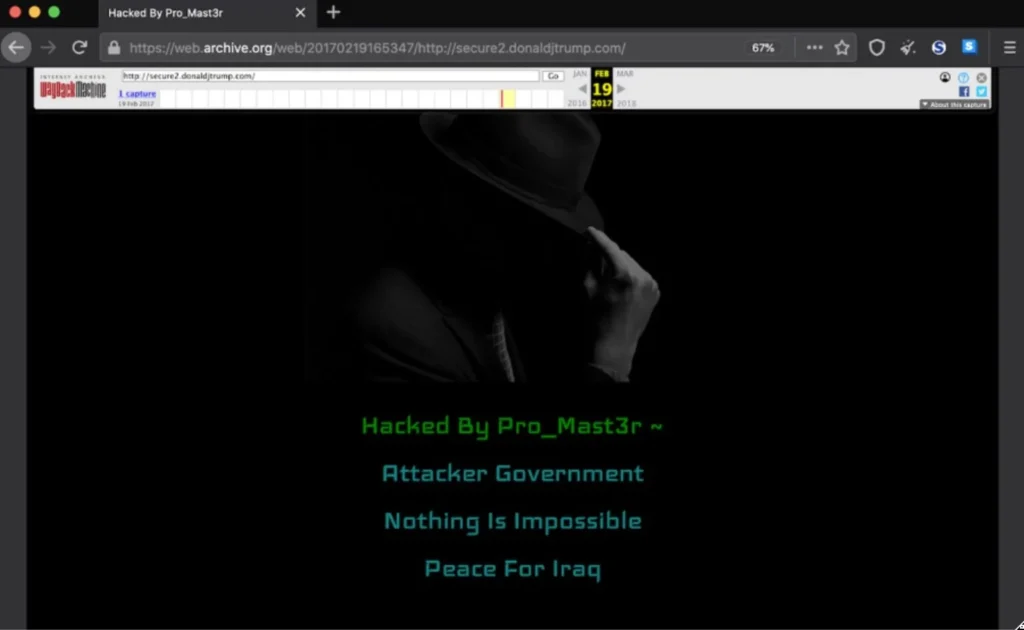
An example defaced website resulting from a subdomain takeover attack | Image: SentinelOne
Subdomain takeovers, a type of attack where an attacker gains control of an organization’s improperly configured or unused subdomain, may seem like a minor issue, but they can create significant cybersecurity risks. However, SentinelOne warns can escalate from a minor DNS misconfiguration into a full-blown supply chain attack.
There are several ways in which a subdomain takeover can occur, but the most common involves the misuse of Domain Name System (DNS) records, particularly canonical name (CNAME) records.
A primary cause is when these records are set up to point to a specific subdomain, and that subdomain either expires and becomes available for registration by an attacker or the attacker sets up virtual hosting for the subdomain before the organization can. This is often referred to as “Dangling DNS”.
“Dangling DNS” is defined by a DNS record that directs traffic to a subdomain or resource that is vulnerable to attack.
It’s important to note that the risk isn’t limited to CNAME records; other DNS records like NS, MX, A, and AAA records can also be exploited.
While a defaced landing page or stolen credentials is damaging, the real threat lies in supply chain abuse. Subdomains frequently serve static resources and container images—critical elements in modern development pipelines.
An example comes from a recent investigation where researchers registered 150 abandoned S3 buckets and recorded over 8 million requests targeting these buckets—many from active pipelines and internal build systems.
These included requests for:
- CloudFormation templates
- Unsigned Windows, Linux, and macOS binaries
- Container images
- Software updates
- VPN configurations
Subdomain takeovers open the door for:
- Malware distribution via spoofed software updates
- Credential harvesting through phishing subdomains
- Remote Code Execution (RCE) in build pipelines
- Persistent backdoors within DevOps environments
- Brand defacement and trust erosion
The attacker’s control over an infrastructure component can cascade down the entire supply chain, affecting thousands of downstream users or clients—similar in magnitude to the infamous SolarWinds attack.
“The scope for remote code execution (RCE), resource hijacking, persistent backdoors, credential theft, and privilege escalation is matched only by the imagination of an attacker,” SentinelOne warns.
In conclusion, subdomain takeovers, fueled by misconfigurations and oversights, present a significant and evolving cybersecurity challenge, particularly in the context of software supply chains. Organizations must remain vigilant and proactive in identifying and mitigating these risks to protect themselves and their customers.
Related Posts:
- HTTP Client Tools Weaponized in Account Takeover Attacks
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected
- Breaking News: Widespread WordPress Plugin Compromise in Active Supply Chain Attack