functionalities, while securing command and control communications with AES-256 encryption.”
One of SectopRAT’s distinguishing features is its ability to establish concealed secondary desktops, enabling threat actors to remotely manipulate browser sessions without the victim’s knowledge.
SectopRAT is commonly distributed through malvertising campaigns, including ads on major platforms like Google and Bing, and drive-by downloads of illegitimate software.
The report details a specific infection scenario that begins with users being drawn to a site through Google search results or a YouTube channel. The infection chain involves a multi-step process:
- Initial Redirect: A script is requested from an off-site URL, which then redirects to an R2 bucket serving heavily obfuscated JavaScript.
- Obfuscation and Deception: The JavaScript is heavily obfuscated to hinder analysis, using techniques that require tools like Obfuscator.io Deobfuscator and assistance from language models to decipher.
- Cloudflare Impersonation: A DOM overlay is constructed to mimic Cloudflare’s styling, creating a fake verification process.
- Social Engineering: The script uses local storage to track interaction count and, after a couple of attempts, presents a lure message claiming unusual web traffic has been detected.
- Malicious Command Execution: Users are instructed to copy and paste a “verification code” into a run box, which actually contains a base64 encoded command. This command, when executed, downloads and runs an MSI package.
The downloaded MSI package employs techniques seen in other malware like Qakbot, using SrTasks to create a system restore point for persistence. The MSI drops several files, including “hello.exe” and “icuin40.dll” in the user’s AppData\Local\Beam\ directory.
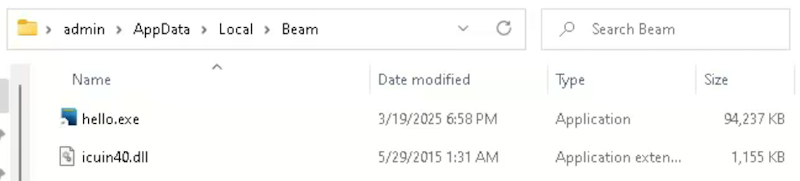
“Hello.exe” undergoes multiple unpacking stages before creating “LightingService.exe” in the user’s Roaming profile, which is then set to run at startup for persistence. This “LightingService.exe” acts as the loader for the SectopRAT payload.
SectopRAT, once loaded, exhibits a wide range of malicious capabilities, primarily focused on data exfiltration. The malware targets various categories of sensitive information, including:
- System information.
- Cookies, saved passwords, history, and autofill data from browsers.
- Cryptocurrency wallets.
- VPN configurations.
The unpacked executable, despite cleanup attempts, has mangled control flow, making analysis challenging. However, researchers can still debug it and derive the RAT’s capabilities through static code review.
The malware also uses an embedded resource containing its encoded configuration. This configuration is decoded using a specific function that employs rolling parameters and bitwise operations.
Researchers have developed scripts to brute-force the encoded configuration values directly from the resource file, using techniques to reduce false positives, such as checking character validity, calculating Shannon entropy, and identifying common string patterns.
SectopRAT uses a hardcoded C2 server and also embeds a Pastebin URL as a backup for C2 servers. The malware uses a “ScanResult” object to collect and prepare data for exfiltration to the C2 server.
SectopRAT may also deploy a browser plugin, typically for Chrome, though its deployment is inconsistent. The plugin, disguised as “Google Docs,” includes a genuine jQuery script but also malicious scripts.
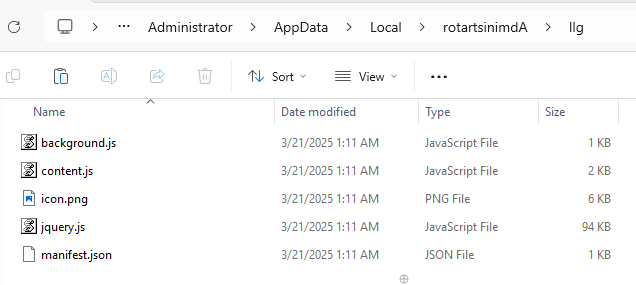
The plugin’s “background.js” implements a CORS bypass, while “content.js” executes on page load to intercept data. It establishes event listeners on form input elements and transmits every form interaction, along with contextual metadata, to the C2 server.
The report notes that variants of SectopRAT have been observed, with changes in the loader. For instance, one variant used an Autolt chain and a different executable with an invalid signature.