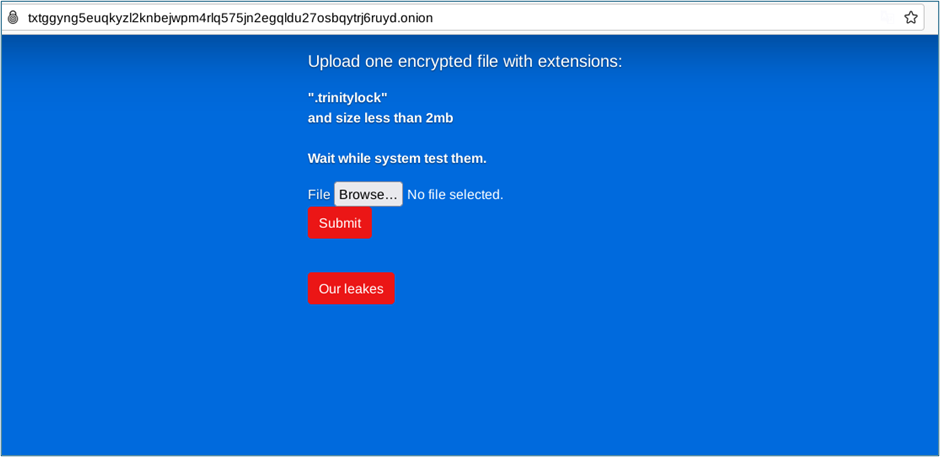
Trinity Victim Support Site
Cyble Research and Intelligence Labs (CRIL) has recently published a detailed analysis of a newly identified ransomware variant named Trinity, highlighting its potential links to the previously known Venus ransomware. This report delves into the technical similarities and operational tactics between these two formidable cyber threats.
Key Discoveries and Technical Similarities
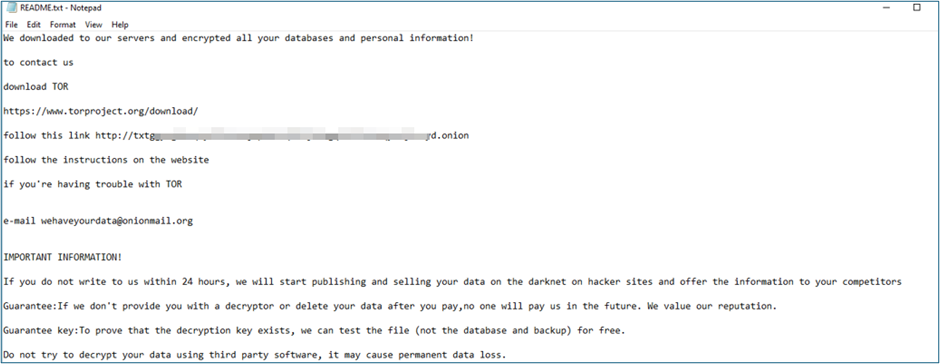
CRIL’s investigation revealed that Trinity ransomware utilizes a double extortion technique, a method increasingly favored by cybercriminals. This technique not only encrypts the victim’s data but also exfiltrates it, threatening to release the information publicly if ransom demands are not met. Notably, the perpetrators behind Trinity have established both a victim support site and a data leak site, though the latter currently shows no entries.

A significant finding from the report is the resemblance between Trinity and a ransomware dubbed “2023Lock.” Both share a similar ransom note format and underlying codebase, suggesting that Trinity may be an evolved variant of 2023Lock. Further analysis exposed even deeper connections with Venus ransomware, particularly in their usage of registry values and mutex naming conventions, indicating a possible shared lineage or common threat actor behind these variants.
Technical Breakdown of Trinity Ransomware
Trinity ransomware is characterized by its use of the ChaCha20 encryption algorithm, noted for its efficiency and security. The ransomware modifies the desktop wallpaper via a registry change, appends a “.trinitylock” extension to encrypted files, and distributes ransom notes in both text and .hta formats. Intricate technical procedures are employed for its operations, including advanced techniques for handling Windows API functions, managing COM objects, and interacting with system components to perform actions like shadow copy removal.
The analysis also touched upon the ransomware’s method for ensuring its persistence and evasion. For instance, Trinity checks for the presence of specific mutexes to determine if it should terminate itself to avoid detection or proceed with its malicious activities.
Implications and Concluding Thoughts
The discovery of Trinity underscores the ever-evolving nature of ransomware threats. The potential connections to established ransomware families like Venus could signify a troubling trend of collaboration and knowledge sharing among cybercriminal groups.
Furthermore, the double extortion tactic employed by Trinity adds another layer of complexity for victims. Not only do they face the disruption of encrypted files, but they also must contend with the threat of sensitive data being leaked online, leading to reputational damage and potential legal ramifications.
Recommendations for Businesses and Individuals
- Regularly Back Up Data: Maintain offline backups of critical data to mitigate the impact of ransomware attacks.
- Update Software: Keep all software, including operating systems and security solutions, up to date with the latest patches.
- Educate Employees: Train staff to recognize phishing emails and other social engineering tactics commonly used to deliver ransomware.
- Implement Strong Security Measures: Use strong passwords, enable multi-factor authentication, and consider endpoint protection solutions that can detect and block ransomware.