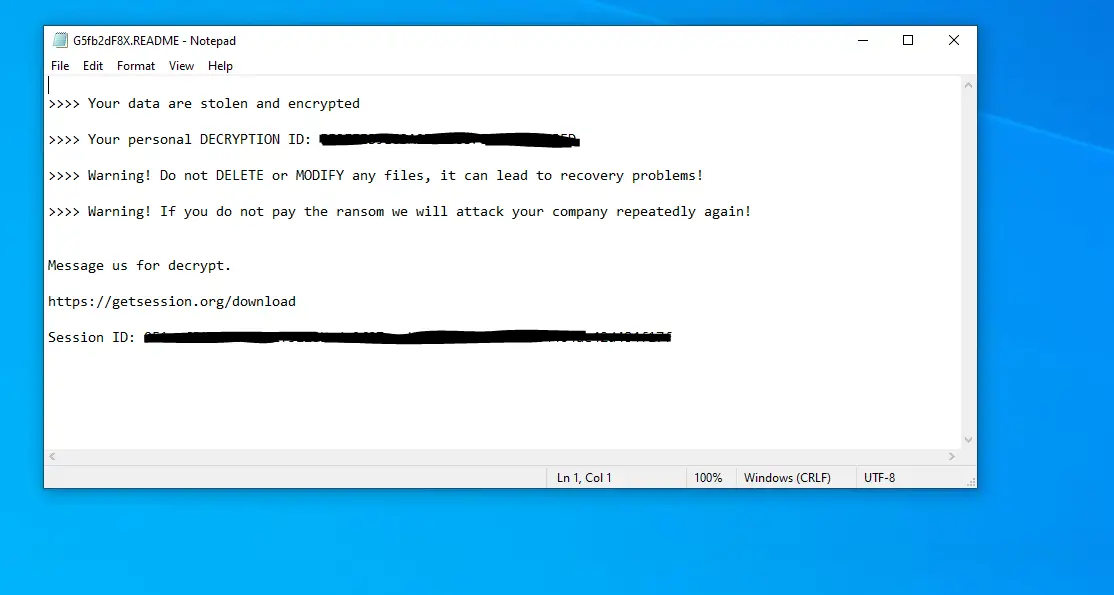
A LockBit 3.0 ransom note | Image: Kaspersky Labs
Kaspersky Labs has identified a new cybercriminal group dubbed Crypt Ghouls, responsible for a series of ransomware attacks against Russian businesses and government agencies. The group’s modus operandi involves exploiting compromised credentials from contractors and subcontractors to gain initial access, followed by the deployment of LockBit 3.0 and Babuk ransomware to encrypt victims’ data.
According to Kaspersky’s analysis, Crypt Ghouls often begins its attacks by using stolen contractor credentials to infiltrate target systems via VPN connections. These connections were traced back to Russian hosting providers and compromised contractor networks. Once inside, the group employs a variety of tools to move laterally and maintain persistence. “To maintain access to the system, the attackers used the NSSM and Localtonet utilities,” Kaspersky noted, adding that these tools create and manage services on compromised hosts while providing encrypted tunnels for remote access.
The group’s arsenal includes well-known hacking tools such as Mimikatz, XenAllPasswordPro, and AnyDesk. One particularly alarming aspect of the Crypt Ghouls campaign is their use of CobInt, a backdoor loader, which Kaspersky described as a “telltale tool” linking this group to other notorious campaigns. “The CobInt downloader we encountered is a VBScript called Intellpui.vbs that executes obfuscated PowerShell code,” the report stated, allowing attackers to load malware into memory without leaving traces on disk.
Crypt Ghouls relies heavily on LockBit 3.0 and Babuk ransomware to wreak havoc on their victims’ systems. LockBit 3.0, a notorious ransomware variant, is used to encrypt critical data on Windows systems. Kaspersky highlighted the unique nature of this encryption process, stating, “We found a cycle that systematically renamed the original file in the recycle bin, iterating through every letter of the English alphabet until it reached the last one. This type of encryption makes it really hard, or even impossible, to recover the user’s files.” The group also adds directories containing tools for harvesting credentials to the encryption exclusion list to retain control even after the encryption process is completed.
On Linux systems, Crypt Ghouls deploys Babuk, a ransomware strain designed to target ESXi servers, which host virtual machines. The attackers connect to these servers via SSH, upload Babuk, and begin encrypting files within virtual machines, disrupting organizational operations.
Kaspersky’s analysis uncovered significant similarities between Crypt Ghouls and other groups such as MorLock, BlackJack, and Twelve. These groups share many of the same utilities, including SoftPerfect Network Scanner, PingCastle, and XenAllPasswordPro, making it difficult to attribute attacks to specific actors.
“The file and folder names used in attacks by both groups also show similarities,” Kaspersky stated, noting that both Crypt Ghouls and MorLock used the same resocks utility and similar naming conventions for key attack tools. Furthermore, the infrastructure supporting these attacks frequently overlaps, suggesting that multiple groups are either sharing resources or collaborating directly.
Crypt Ghouls is just the latest in a series of sophisticated cybercriminal groups targeting Russian organizations. The group’s ability to leverage publicly available ransomware like LockBit 3.0 and Babuk, combined with shared tools and tactics across multiple cybercriminal groups, makes attribution and mitigation increasingly difficult. Kaspersky Labs’ analysis concludes that “cybercriminals are leveraging compromised credentials, often belonging to subcontractors, and popular open-source tools,” making it challenging to identify specific attackers.
Related Posts:
- New malware automatically detects computer configuration to determine mining or crypting
- Avast Unveils Updated Babuk Decryptor in Collaboration with Cisco Talos and Dutch Police
- RA World Ransomware: A Babuk Successor Targets Healthcare
- LockBit Imposter: New Ransomware Leverages AWS for Attacks
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities