spyse.py
Python API wrapper and command-line client for the tools hosted on spyse.com.
“Spyse is a developer of complete DAAS (Data-As-A-Service) solutions for Internet security professionals, corporate and remote system administrators, SSL / TLS encryption certificate providers, data centers and business analysts. All Spyse online solutions are represented by thematic services that have a single platform for collecting, processing, and aggregating information.” – spyse.com
Supports the following APIs:
Install
pip3 install spyse.py
Use
Spyse allows you to search their database for IPs, IP ranges, domain names, URLs, etc. The parameter argument is meant to specify the type of your input.
As of July 6th, 2019, most of the functions do not require you to set a parameter unless you’d like to override the default one.
For example, the default parameter for –domains-on-ip is ip, however, you can override this parameter and search by CIDR, or organization instead. You should only need to do this if you’re getting an error message, as parameter detection has also been added.
The detection is quite simple:
The detection varies from function to function, as certain functions require different default parameters.
List of parameters
- CIDR
- domain
- ip
- page
- url
- hash
- q
Using search queries
Much like Shodan, Spyse allows you to use search queries.
spyse -target "org: Microsoft" --ssl-certificates
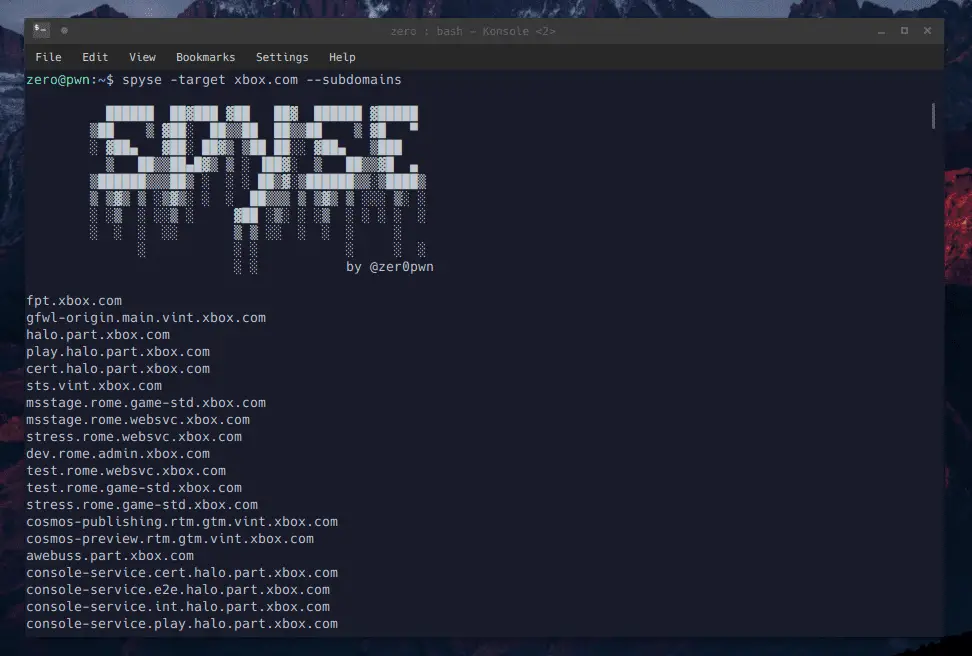
Searching for subdomains
spyse -target xbox.com --subdomains
Reverse IP Lookup
spyse -target 52.14.144.171 --domains-on-ip
Searching for SSL certificates
spyse -target hotmail.com --ssl-certificates
spyse -target "org: Microsoft" --ssl-certificates
Getting all DNS records
spyse -target xbox.com --dns-all
Manually overriding the parameter argument
spyse -target hackerone.com -param domain --subdomains
Navigating multiple pages using your API key
export SPYSEKEY="yourkeyhere"
spyse -target xbox.com -apikey $SPYSEKEY -page 2 ---ssl-certificates
Piping to jq and aquatone
Initially, when I decided to write this client I really wanted it to focus on flexibility within the command-line, which is why there is the –raw option. From there you can work with the raw JSON returned by the API.
spyse -target hackerone.com --dns-soa --raw | jq
spyse -target hackerone.com -param domain --subdomains --raw | aquatone
Copyright (c) 2019 Dominik Penner
Source: https://github.com/zeropwn/