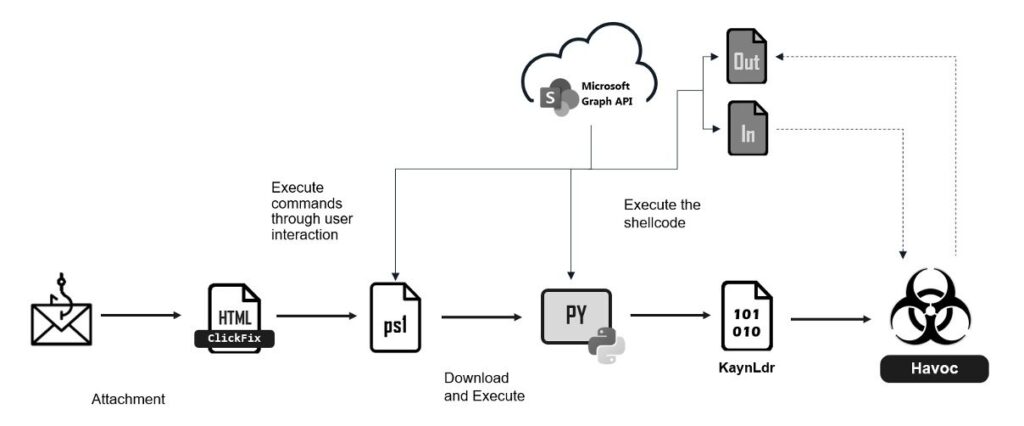
Attack flow | Source: FortiGuard Labs
A recent report from FortiGuard Labs has shed light on an advanced cyber campaign leveraging the open-source Havoc command-and-control (C2) framework to execute fully undetectable (FUD) malware operations. The attackers employ Microsoft Graph API and SharePoint services to discreetly communicate with infected machines, effectively masking malicious activities within legitimate services.
Havoc is a powerful C2 framework akin to Cobalt Strike, Silver, and Winos4.0, widely utilized by adversaries to gain full control over compromised systems. As an open-source tool available on GitHub, it has been modified by threat actors to evade detection. FortiGuard Labs has identified a phishing campaign that deploys a customized Havoc Demon agent, which utilizes SharePoint and Microsoft Graph API to establish resilient C2 channels.
The attack starts with a phishing email containing an HTML attachment, Documents.html, which employs ClickFix social engineering techniques to deceive users. The HTML file mimics an error message, coercing victims into copying and pasting a malicious PowerShell command into their terminals:
This command downloads a remote PowerShell script hosted on SharePoint, which executes a multi-stage attack:
- Evades sandbox detection by checking the number of domain computers.
- Deletes registry entries under HKCU:\Software\Microsoft with specific markers.
- Downloads and executes a Python-based shellcode loader.
The Python script, also hosted on SharePoint, contains debug messages in Russian, indicating its possible origin. Once executed, the script loads shellcode and runs Havoc’s KaynLdr shellcode loader, which leverages API hashing and reflective DLL injection to execute the malware.
One of the most sophisticated aspects of this campaign is its use of Microsoft Graph API for stealthy C2 communications. The attackers initialize SharePointC2Init, which utilizes the Microsoft Identity Platform to obtain access tokens and create files in SharePoint’s document library:
- {VictimID}pD9-tKout: Stores C2 commands.
- {VictimID}pD9-tKin: Stores malware responses.
The infected machine retrieves instructions via TransportSend, which accesses the {VictimID}pD9-tKout file using Graph API GET requests. If valid commands are found, they are decrypted and executed. The response is then uploaded to {VictimID}pD9-tKin, and after processing, the contents are immediately erased to avoid forensic detection.
All communications are AES-256 encrypted in CTR mode, ensuring that network-based detection tools struggle to identify anomalies.
The Havoc-SharePoint C2 campaign highlights the increasing trend of cloud service abuse for malware operations. As organizations move towards cloud-based infrastructure, adversaries follow suit, embedding malicious C2 frameworks within trusted enterprise services to evade detection.
Related Posts:
- Warning: Fully Undetectable (FUD) Links Exploit Trust in Cloud Giants
- Microsoft’s September Patch Tuesday: A Patchwork of Urgency with 4 Zero-Days Under Attack
- CVE-2024-38094 Exploited: Attackers Gain Domain Access via Microsoft SharePoint Server