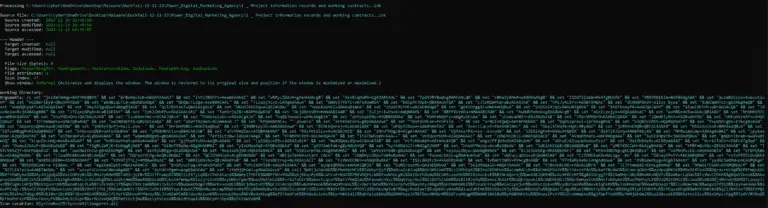
The RedCurl Advanced Persistent Threat (APT) group, also known as Earth Kapre or Red Wolf, has resurfaced...
powershell
A recent report by Cyble Research and Intelligence Labs (CRIL) unveils a troubling trend: threat actors are...
The ever-evolving Python NodeStealer has resurfaced with advanced techniques and a broader target range, as detailed in...
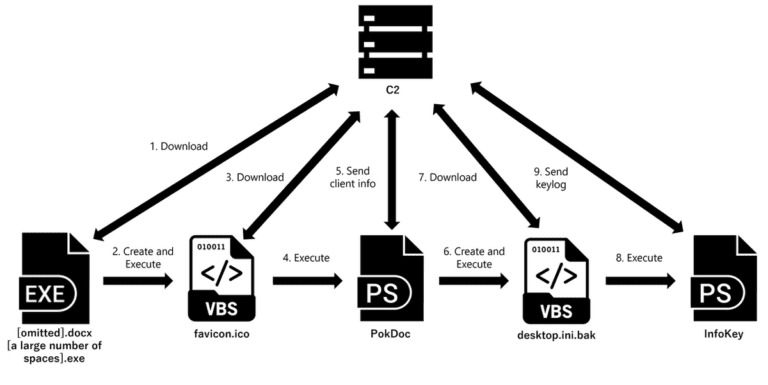
In a recent discovery, Cyble Research and Intelligence Lab (CRIL) detailed a complex, multi-stage PowerShell campaign that...
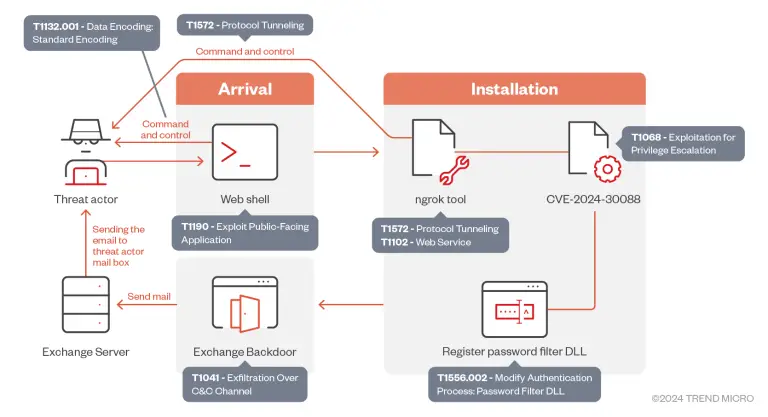
Trend Micro researchers have uncovered a series of advanced cyberattacks carried out by the threat group Earth...
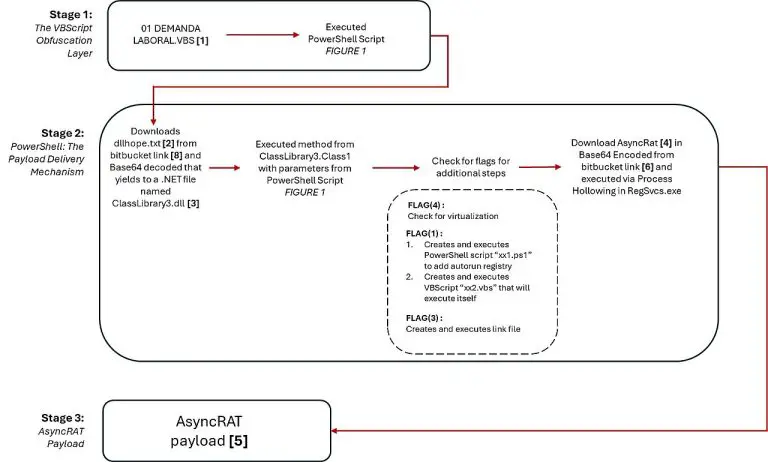
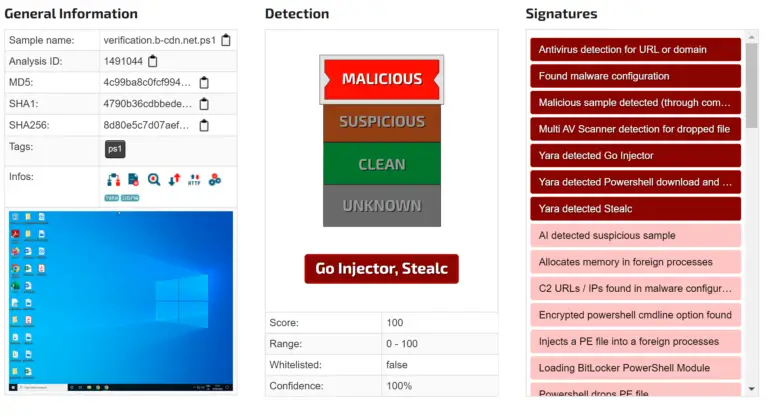
G DATA Security Lab recently uncovered a sophisticated malware campaign leveraging Bitbucket, a popular code hosting platform,...
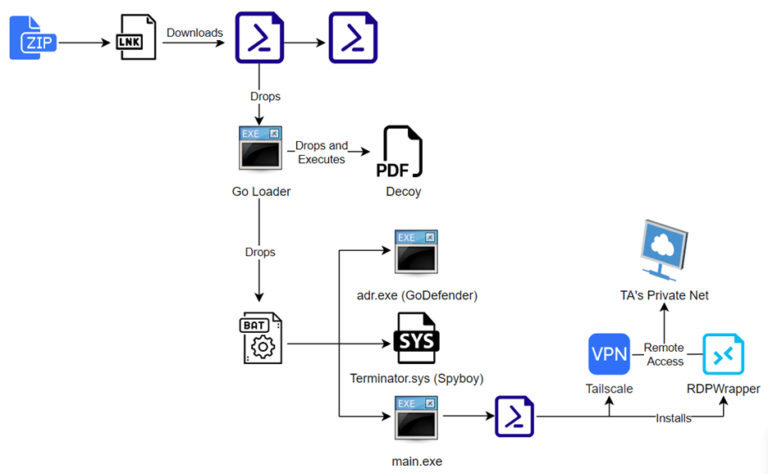
Recently, the eSentire Threat Response Unit (TRU) discovered a concerning new malware delivery chain involving a Go-based...
The CYFIRMA Research and Advisory Team has identified a new and sophisticated cyber threat, dubbed the Mekotio...
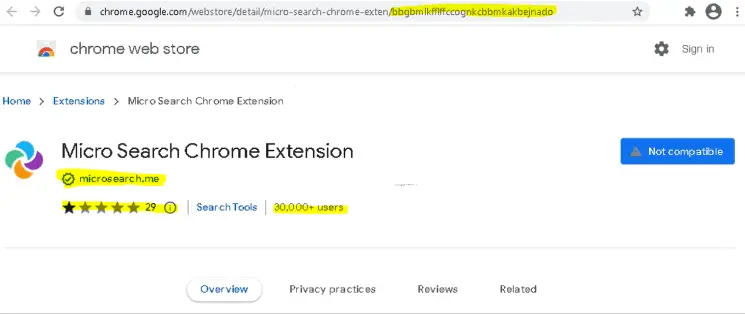
The ReasonLabs Research Team has discovered a widespread polymorphic malware campaign that forcefully installs malicious extensions on...
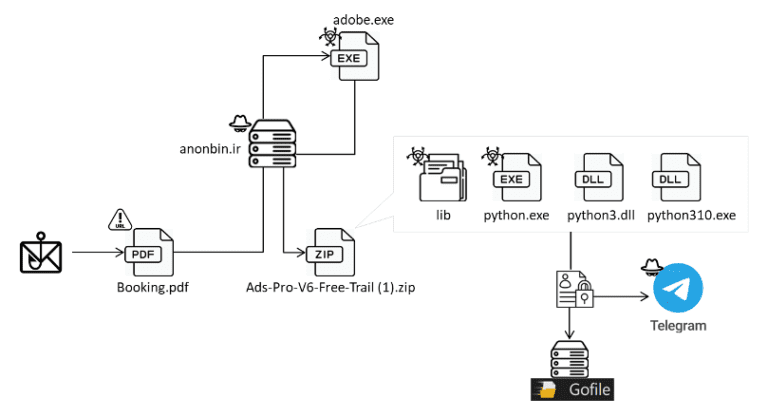
Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated cyberattack campaign targeting cryptocurrency users. This multi-stage...
Japanese organizations are being targeted by the notorious North Korean advanced persistent threat (APT) group, Kimsuky, in...
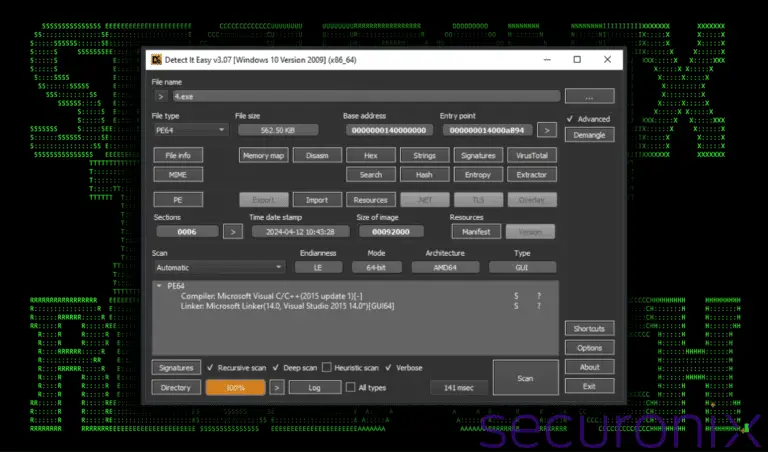
Securonix’s Threat Research team has uncovered a novel cyberattack campaign, dubbed CLOUD#REVERSER, that leverages legitimate cloud storage...
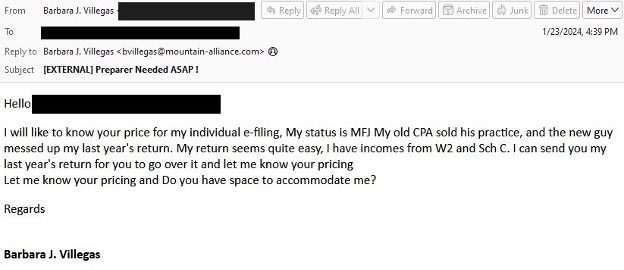
As the tax season rolls in, so does the threat of cybercrime, and leading the charge in...
In December 2023, the cybersecurity community was alerted to a new form of cyber threat – the...
In a digital age teeming with cyber threats, FortiGuard Labs recently identified an email phishing campaign that...