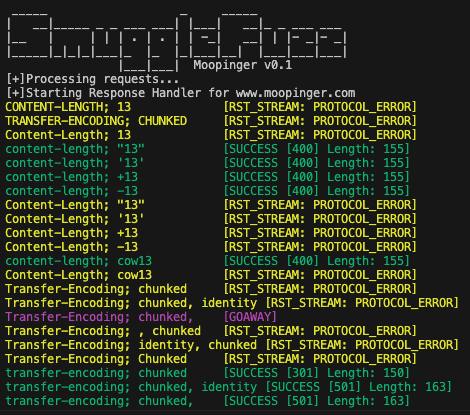
SmuggleFuzz
SmuggleFuzz is designed to assist in identifying HTTP downgrade attack vectors. Its standout feature is not just the time-based detection or request handling, but the detailed response information it provides. This empowers users to define their detection methods, including monitoring HTTP status codes and response sizes. It also handles RST_STREAM frames, including error codes to better pinpoint successful HTTP Smuggling requests or identify failed attacks. SmuggleFuzz adeptly manages GOAWAY frames and establishes new TCP connections without disrupting existing streams. Custom timeout values for confirmation requests can also be set by users.

Wordlist
SmuggleFuzz allows users complete control over requests through custom wordlists. These lists have a basic structure, which should be followed for optimal request handling. For instance, headers and their values are split using a semicolon and a space (; ) instead of the usual colon, facilitating the inclusion of colon values in smuggling requests. This also opens up possibilities for various mutations and creative approaches. For detailed guidance on creating your payloads, refer to PortSwigger’s HTTP/2 Research.
The tool includes a ready-to-use list of 125 smuggling gadgets, though there’s always scope for expansion. These gadgets can be displayed using the ‘output’ command, providing insights into query structuring. Users can run scans with custom wordlists using the ‘w’ flag. The list supports URL encoding (%00) for non-printable byte values, such as carriage return and line feed represented as ‘%0d%0a’ or ‘\r\n’. While the provided list is comprehensive, crafting your gadgets can significantly enhance success rates.
Install & Use
Copyright (c) 2024 Charlie Smith