Security researchers NSG650 and Pdawg have unveiled a proof-of-concept UEFI bootkit that exploits a critical firmware function to compromise the Windows kernel during the boot process. This bootkit demonstrates the continued evolution of malware targeting the Unified Extensible Firmware Interface (UEFI), underscoring the increasing sophistication of threats aimed at pre-operating system environments.
Bootkits are a subset of malware designed to infect systems during the earliest stages of booting, typically before the operating system’s kernel is loaded. As the researchers explain, “Bootkits are inherently subtle, making them very difficult to detect and by effect making it much harder for anti-virus software to detect them or what changes they might have made to the system.”
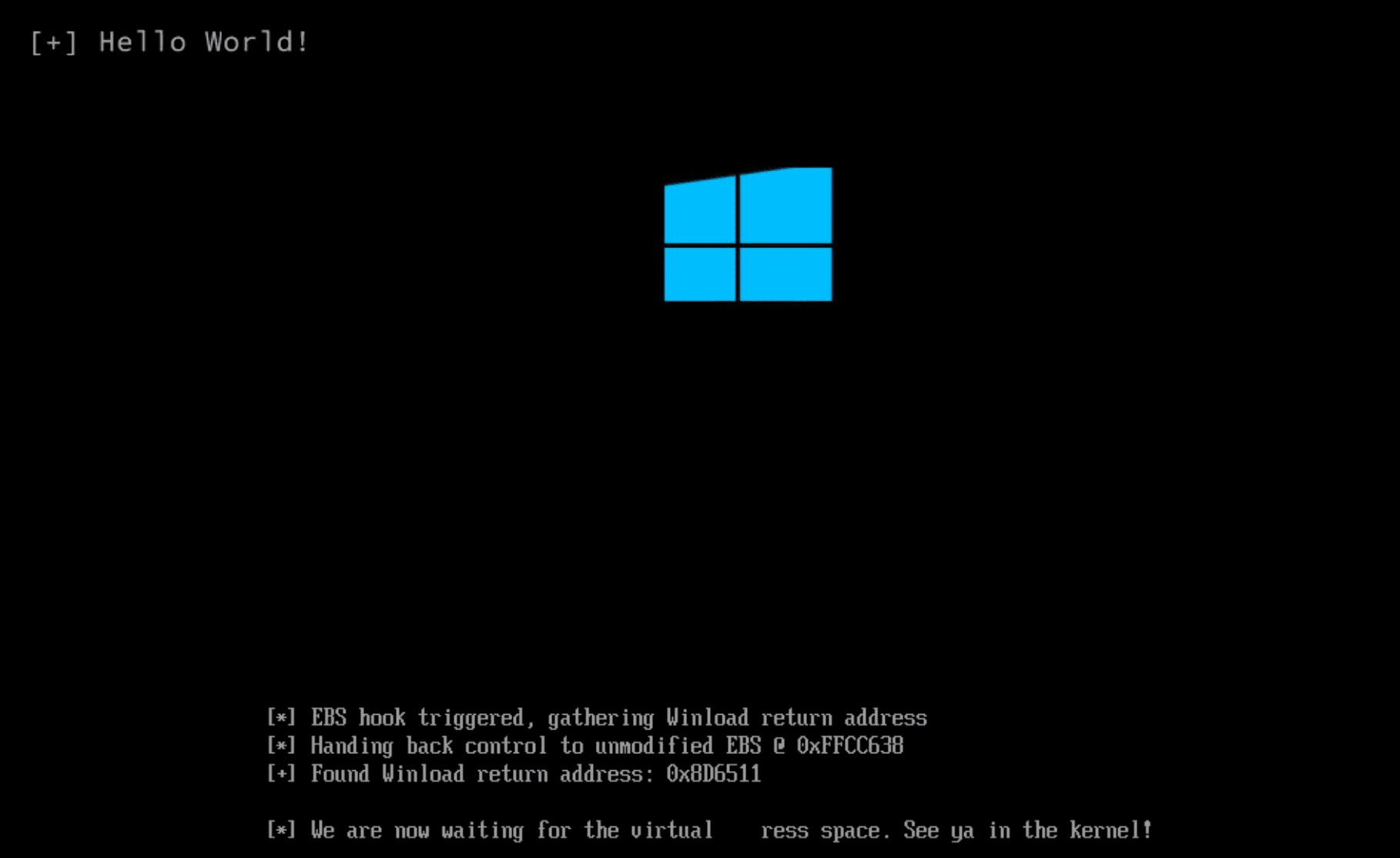
In this particular case, the bootkit leverages UEFI Runtime Services to achieve persistence and manipulate system components. The bootkit hooks into the ExitBootServices function—a crucial process in the bootloader’s sequence—granting the malware control over the system before the operating system takes over.
The ExitBootServices function is called just before the kernel gains control of the system. By overwriting the function pointer to this service within the global Boot Services object, the bootkit seamlessly integrates itself into the boot process. This modification allows it to intercept critical system operations. The researchers noted, “The hook function is minimal and only captures the return address of the caller which points to inside OslFwpKernelSetupPhase1. Afterward, it calls the original ExitBootServices to continue the boot process.”
Once the kernel’s base address is obtained, the bootkit targets the IoInitSystem function. This critical function is called early in the boot process after core system drivers are loaded but before boot drivers are initialized. By patching this function with a retpoline jump, the malware ensures its code is executed, enabling further kernel manipulation. The researchers stated, “At the end of the hook function, we restore the original code, and since the last address on the stack is the original function, when we return execution continues as normal.”
UEFI-based malware like this bootkit represents a significant threat because it operates at a level beneath traditional antivirus protections. Furthermore, the ability to persist through system reboots and evade detection makes such threats particularly dangerous.
To defend against such threats, organizations should ensure secure boot settings are properly configured and firmware is regularly updated. The researchers have made their proof-of-concept code available for educational purposes on GitHub.
For more technical details and access to the proof-of-concept code, visit the UEFIBootKit repository.
Related Posts:
- ESET Unveils “Bootkitty”: The First UEFI Bootkit Targeting Linux Systems
- Security Alert: Bootkitty Bootkit Targets Linux via UEFI Vulnerability (CVE-2023-40238)
- Ubuntu 18.04 LTS will have Boot Speed Boost feature