Source: XLab
A discovery by XLab has detailed Glutton, a stealthy PHP backdoor targeting both traditional organizations and the cybercrime ecosystem itself. According to XLab’s analysis, Glutton represents a new generation of cyber threats, blending modularity with strategic subterfuge in what appears to be a carefully orchestrated campaign by the APT group Winnti.
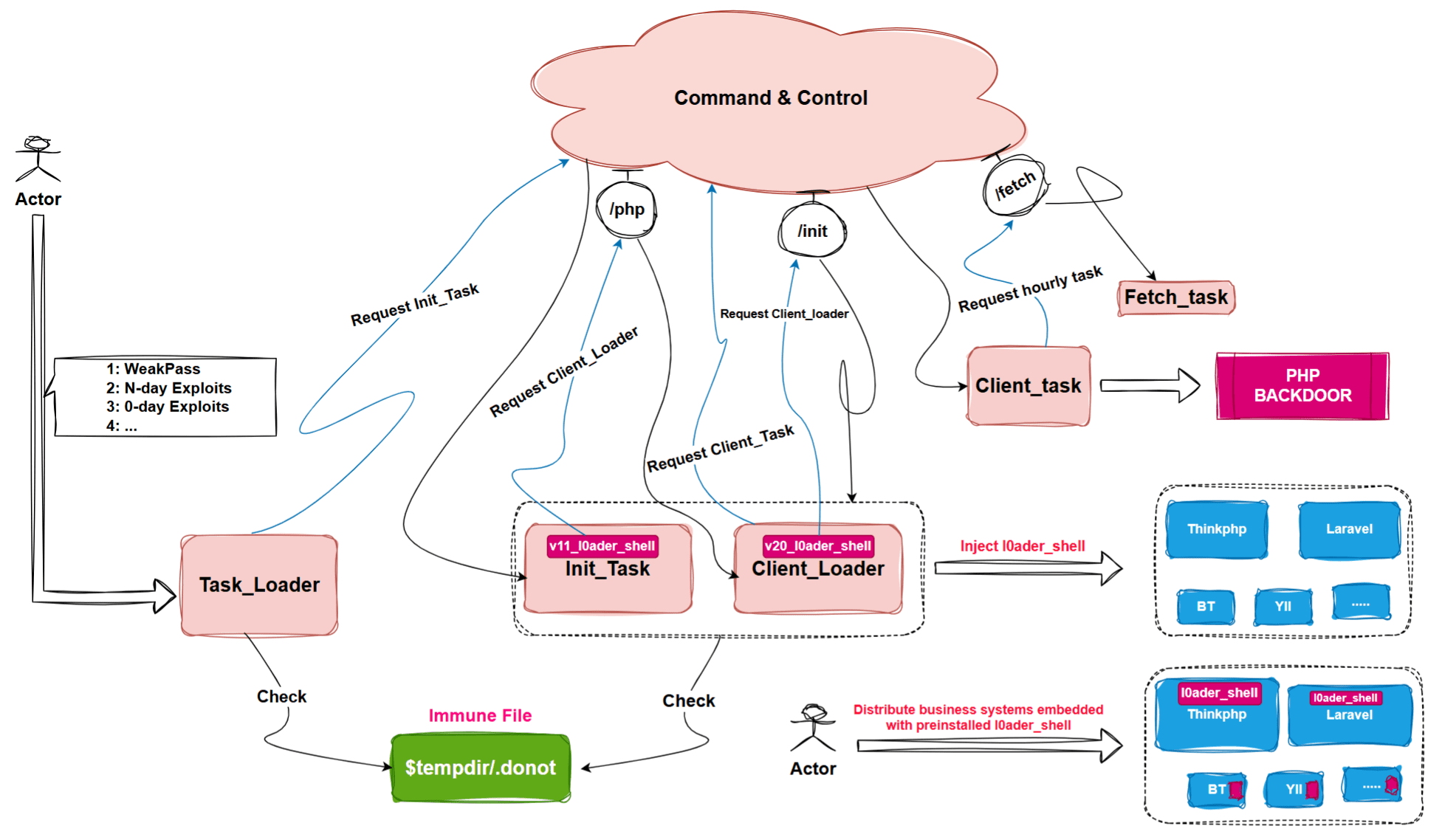
On April 29, 2024, XLab’s Cyber Threat Insight and Analysis System (CTIA) detected unusual activity originating from IP 172.247.127.210. Initially linked to an ELF-based Winnti backdoor, the investigation uncovered a malicious PHP file, init_task.txt, distributed earlier on December 20, 2023. This file led researchers to identify multiple malicious PHP payloads, including task_loader, client_task, and l0ader_shell. Together, these modules create a highly adaptable framework capable of executing fileless attacks.
“We uncovered a previously undocumented advanced PHP backdoor, which we named Glutton due to its ability to infect large numbers of PHP files and implant l0ader_shell,” XLab stated in its report.
The Glutton backdoor operates using a modular framework, allowing attackers to execute various stages of an attack without leaving file traces. Its core functionalities include:
- Data Exfiltration: Stealing sensitive information such as Baota panel credentials and PHP configuration data.
- Backdoor Installation: Deploying both PHP- and ELF-based Winnti backdoors.
- Code Injection: Injecting malicious code into popular PHP frameworks like Laravel, Yii, and ThinkPHP.
According to the report, “All code execution occurs within PHP or PHP-FPM (FastCGI) processes, ensuring no file payloads are left behind, thus achieving a stealthy footprint.”
While Glutton targets IT services, business operations, and social security sectors, XLab’s analysis revealed a surprising twist: its creators also exploit the cybercrime ecosystem. By embedding backdoors into business systems sold on underground forums, Glutton turns cybercriminals into unwitting agents of its campaign.
XLab described this as a “no honor among thieves” scenario, where tools meant for gambling scams or click-fraud operations are poisoned to serve Glutton’s operators. “Why should these small-time scammers in gambling and click-fraud get all the money? Let’s rob them blind,” the report summarized the hackers’ strategy.
Despite its innovative approach, Glutton’s simplicity raises questions about its authorship. Unlike the sophisticated tools typically associated with Winnti, Glutton’s implementation shows several shortcomings:
- Lack of encrypted C2 communications, making traffic easy to intercept.
- Unobfuscated PHP samples, leaving its source code exposed.
- Use of plaintext HTTP for downloader communication, simplifying interception.
XLab noted, “While Glutton’s delivery mechanisms strongly align with the Winnti group, its lack of stealth and simplistic implementation introduce uncertainty.”
Glutton infections have been traced to victims in China and the United States, with a focus on IT services and business operations. However, its reach extends further, facilitated by underground forums selling infected systems.
To mitigate the threat of Glutton, XLab recommends inspecting PHP files for signs of l0ader_shell, removing associated malicious processes, and securing temporary directories. System administrators must also stay vigilant, given the backdoor’s modular nature and ability to infect widely used PHP frameworks.
Related Posts:
- Kiteshield Packer Emerges as a Significant Threat in Linux Malware Landscape
- New Melofee Backdoor Variant Targets Linux Systems with Advanced Stealth Tactics