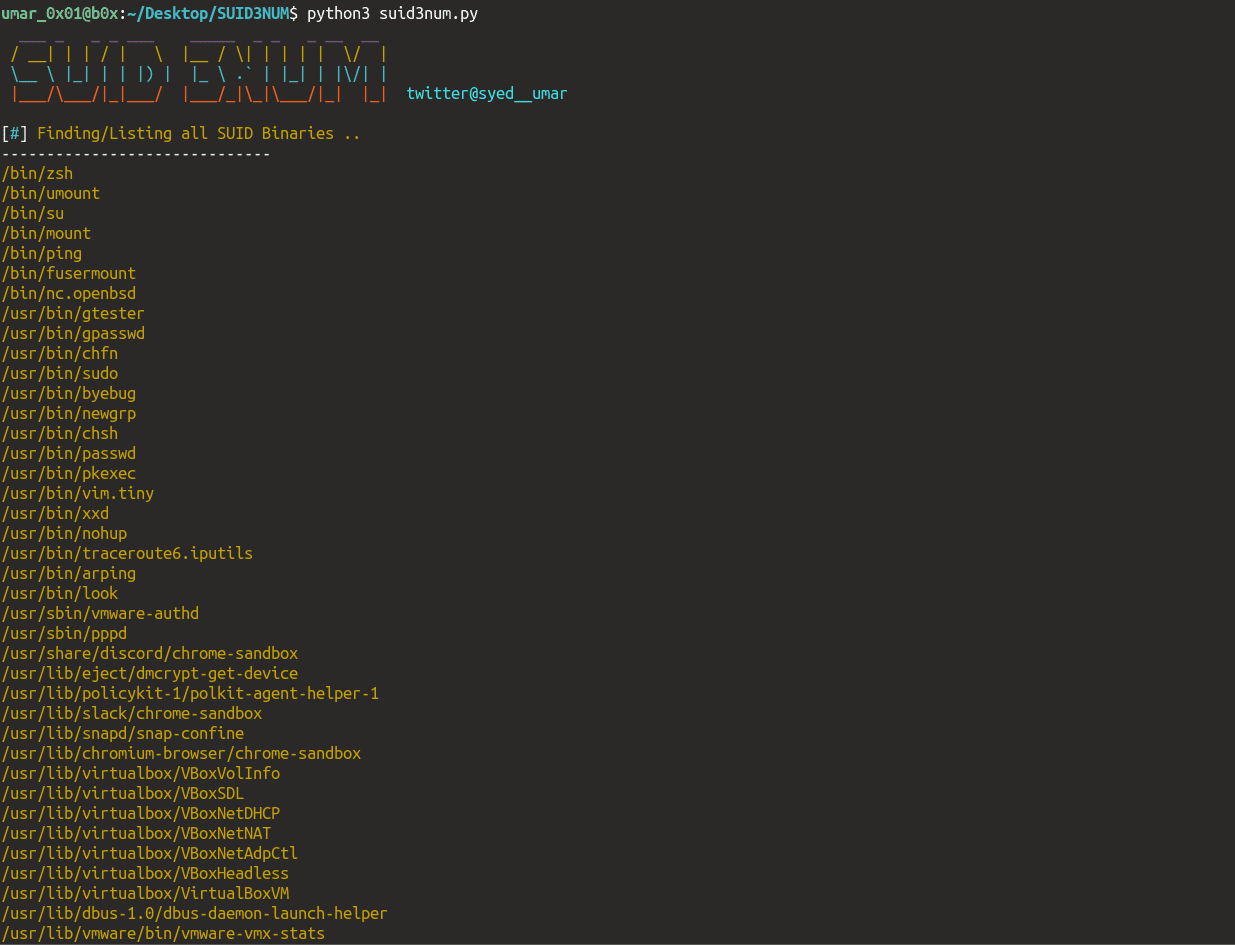
SUID3NUM
A standalone script supporting both python2 & python3 to find out all SUID binaries in machines/CTFs and do the following
- List all Default SUID Binaries (which ship with Linux/aren’t exploitable)
- List all Custom Binaries (which don’t ship with packages/vanilla installation)
- List all custom binaries found in GTFO Bin’s (This is where things get interesting)
- Printing binaries and their exploitation (in case they create files on the machine)
- Try and exploit found custom SUID binaries which won’t impact the machine’s files
Why This?
- Because LinEnum and other enumeration scripts only print SUID binaries & GTFO Binaries, they don’t seperate default from custom, which leads to severe headbanging in walls for 3-4 hours when you can’t escalate privs 🙂
Can I use this in OSCP?
Yes, you totally can. I used it in my exam, linked it in the report as well. Just don’t use -e (according to some people) and you’re good to go!
Download & Use
Initializing Script
python suid3num.py
Doing Auto Exploitation of found custom SUID binaries
python suid3num.py -e
Output
Copyright (c) 2019 Syed Umar Arfeen
Source: https://github.com/Anon-Exploiter/