SSH3: faster and rich secure shell using HTTP/3

SSH3 is a complete revisit of the SSH protocol, mapping its semantics on top of the HTTP mechanisms. In a nutshell, SSH3 uses QUIC+TLS1.3 for secure channel establishment and the HTTP Authorization mechanisms for user authentication. Among others, SSH3 allows the following improvements:
- Significantly faster session establishment
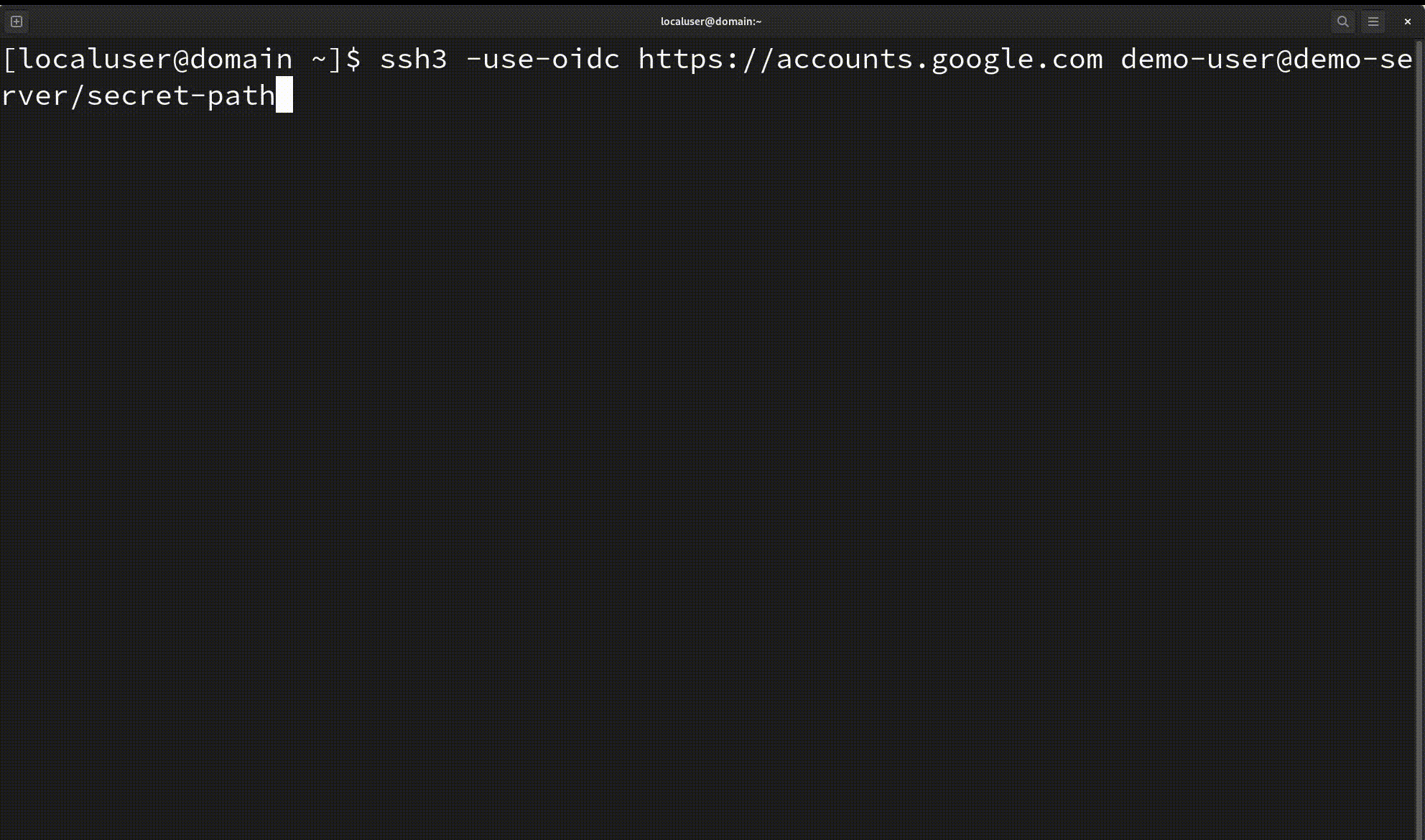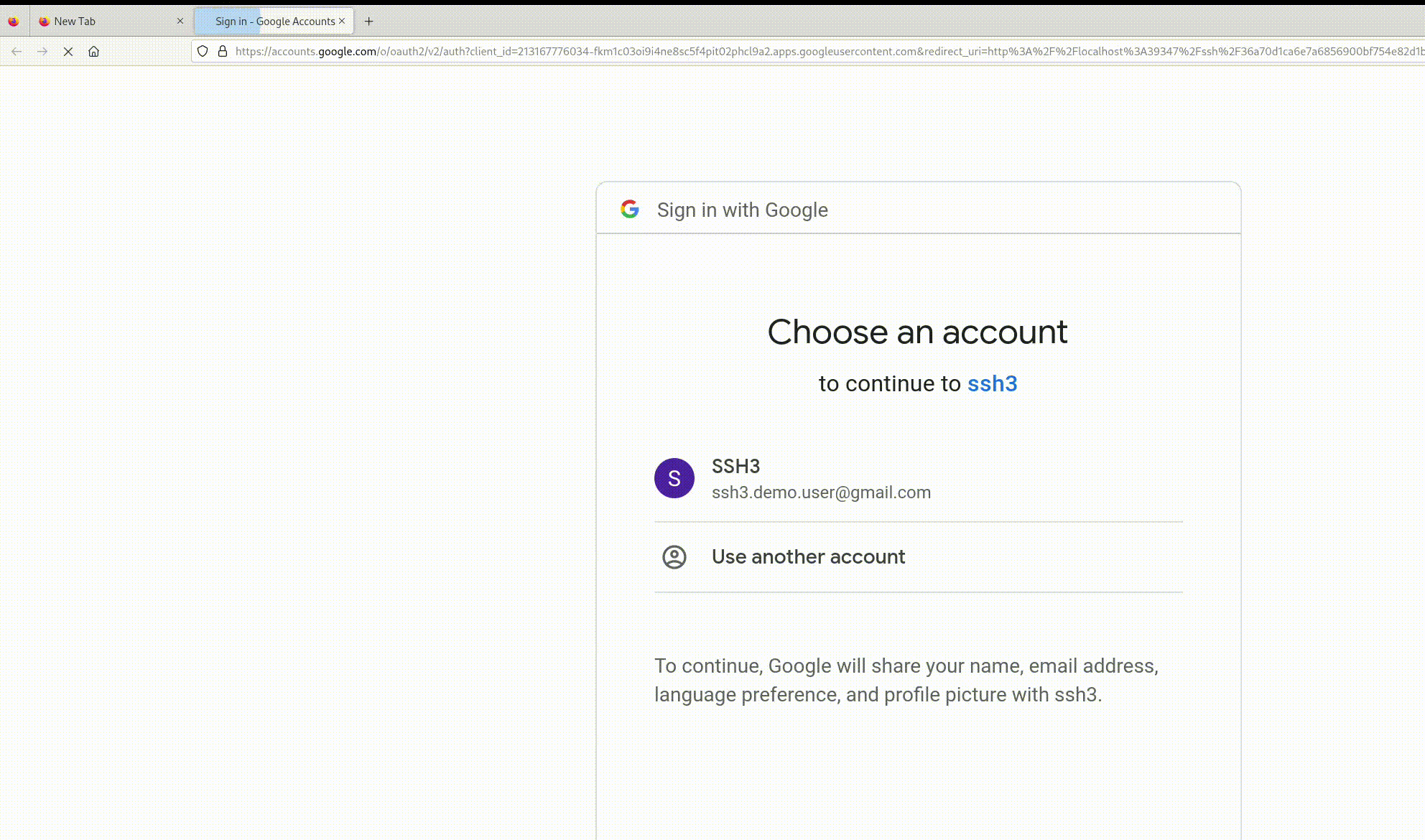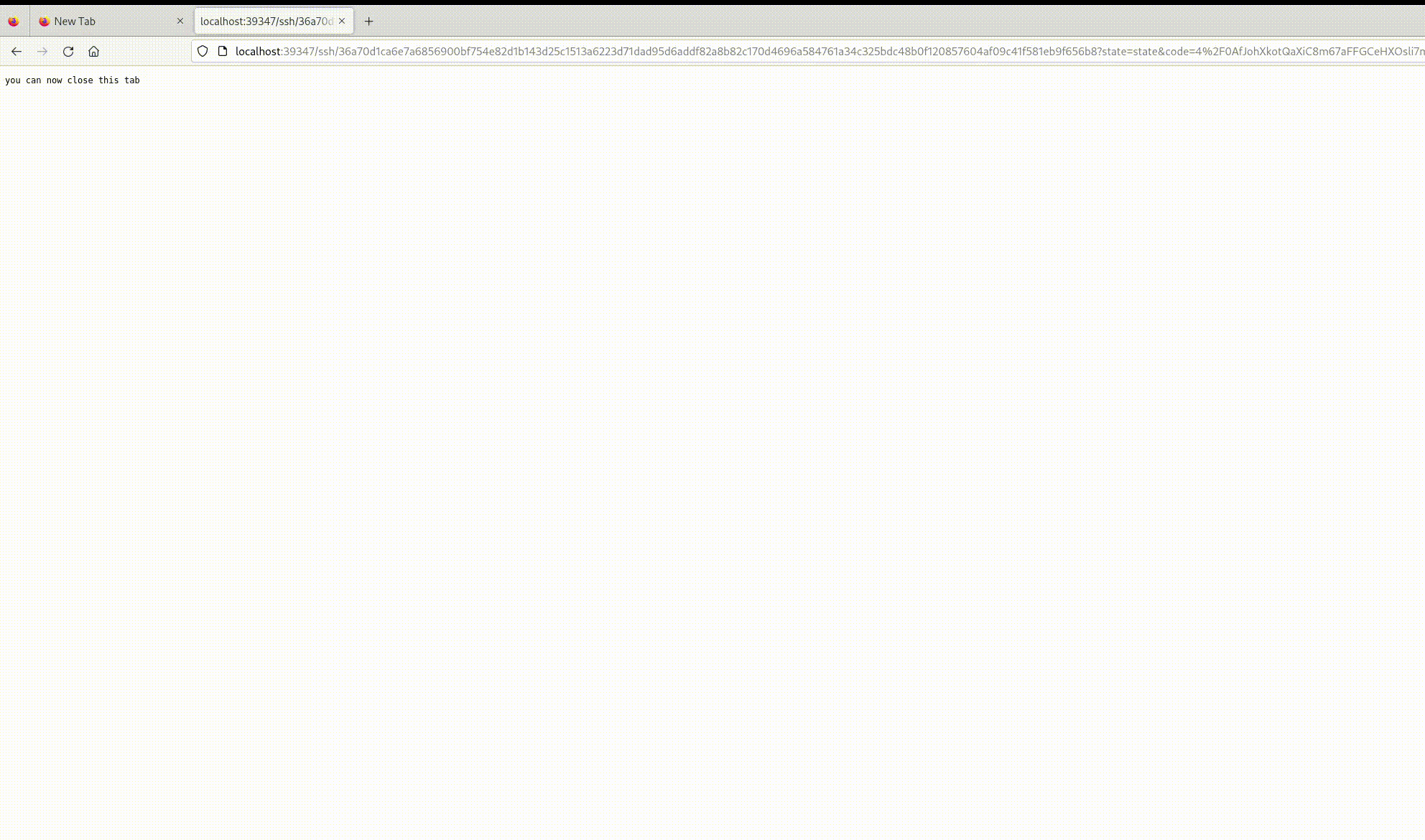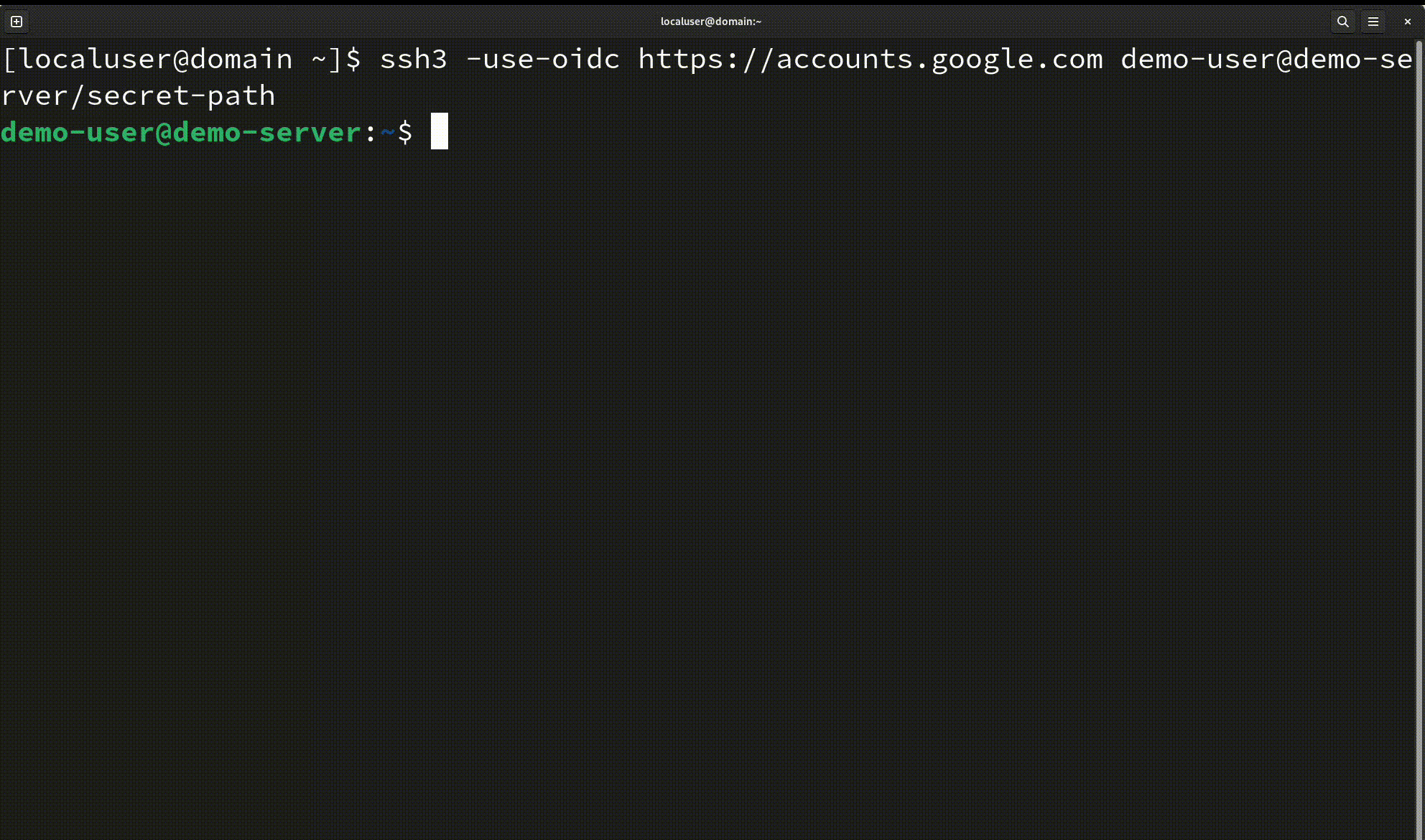
- New HTTP authentication methods such as OAuth 2.0 and OpenID Connect in addition to classical SSH authentication
- Robustness to port scanning attacks: your SSH3 server can be made invisible to other Internet users
- UDP port forwarding in addition to classical TCP port forwarding
- All the features allowed by the modern QUIC protocol: including connection migration (soon) and multipath connections
SSH3 is faster
Faster for session establishment, not throughput! It offers a significantly faster session establishment than SSHv2. Establishing a new session with SSHv2 can take 5 to 7 network round-trip times, which can easily be noticed by the user. SSH3 only needs 3 round-trip times. The keystroke latency in a running session is unchanged.
SSH3 is secure
While SSHv2 defines its protocols for user authentication and secure channel establishment, SSH3 relies on the robust and time-tested mechanisms of TLS 1.3, QUIC, and HTTP. These protocols are already extensively used to secure security-critical applications on the Internet such as e-commerce and Internet banking.
SSH3 already implements the common password-based and public-key (RSA and EdDSA/ed25519) authentication methods. It also supports new authentication methods such as OAuth 2.0 and allows logging in to your servers using your Google/Microsoft/Github accounts.
SSH3 is already feature-rich
It provides a new feature that could not be provided by the SSHv2 protocol.
Brand new features
- UDP port forwarding: you can now access your QUIC, DNS, RTP or any UDP-based server that are only reachable from your SSH3 host. UDP packets are forwarded using QUIC datagrams.
- X.509 certificates: you can now use your classical HTTPS cerificates to authenticate your SSH3 server. This mechanism is more secure than the classical SSHv2 host key mechanism. Certificates can be obtained easily using LetsEncrypt for instance.
- Hiding your server behind a secret link.
- Keyless secure user authentication using OpenID Connect. You can connect to your SSH3 server using the SSO of your company or your Google/Github account, and you don’t need to copy the public keys of your users anymore.
Famous OpenSSH features implemented
This SSH3 implementation already provides many of the popular features of OpenSSH, so if you are used to OpenSSH, the process of adopting SSH3 will be smooth. Here is a list of some OpenSSH features that SSH3 also implements:
- Parses
~/.ssh/authorized_keyson the server - Parses
~/.ssh/configon the client and handles theHostname,User,PortandIdentityFileconfig options (the other options are currently ignored) - Certificate-based server authentication
known_hostsmechanism when X.509 certificates are not used.- Automatically using the
ssh-agentfor public key authentication - SSH agent forwarding to use your local keys on your remote server
- Direct TCP port forwarding (reverse port forwarding will be implemented in the future)
Install
Copyright (C) 2023 Francois Michel