Image: CYFIRMA
A recent report by CYFIRMA sheds light on the infrastructure supporting the activities of the Advanced Persistent Threat (APT) group known as Transparent Tribe, also referred to as APT36. This Pakistan-based threat group, active since 2013, is primarily focused on espionage, targeting Indian government officials and defense sectors. This OSINT investigation uncovers new tactics involving Mythic Poseidon binaries, malicious Linux desktop files, and the command-and-control (C2) infrastructure used by the group.
CYFIRMA’s investigation reveals the group’s reliance on 15 malicious hosts, primarily hosted by DigitalOcean, to control their operations. The hosts are part of a Mythic C2 infrastructure—a post-exploitation framework typically used for red teaming but increasingly abused by threat actors like Transparent Tribe.
A significant development in Transparent Tribe’s attack strategy is their use of Linux desktop entry files, posing a particular threat to individuals in India. This approach marks a shift in targeting Linux environments, likely due to the widespread use of the Debian-based BOSS OS in Indian government institutions and the introduction of Maya OS. Transparent Tribe’s deployment of these customized payloads, including the Mythic Poseidon binaries, points to the group’s growing focus on exploiting Linux-based systems.
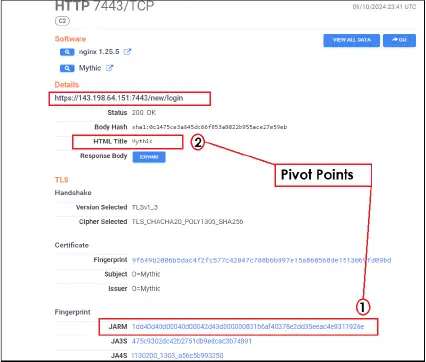
The investigation began with a Twitter post by security researcher @PrakkiSathwik, identifying two IP addresses (206.189.134.185 and 143.198.64.151) linked to Transparent Tribe’s C2 servers. By using JARM fingerprinting and HTML metadata analysis, CYFIRMA successfully identified 15 servers running the Mythic C2 framework.
Among the key identified servers, 143.198.64.151 became the pivot point, revealing a larger network of hosts. The Mythic framework, while initially created for legitimate penetration testing purposes, is being weaponized by Transparent Tribe to remotely control compromised systems. This infrastructure provides the group with persistent access to compromised machines, furthering their cyber espionage goals.
CYFIRMA’s report highlights a novel attack method used by Transparent Tribe—Linux desktop entry files disguised as PDFs. These files initiate malicious actions when executed, such as downloading and running binaries from remote servers. The report identifies two key payloads, trs-clip, and debian-clip, which establish persistence and evade detection by manipulating the system’s crontab.
The OSINT investigation into Transparent Tribe’s C2 infrastructure underscores the APT group’s persistence and adaptability in targeting Indian government sectors. By leveraging Mythic C2 and deploying malicious Linux binaries, the group has expanded its toolkit to enhance its cyber espionage operations. As Transparent Tribe continues to evolve, organizations must remain vigilant, especially those using Linux-based systems in critical sectors.
Related Posts:
- Transparent Tribe Targets Indian Government and Defense Sectors with Evolving Cyber Espionage Tactics
- From SideCopy to Transparent Tribe: Pakistan APTs Hit Indian Government With RATs
- Transparent Tribe & SideCopy: A Dangerous Cyber Alliance Targeting India
- Professional Goods & Services at Risk: Decoding CYFIRMA’s Cybersecurity Report