SSH-Snake: Automated SSH-Based Network Traversal
SSH-Snake: Automated SSH-Based Network Traversal
SSH-Snake is a powerful tool designed to perform automatic network traversal using SSH private keys discovered on systems, to create a comprehensive map of a network and its dependencies, identifying to what extent a network can be compromised using SSH and SSH private keys starting from a particular system.
SSH-Snake can automatically reveal the relationship between systems that are connected via SSH, which would normally take a tremendous amount of time and effort to perform manually.
In other words, SSH-Snake performs the following tasks automatically and recursively:
- On the current system, find any SSH private keys,
- On the current system, find any hosts or destinations (
user@host) that the private keys may be accepted, - Attempt to SSH into all of the destinations using all of the private keys discovered,
- If a destination is successfully connected to, repeat steps #1 – #4 on the connected-to system.
It’s completely self-replicating and self-propagating — and completely fileless. In many ways, SSH-Snake is a worm: It replicates itself and spreads itself from one system to another as far as it can.
Instead of manually jumping between systems with SSH keys like it’s a Super Mario game, let SSH-Snake do the work for you.
Although this tool is intended for hacking purposes, sysadmins can also use it to better understand their infrastructure and network. If you want to disable the printing of private keys discovered, comment out this line of code.
For an in-depth look at how this script works, technical details, interesting discoveries, design decisions, benchmarking, and lessons learned, check out this blog post.

SSH-Snake seamlessly emulates what a human adversary would do to discover SSH private keys and destinations where they can be used to connect. Written entirely in Bash, it operates with a minimal set of dependencies commonly available on major Linux systems: bash, ssh, getconf, coreutils, getent, awk, sort, grep, tr, find, and cat. Likewise, sudo, hostname, ip, and xargs may also be used, but they are not required (and the script gracefully handles cases where they are not present). If a system is discovered without any of the required packages, it gracefully fails, alerting the user that the scan could not continue on that particular system (and backtracks, continuing from the previous system.)
SSH-Snake is completely fileless: after the user runs the script, it is passed to destinations’ bash via stdin and bash arguments (via SSH). No material evidence of the script exists on any of the systems scanned: the only evidence of the script running is in the process tree and the substantial amount of invalid SSH attempts that will inevitably occur.
SSH-Snake takes a depth-first approach to discovery: once it connects to one system, it tries to connect further from that system before backtracking.
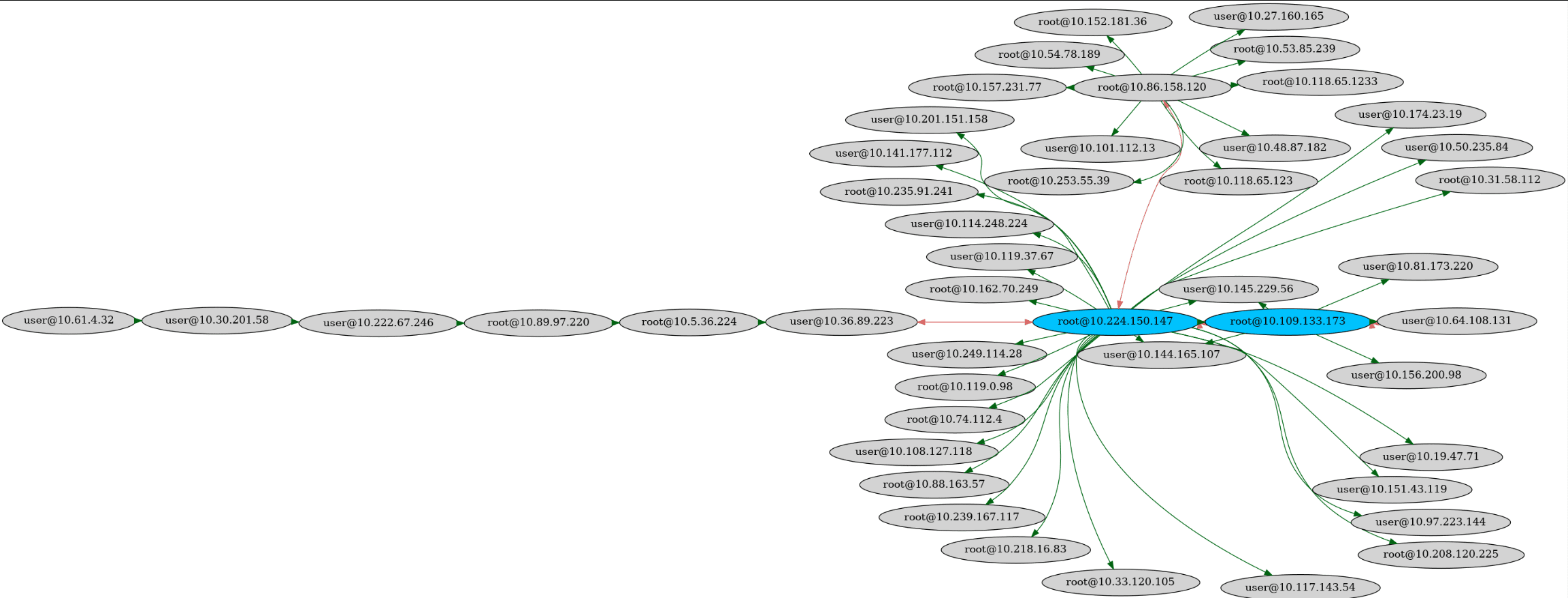
Features
- Recursively SSH from one system to another using local SSH private keys,
- Fileless traversal and propagation/replication of the SSH-Snake script using only stdin and bash arguments to remote systems,
- Automatic elevation of privileges to root using sudo if possible,
- Discover SSH private key files from .bash_history entries,
- Discover SSH private keys from commonly used files and folders,
- Exfiltration of SSH private keys as output of the script,
- Configurable custom command execution on each system,
- Plug-and-play modular system to discover private keys and systems,
- Detect hosts from IP ranges, last logins, known hosts, SSH config files, and more,
- Ability to detect when a system has already been scanned or is in the process of being scanned such that a network like A->B->C can also discover C->A but does not regress to A->B->C-A->B->C->A->B->….,
- Ability to generate graphical visualizations of a network from the output of the script,
- … and more.
Install & Use
Copyright (C) 2024 Joshua Rogers <https://joshua.hu/>





