
The BI.ZONE Threat Intelligence team has uncovered a new cyber-espionage campaign attributed to Squid Werewolf, also known as APT37, Ricochet Chollima, ScarCruft, and Reaper Group. The North Korean-aligned threat actor is leveraging fake job offers to lure employees from targeted organizations into opening malicious attachments that lead to remote code execution (RCE) and persistent access.
In December 2024, BI.ZONE researchers discovered a phishing campaign designed to trick victims into opening malicious attachments under the guise of job opportunities at an industrial organization. The attackers posed as recruiters and sent phishing emails containing a password-protected ZIP file named “Предложение о работе.zip” (Job Offer.zip).
According to the report, the phishing document included “recognizable logos and other branding elements to appear more authentic, prompting victims to open them.” Threat actors frequently exploit the credibility of well-known organizations to enhance the success rate of their phishing attempts.
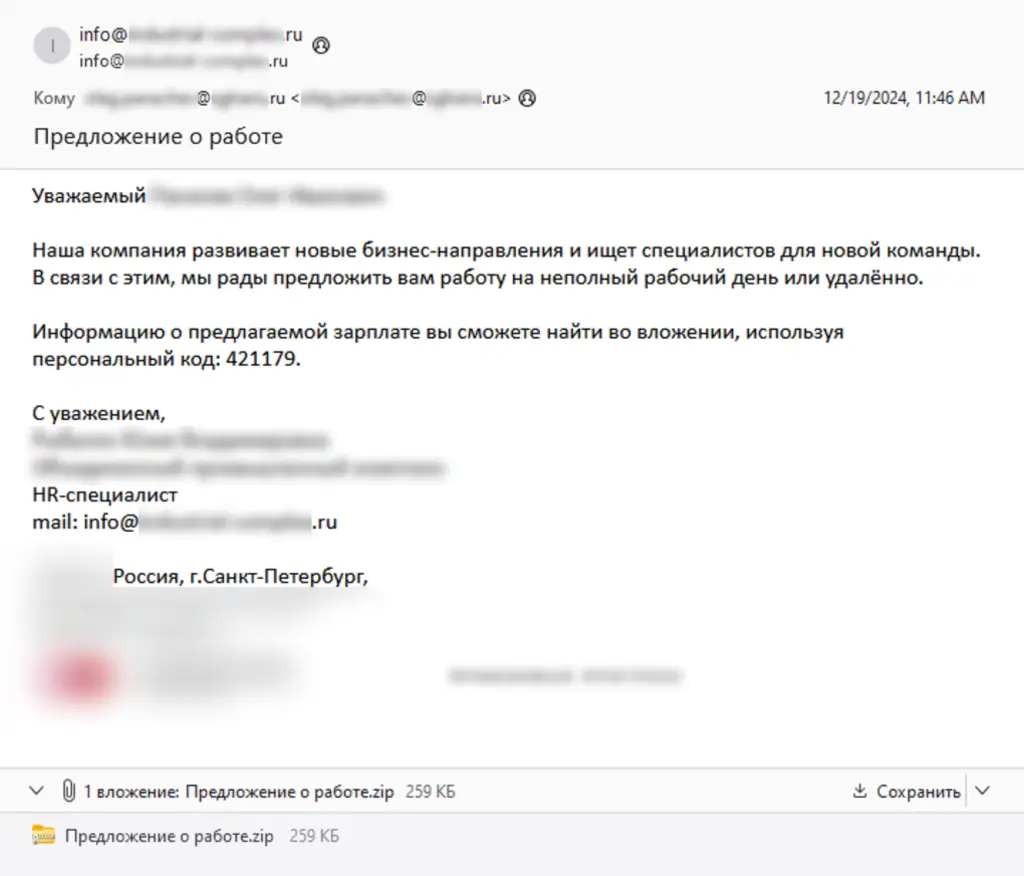
Once the victim extracted and opened the ZIP file, they encountered an LNK shortcut file “Предложение о работе.pdf.lnk”, which triggered a sophisticated infection chain:
-
Execution of Malicious PowerShell Command
The LNK file executed a Base64-encoded PowerShell command, which:- Decoded additional payloads hidden within the file.
- Copied dfsvc.exe (a legitimate Windows binary) to the startup folder as “d.exe” to maintain persistence.
- Saved decoded data into multiple files, including:
- d.exe.config (configuration file for the malware)
- DomainManager.dll (a malicious .NET-based loader)
- mngs Attachement.pdf (a decoy document)
-
Execution of Malicious .NET Loader
The d.exe file, a .NET application, executed the DomainManager.dll loader, which was designed to:- Bypass sandbox detection by performing internet connectivity checks via https://www.timeapi[.]io/api/time/current/zone?timeZone=Europe%2FAmsterdam.
- Establish persistence by modifying Windows registry settings to disable startup autoruns.
- Decrypt and execute additional payloads in memory using AES-128 CBC encryption.
-
Remote Payload Delivery and Execution
If a local configuration file was unavailable, the malware fetched additional payloads from a remote server:- Contacted hxxps://hwsrv-1253398.hostwindsdns[.]com/307c77ab-f41f-4dd4-a478-2a71b9625f64/c/shoppingcart.php.
- Retrieved an AES-encrypted payload, which was decrypted and executed in memory.
- Ensured the payload’s persistence by saving it as DomainManager.conf for future execution.
The BI.ZONE team found similarities between this campaign and a previously documented Squid Werewolf operation analyzed by Securonix. According to the researchers, “The adversaries employed a similar C#-based library in the past,” but previous campaigns used a Caesar cipher for payload decryption instead of AES encryption.
Additionally, past campaigns delivered a PowerShell-based remote access trojan (VeilShell), whereas this latest campaign leverages .NET-based loaders and encrypted payloads to enhance stealth and evade detection.
Related Posts:
- Paper Werewolf: From Espionage to Destruction – A New Threat Emerges
- Sticky Werewolf Targets Aviation Sector in Latest Malicious Campaign
- Denial-of-Service Vulnerability Found in Squid Proxy Server (CVE-2024-45802)
- Security Alert: Squid Proxy’s Unresolved Vulnerabilities