ShadowSpray
A tool to spray Shadow Credentials across an entire domain in hopes of abusing long-forgotten GenericWrite/GenericAll DACLs over other objects in the domain.
Why this tool
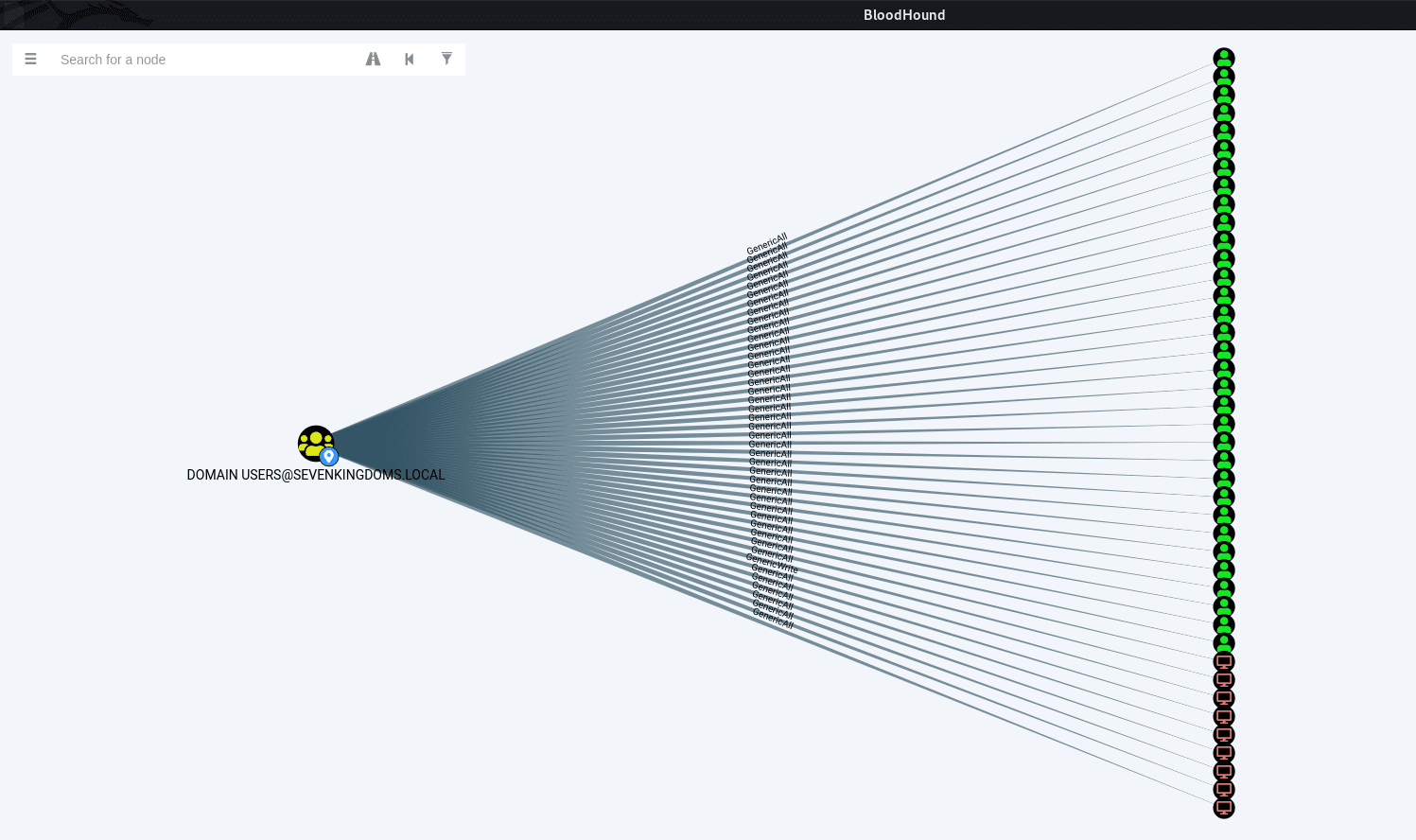
In a lot of engagements, I see (in BloodHound) that the group “Everyone” / “Authenticated Users” / “Domain Users” or some other wide group, which contains almost all the users in the domain, has some GenericWrite/GenericAll DACLs over other objects in the domain.

These rights can be abused to add Shadow Credentials on the target object and obtain its TGT and NT Hash.
It occurred to me that we can just try and spray shadow credentials over the entire domain and see what’s sticks (obviously this approach is better suited to non-stealth engagements, don’t use this in a red team where stealth is required). When a Shadow Credentials is successfully added, we simply do the whole PKINIT + UnPACTheHash dance, and voilà – we get NT Hashes.
Since the process is extremely fast, this can be used at the very start of the engagement, and hopefully, you’ll have some users and computers owned before you even start.
How this tool works
It goes something like this:
- Login to the domain with the supplied credentials (Or use the current session).
- Check that the domain functional level is 2016 (Otherwise stop since the Shadow Credentials attack won’t work)
- Gather a list of all the objects in the domain (users and computers) from LDAP.
- For every object in the list do the following:
- Try to add KeyCredential to the object’s “msDS-KeyCredentialLink” attribute.
- If the above is successful, use PKINIT to request a TGT using the added KeyCredential.
- If the above is successful, perform an UnPACTheHash attack to reveal the user/computer NT hash.
- If –RestoreShadowCred was specified: Remove the added KeyCredential (clean up after yourself…)
- If –Recursive was specified: Do the same process using each of the user/computer accounts we successfully owned.
ShadowSpray supports CTRL+C so if at any point you wish to stop the execution just hit CTRL+C and ShadowSpray will display the NT Hashes recovered so far before exiting.