DotStealer malware sample
A new menace has been detected by security researcher @Yogesh Londhe: the DotStealer malware. This sophisticated piece of cyber weaponry, analyzed by K7 Computing, has showcased its prowess in espionage by pilfering user information with alarming precision.
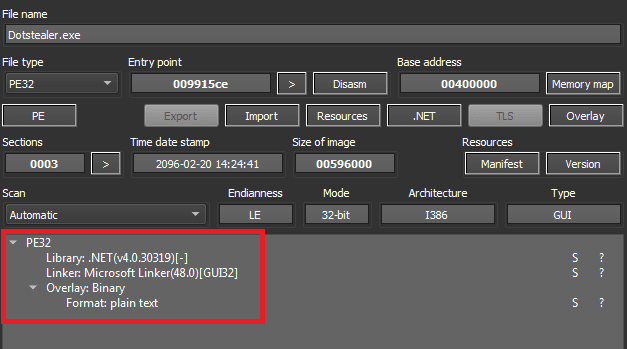
DotStealer, masquerading within the binary veil of a 32-bit executable, crafts its lair directly on the user’s system, only to unleash its malicious intent by capturing user login and credit card details, alongside a comprehensive sweep of system information.

Armed with the ability to disguise itself within your system, DotStealer first identifies the user’s username, creating a clandestine directory to conceal its presence. Employing the Rot13 algorithm, it then decrypts Telegram credentials, granting access to a conduit for data exfiltration.
DotStealer is not content to simply plunder your data—it seeks to evade detection at every turn. Employing sophisticated techniques, it scans for signs of a controlled environment, promptly aborting its mission if suspicions arise. Through blacklist checks and meticulous analysis, DotStealer evades scrutiny with calculated precision.
But perhaps most chilling of all is DotStealer’s ability to cover its tracks, leaving behind no trace of its nefarious activities. By creating a batch file and running using a command prompt, it obfuscates its presence, ensuring that the user “cannot find the original malware file.”
Employing the stealth of Telegram for data exfiltration, this malware introduces a novel vector of attack through social media platforms. With an arsenal equipped to decrypt communication tokens and a cunning strategy to self-replicate, DotStealer navigates the cyber terrain undetected, leaving a trail of digital breadcrumbs leading back to its command and control overseers.
“With the increasing risk of malware attacks, it’s important to take steps to protect your data,” the researcher warns.