Hackers use a five-year-old vulnerability to infect Linux servers and earn money
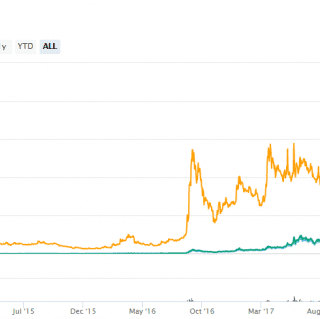
The hacker group used the Cacti “Network Weathermap” plug-in for a five-year-old vulnerability to install Monero miners on Linux servers and made nearly $75,000. Experts from US security company Trend Micro said that...