
Image: NVISO
Security researchers from NVISO have uncovered two sophisticated TLS-based backdoors, dubbed SparkCockpit and SparkTar, actively targeting critical-sector organizations using Ivanti Pulse Secure appliances. These backdoors demonstrate a worrying escalation in network appliance attacks, compromising security measures and providing persistent access to attackers.
In early 2024, a widespread attack on Ivanti’s Pulse Secure appliances exploited the known vulnerabilities CVE-2023-46805 and CVE-2024-21887. Amidst this widespread exploitation, two at-the-time undetected covert TLS-based backdoors were unearthed: SparkCockpit and SparkTar.

Both backdoors are masters of disguise, employing selective interception of TLS communication to avoid detection by conventional network-based security solutions. SparkCockpit, birthed from the exploitation of the 2024 Pulse Secure vulnerability, and SparkTar, lurking in the shadows since Q3 2023, offer attackers a suite of nefarious capabilities. From traffic tunneling via SOCKS proxy to enduring persistence through appliance upgrades and factory resets, these backdoors represent a formidable threat to network security.
The architectural sophistication of SparkCockpit and SparkTar is noteworthy. Each backdoor employs a malicious JAR plugin for boot persistence, intercepting TLS handshakes with a finesse that allows them to filter through legitimate communication, thus commandeering the system undetected. SparkCockpit utilizes embedded certificates for completing intercepted TLS handshakes, whereas SparkTar opts for pre-existing on-disk certificates.
SparkCockpit’s lineage can be traced back to an evolution of the Pulse Secure BUSHWALK webshell, analyzed by Mandiant. It offers rudimentary yet effective functionalities such as file uploads/downloads and command execution. Embedded within Ivanti’s Pulse Secure’s client-less browser-based remote access functionality, RemoteSpark, SparkCockpit ensures its persistence through clever manipulation of the SparkGateway server component.
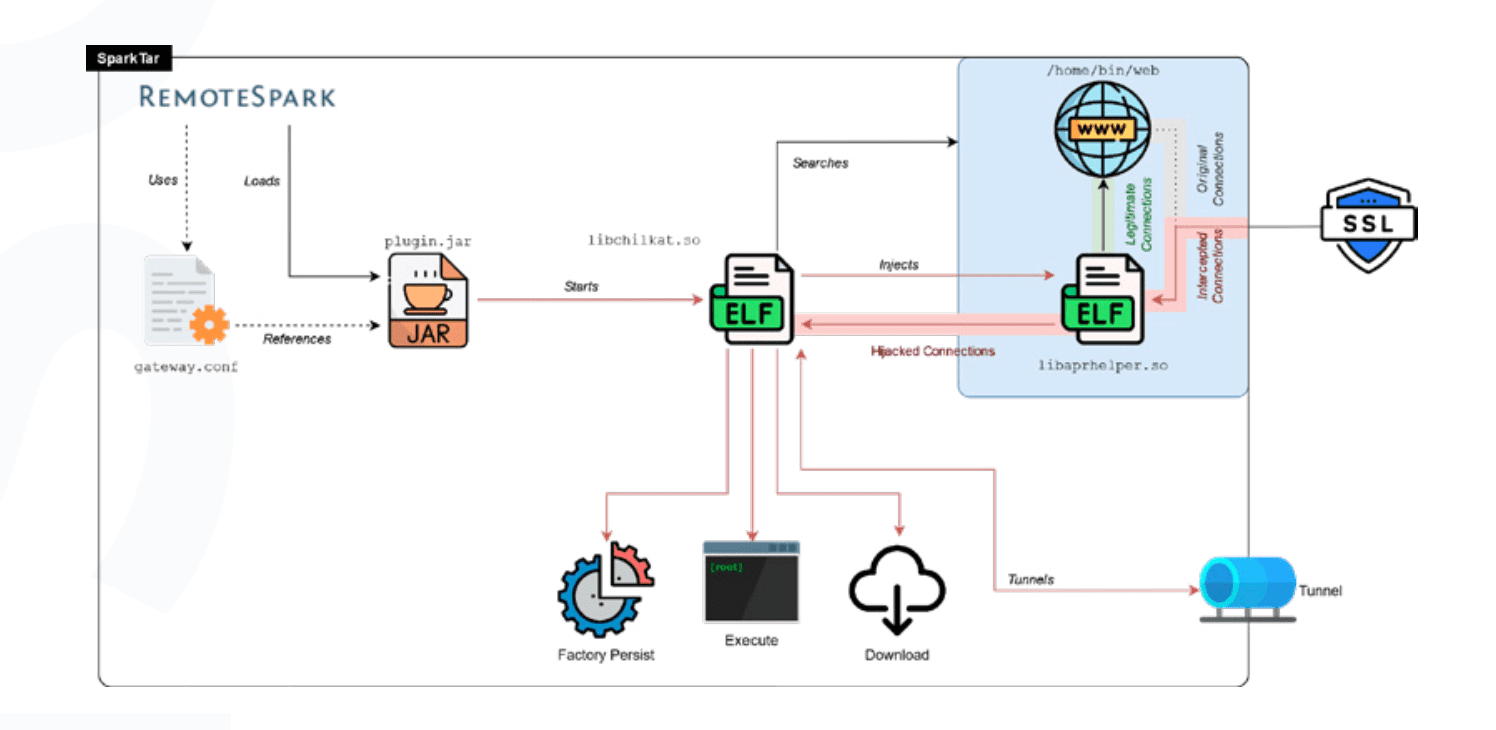
SparkTar stands out for its complexity and versatility, supporting multiple levels of persistence and providing attackers with a realistic shell experience through input/output streaming for commands. Its capability to establish SOCKS proxies for relaying traffic directly into an organization’s network is particularly alarming, indicating a significant leap in backdoor sophistication. It modifies the appliance’s factory reset process itself, ensuring that even after a seemingly clean wipe, it can re-establish itself. It also cleverly patches configuration files to guarantee it reloads upon system restart.
This incident underscores the necessity for organizations to stay abreast of the latest cybersecurity developments, ensuring that their defenses evolve in tandem with the threats they face.