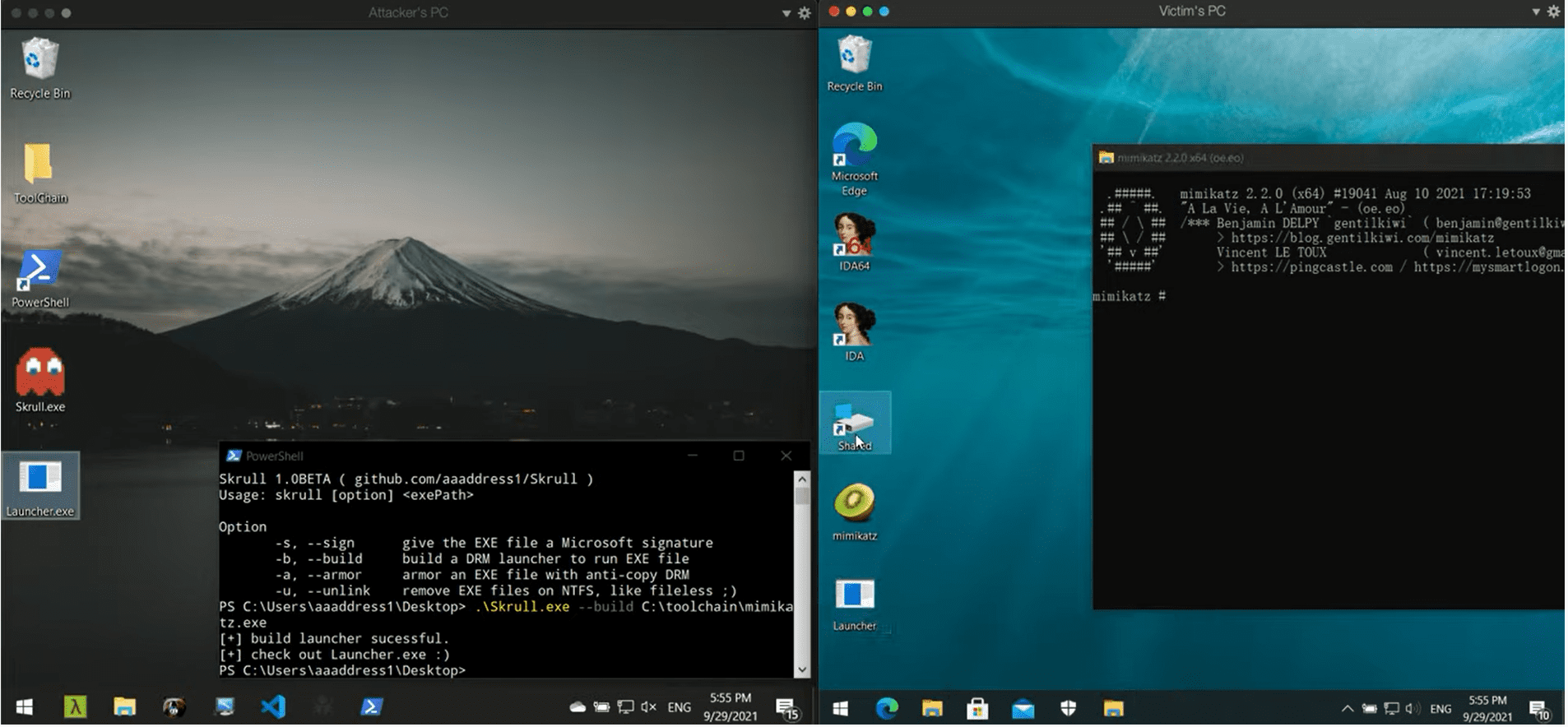
Skrull
There is a well-known feature by which anti-virus or EDR can capture ambiguous or suspicious program files and send them back to security response center for researcher analysis. For malware designers, playing cat and mouse with security solutions in the post exploitation stage while hiding their backdoors from malware detection and forensics is a crucial mental challenge.
Many methods used in the wild by hackers against researchers have already been discussed, for example using a COM hijack to obscure their malware, deploying a kernel hook-based rootkit, bypassing signature-based scanning, and others besides. There’s still no method robust enough to counter these techniques, as researchers often cannot totally understand how the malware works internally even if it’s caught and analyzed.
Imagine a situation: malware acquires DRM protection, and thereby naturally damages itself when copied from the infected machine. Is it possible? How would it happen? In short, security vendors should be prepared to handle this situation within the Maginot line of their own defenses.

Skrull is a malware DRM, that prevents Automatic Sample Submission by AV/EDR and Signature Scanning from Kernel. It generates launchers that can run malware on the victim using the Process Ghosting technique. Also, launchers are totally anti-copy and naturally broken when got submitted.
Download
Demo
Copyright (C) 2021 Sheng-Hao Ma