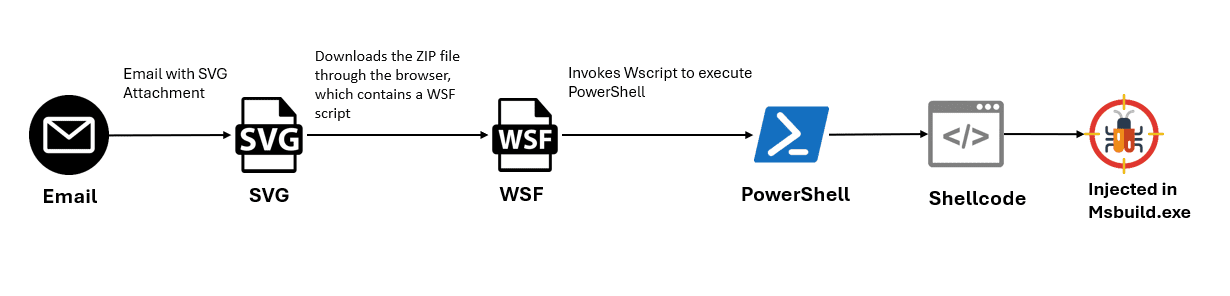
Infection chain
The cybersecurity world is a battlefield of constant change – understanding your enemy’s weapons and strategies is key to survival. Enter GULoader, a malware favored by cybercriminals for its stealth, adaptability, and ability to bypass defenses, posing a serious threat to businesses and individuals alike.
GULoader’s Cloak of Invisibility
Think of GULoader malware as a digital chameleon. It employs sophisticated techniques like polymorphic code (constantly changing itself) and encryption to obscure its true nature and slip undetected past traditional antivirus solutions. This makes it remarkably persistent, allowing it to establish a foothold within your network while defenders remain oblivious.
The Case of the Malicious SVG

A recent McAfee Labs study uncovered how GULoader is being distributed – disguised as an innocent-looking SVG (Scalable Vector Graphics) file sent via email. SVG files, commonly used for logos and icons on websites, are often trusted. Here’s how the attack unfolds:
-
The Lure: An enticing email arrives with an SVG attachment promising urgent information or an invoice. The meticulous analysis of this campaign reveals a spam email harboring the trojan SVG file, innocuously named “dhgle-Skljdf.svg”. The embedded JavaScript, a Trojan horse in its own right, conjures a malicious zip archive upon the file’s activation. This archive, birthed from a Blob object containing base64 encoded data, drops onto the system through the browser’s unwitting complicity.
-
Hidden Payload: Attackers leverage commonly used and often less scrutinized file formats, such as SVGs, to circumvent traditional defenses focused on blocking executable files. This underscores the need for content-aware security solutions capable of inspecting data within seemingly innocent files.
-
Chain Reaction: Opening the SVG triggers a series of events. Malicious code creates a ZIP file, followed by a WSF (Windows Script File) that launches PowerShell commands.
-
Command and Control: PowerShell reaches out to a compromised domain, downloading and executing shellcode directly into the legitimate MSBuild process. This “process hollowing” technique allows GULoader to operate under the guise of a trusted application.
Shapeshifting and Expanding its Arsenal
Once injected, GULoader checks for analysis tools and establishes persistence in the system by modifying the Windows Registry. The downloaded shellcode acts as a loader, capable of fetching and launching a wide range of even more harmful malware – from ransomware to data-stealing Trojans.
Protecting Yourself Against GULoader
-
Extreme Vigilance with Attachments: Train employees to scrutinize emails with unexpected attachments, even seemingly benign file formats like SVGs.
-
Layered Defenses: Relying solely on traditional antivirus isn’t enough. Implement endpoint detection and response (EDR) tools and network monitoring for early detection.
-
Patching and Updates: Keeping software and operating systems up-to-date is critical. Patch vulnerabilities to reduce the attack surface GULoader can exploit.
-
Zero Trust Architecture: Assume breaches will happen. Segment your network and enforce least privilege access to minimize the damage from any successful attack.