ssh-auditor v0.18 releases: scan for weak ssh passwords
SSH Auditor

Features
ssh-auditor will automatically:
- Re-check all known hosts as new credentials are added. It will only check the new credentials.
- Queue a full credential scan on any new host discovered.
- Queue a full credential scan on any known host whose ssh version or key fingerprint changes.
- Attempt command execution as well as attempt to tunnel a TCP connection.
- Re-check each credential using a per credential scan_interval – default 14 days.
It’s designed so that you can run ssh-auditor discover + ssh-auditor scan from cron every hour to perform a constant audit.
Changelog v0.18
- db27fb8 update goreleaser config
- 4f3bc9b Merge branch ‘store-tweaks’
- e7e23bf Improve updateBruteResult behavior
- 7fce102 remove batch size for scan queue, just scan everything
- 5ae14c5 update go versions
- 139ebf0 fix build command when using go modules
- b152e22 add tests for the batching code
Install
$ go get github.com/ncsa/ssh-auditor
Or
Use
Create an initial database and discover ssh servers
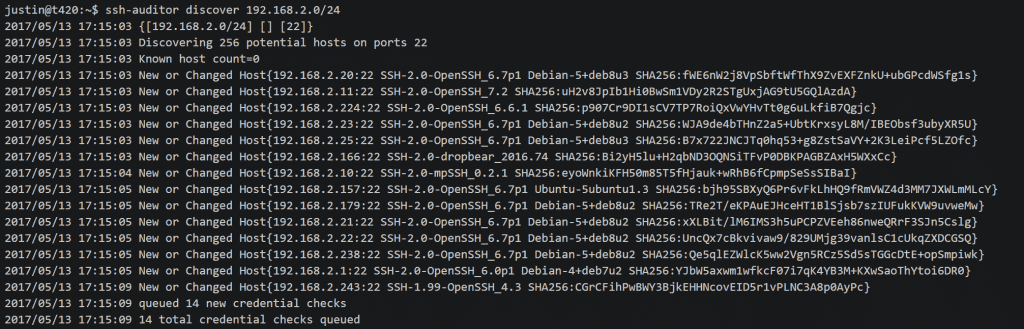
$ ./ssh-auditor discover -p 22 -p 2222 192.168.1.0/24 10.0.0.1/24
Add credential pairs to check
$ ./ssh-auditor addcredential root root $ ./ssh-auditor addcredential admin admin $ ./ssh-auditor addcredential guest guest --scan-interval 1 #check this once per day
Try credentials against discovered hosts in a batch of 20000
$ ./ssh-auditor scan
Output a report on what credentials worked
$ ./ssh-auditor vuln
Report query.
This query that ssh-auditor vuln runs are
RE-Check credentials that worked
$ ./ssh-auditor rescan
Output a report on duplicate key usage
$ ./ssh-auditor dupes
Demo
Copyright (c) 2016 University of Illinois/NCSA
Source: https://github.com/ncsa/