spring4shell scan
A fully automated, reliable, and accurate scanner for finding Spring4Shell and Spring Cloud RCE vulnerabilities.
The Spring4Shell RCE is a critical vulnerability that FullHunt has been researching since it was released. We worked with our customers in scanning their environments for Spring4Shell and Spring Cloud RCE vulnerabilities.
We’re open-sourcing an open detection scanning tool for discovering Spring4Shell (CVE-2022-22965) and Spring Cloud RCE (CVE-2022-22963) vulnerabilities. This shall be used by security teams to scan their infrastructure, as well as test for WAF bypasses that can result in achieving successful exploitation of the organization’s environment.

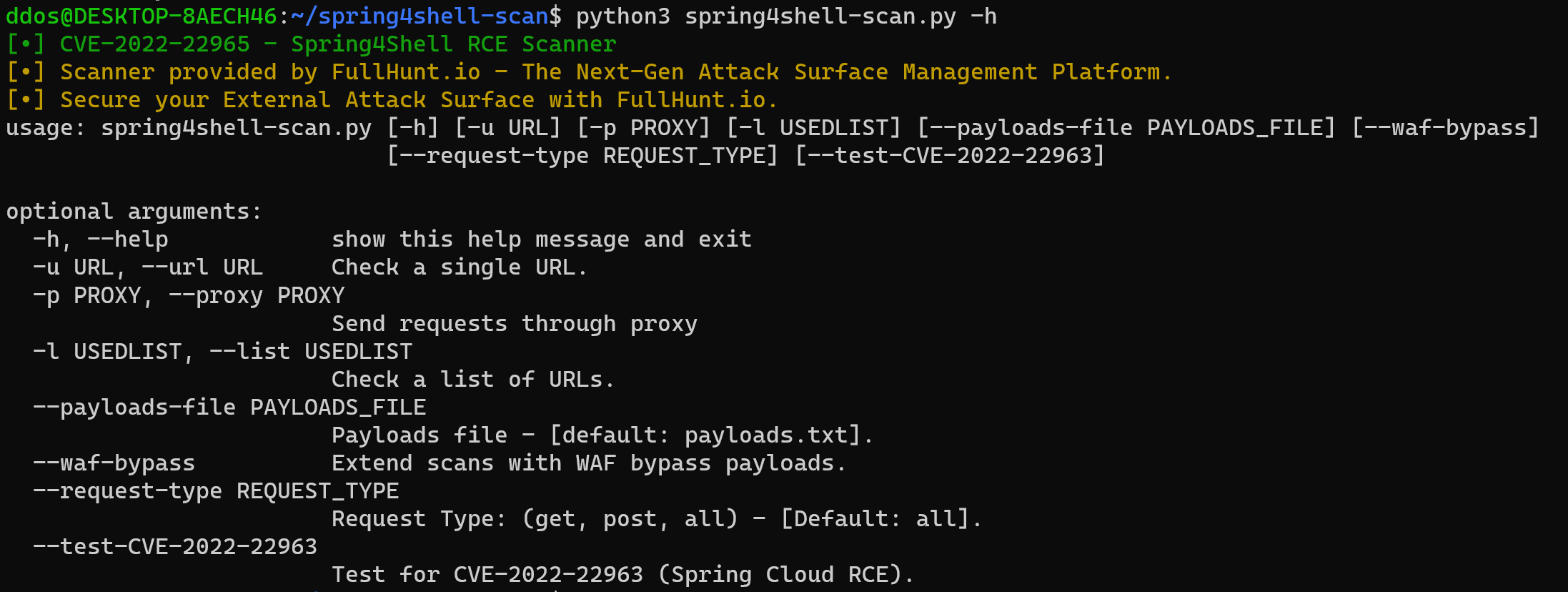
Features
- Support for lists of URLs.
- Fuzzing for more than 10 new Spring4Shell payloads (previously seen tools uses only 1-2 variants).
- Fuzzing for HTTP GET and POST methods.
- Automatic validation of the vulnerability upon discovery.
- Randomized and non-intrusive payloads.
- WAF Bypass payloads.
Install
git clone https://github.com/fullhunt/spring4shell-scan.git
cd spring4shell-scan
pip3 install -r requirements.txt
Use
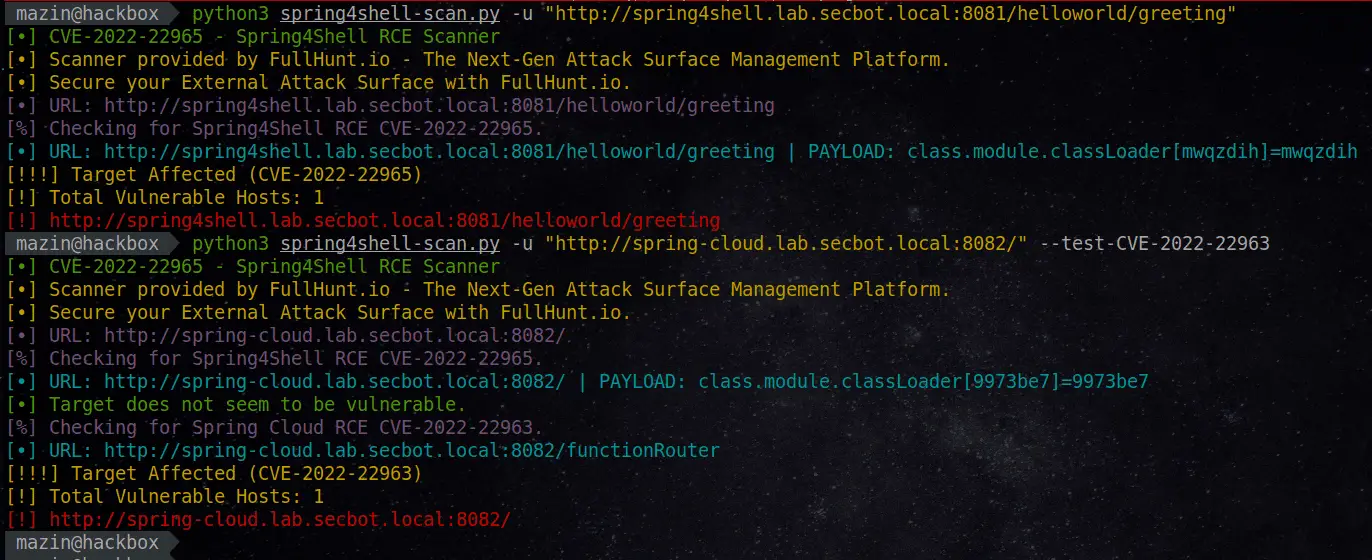
Scan a Single URL
$ python3 spring4shell-scan.py -u https://spring4shell.lab.secbot.local
Discover WAF bypasses against the environment
$ python3 spring4shell-scan.py -u https://spring4shell.lab.secbot.local --waf-bypass
Scan a list of URLs
$ python3 spring4shell-scan.py -l urls.txt
$ python3 spring4shell-scan.py -l urls.txt --test-CVE-2022-22963
Copyright (C) 2022 Mazin Ahmed
Source: https://github.com/fullhunt/