SGXRay: Automating Vulnerability Detection for SGX Apps
Intel SGX protects isolated application logic and sensitive data inside an enclave with hardware-based memory encryption. To use such hardware-based security mechanism requires a strict programming model on memory usage, with complex APIs in and out the enclave boundary. Enclave developers are required to apply careful programming practices to ensure enclave security, especially when dealing with data flowing across the enclave’s trusted boundary. Trusted boundary violations can further cause memory corruption and are exploitable by attackers to retrieve and manipulate protected data. Currently, no publicly available tools can effectively detect such issues for real-world enclaves.
It is an open-source tool that automatically detects SGX enclave bugs rooting from violations of trusted boundaries. It recompiles a given enclave code and starts the analysis from a user-specified enclave function entry. SGXRay can also enumerate and analyze all enclave entry functions automatically. The goal of SGXRay is to effectively report enclave vulnerabilities exploitable by an attacker in the untrusted domain and automatically generate test cases accordingly.
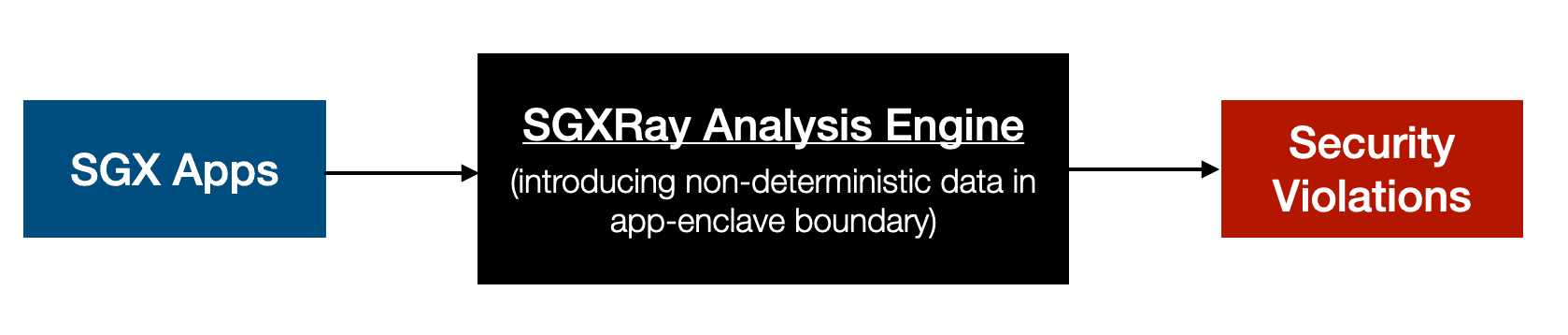
The following figure demonstrates the workflow of SGXRay. The SGXRay analysis engine takes SGX apps and introduces non-deterministic data to the app-enclave boundaries. By analyzing the data/control flows, it outputs positions of potential security violations.