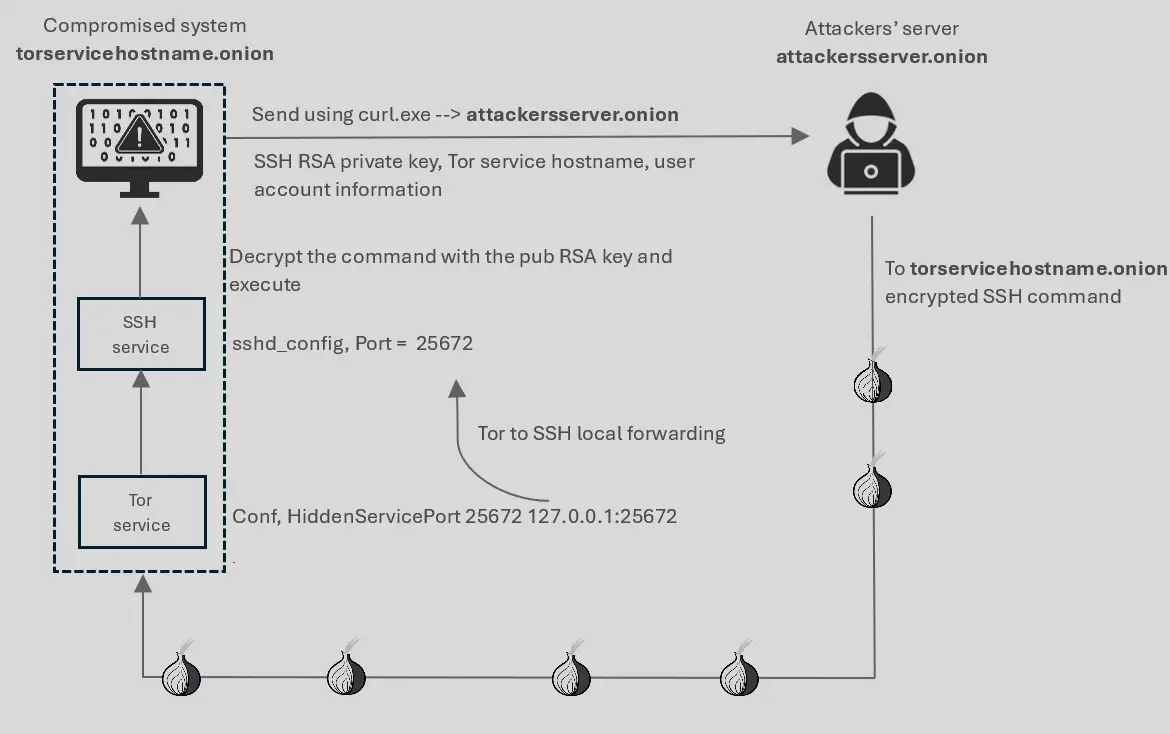
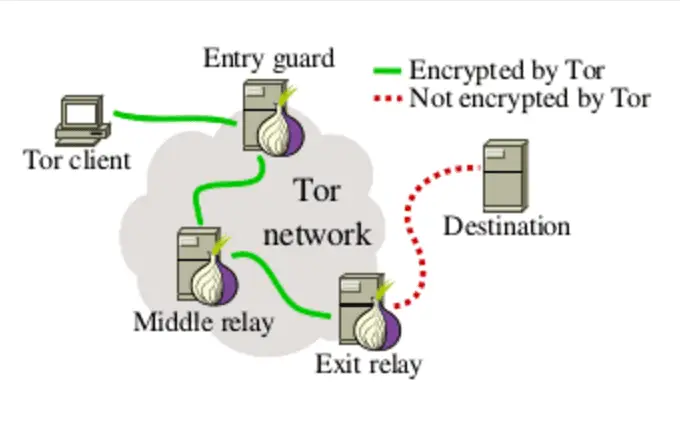
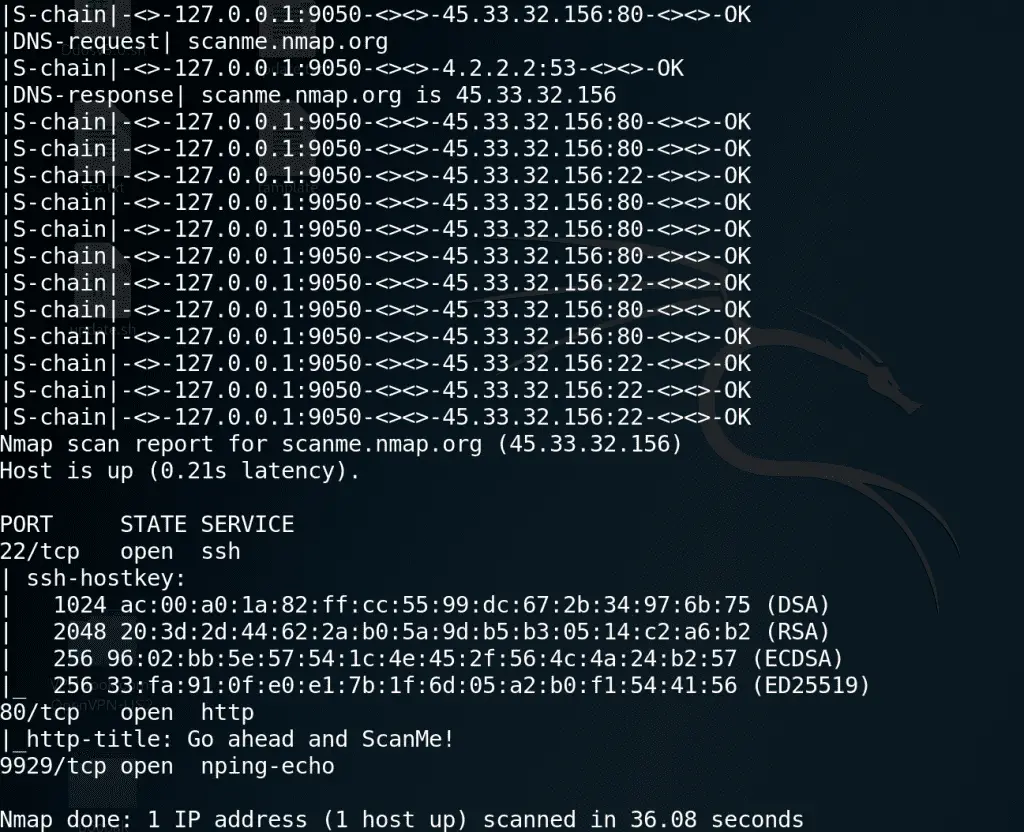
Malware Targeting the Ukrainian Military: SSH Over TOR Backdoor Unveiled
Security researcher Artem Baranov has detailed a sophisticated malware campaign targeting the Ukrainian military through a backdoor leveraging SSH over TOR. The campaign exploits the digital infrastructure of “Army+,” a...