Image: Hossam Ehab
A recent blog by security researcher Hossam Ehab has detailed an advanced technique for process injection through manipulation of the Kernel Callback Table within the Process Environment Block (PEB) on Windows systems. This approach, which provides a stealthy route for code injection and persistence, has been employed by high-profile threat actors like FinFisher and Lazarus. Leveraging this technique, adversaries can redirect a process’s execution flow to malicious payloads, evading detection by running within legitimate processes.
The Process Environment Block, or PEB, is a core Windows structure that acts as a control center, providing vital information about a program’s state and interactions with the operating system. Ehab explains, “The PEB is part of the memory space of the process, and it helps both the operating system and the program manage various internal details.” This includes details about loaded modules, memory management, process start times, and more. It essentially tracks everything the program needs to operate, from its DLL dependencies to its memory allocation and layout.
Within the PEB is the Kernel Callback Table, an array of function pointers populated when user32.dll is loaded into any graphical user interface (GUI) process. This table contains pointers to callback functions that manage window messages and interprocess communication. For example, the __fnCOPYDATA function within this table is triggered by the WM_COPYDATA message, which facilitates data transfer between applications.
Ehab notes, “By understanding the structure and purpose of each function within the Kernel Callback Table, we can comprehend how processes interact and handle various system events.” Recognizing how these function pointers operate is key to understanding the vulnerabilities that adversaries can exploit within the Kernel Callback Table.
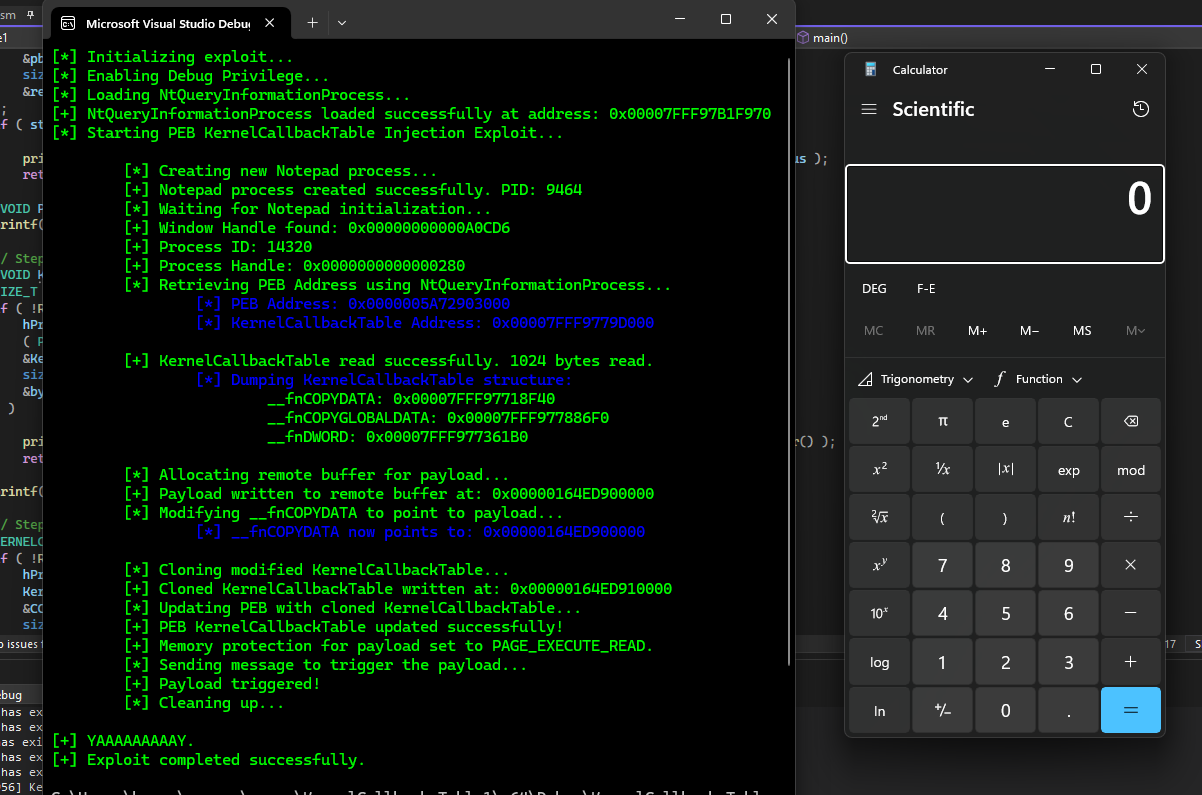
The researcher highlights how attackers can hijack the execution flow by altering the Kernel Callback Table. This table offers a prime target for adversaries seeking to execute code covertly. According to Ehab, “To hijack execution flow using the Kernel Callback Table, an attacker can replace one or more of the original callback function pointers with pointers to malicious code.” This manipulation effectively redirects system events, like WM_COPYDATA, to execute malicious payloads instead of legitimate callbacks.
To accomplish this, attackers often retrieve the PEB address using the NtQueryInformationProcess API call, a low-level Windows function that exposes process internals. By locating the Kernel Callback Table within the PEB, an adversary gains access to modify its function pointers, substituting them with addresses of malicious code. When a specific Windows message triggers these altered callbacks, the injected payload runs within the target process.
One of the most concerning aspects of Kernel Callback Table hijacking is its stealth. As Ehab describes, “Because this manipulation occurs within the target process’s memory, it effectively evades detection by masking the execution of the payload under a legitimate process.” The attacker’s code runs within a valid process, bypassing many security measures.
To enhance stealth, advanced attackers may even restore the Kernel Callback Table to its original state after executing their payload, making it difficult for detection tools to catch the alteration.
For those interested in the technical aspects of this approach, the proof-of-concept exploit code is available on GitHub, allowing security professionals to better understand this complex form of process injection.
Related Posts:
- TikTok Hit by Zero-Day Attack: High-Profile Accounts Compromised
- Iranian APT42 Ramps Up Phishing Campaigns Against Israel, U.S. Election Targets