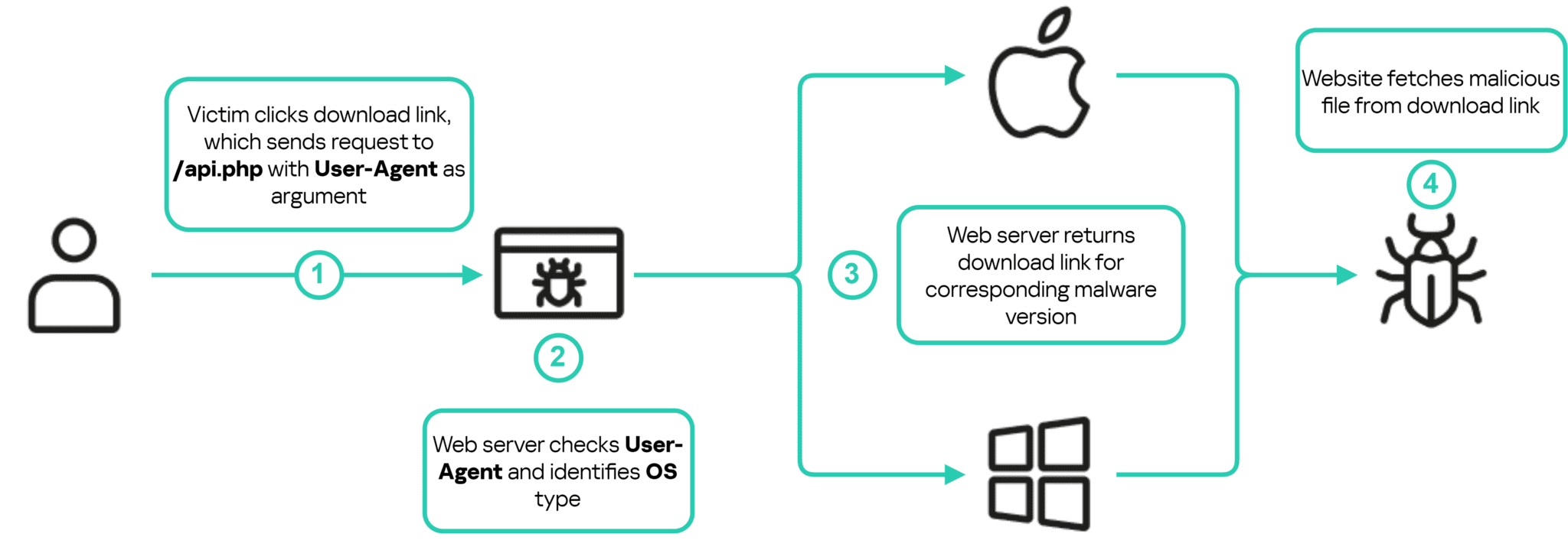
Malicious webserver routine to download the appropriate malware version depending on the user’s operating system | Image: Kaspersky Lab
Kaspersky Lab has uncovered an international cyber campaign targeting the theft of cryptocurrency and personal data from Windows and macOS users worldwide. The campaign has been named “Tusk.” The attacks appear to be orchestrated by Russian-speaking cybercriminals who employ phishing sites, info-stealers, and clippers to achieve their goals.
The perpetrators operate with cunning and complexity, luring victims to phishing sites that closely resemble legitimate services. To capture attention, they exploit popular themes such as Web3, cryptocurrency, artificial intelligence, and online gaming. Some of the discovered pages mimic a crypto platform, a role-playing online game, and an AI translator. These counterfeit resources are so convincingly designed that users are easily deceived into entering their personal information or downloading malicious software.
The fraudulent sites enable the extraction of sensitive user data, such as private keys for cryptocurrency wallets, and the installation of malware on the victim’s device. Subsequently, the attackers may gain access to the cryptocurrency wallet through the fake site, drain funds from it, or steal credentials, wallet details, and other information via malicious programs.
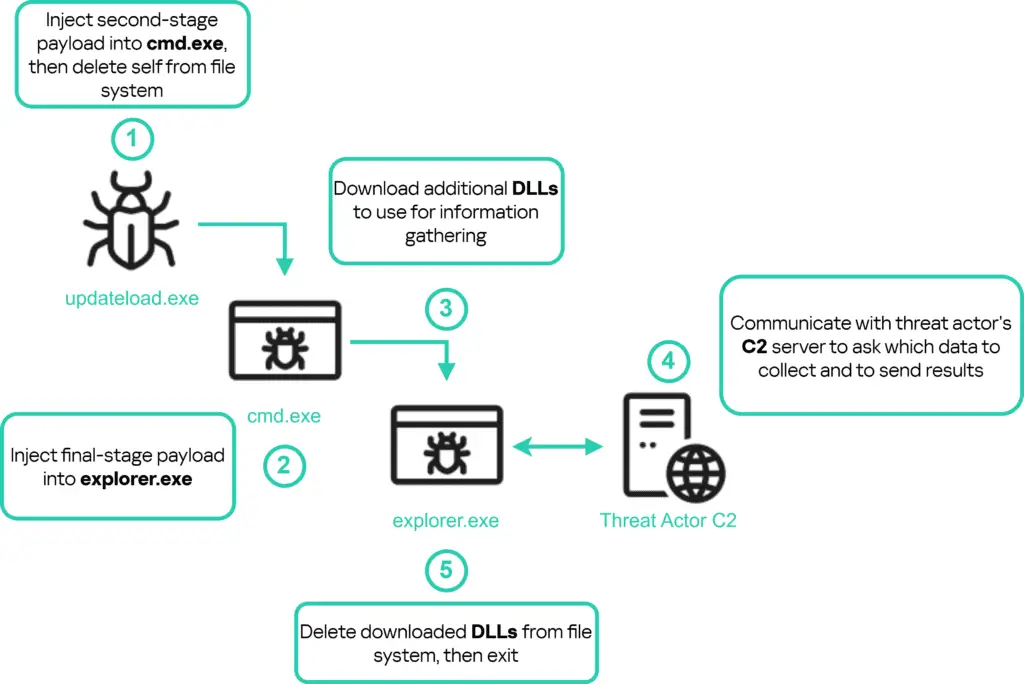
The cybercriminals’ arsenal includes info-stealers such as Danabot and Stealc, as well as clippers. The former is aimed at stealing passwords and other confidential information, while the latter intercepts clipboard data, substituting, for instance, cryptocurrency wallet addresses with malicious ones.
The files for downloading malicious software are hosted on Dropbox. When a victim downloads a file, they are redirected to a site with an appealing interface, where they are prompted to either log in or simply keep the page open. During this time, additional malware is downloaded, which continues the attack.
Intriguing details were found in the code of the malicious programs. It contains lines in Russian, and the downloaded files include the word “Mammoth,” which Russian-speaking cybercriminals often use to denote a victim. The attackers appear to have financial motives. The campaign’s name, “Tusk,” also references the image of a mammoth, which was hunted for its valuable tusks.
An analysis conducted by Kaspersky Lab specialists revealed that the Tusk campaign is meticulously planned and consists of several stages. Experts are confident that this series of attacks could be the work of either an organized group or a lone hacker with financial objectives. The company also noted that they were able to identify sub-campaigns on various popular topics, including cryptocurrency, artificial intelligence, and online gaming, as well as 16 others. This suggests that the perpetrators can quickly adapt to current trends and exploit them for attacks on users.
Related Posts:
- Hackers use ‘Poison’ Google Ads to steal $50 million in cryptocurrencies
- Beware! Fake Chrome App “Mamont” Steals Banking Details
- Stealthy New Golang Trojan Exploits Fake Certificates for Evasive Communication
- Malware infections associated with online gaming