In a recent report, cybersecurity firm Mandiant disclosed a significant cybercrime campaign targeting customers of Snowflake, the cloud-based data warehousing platform. Tracked as UNC5537, this financially motivated threat actor has systematically compromised hundreds of Snowflake customer accounts, resulting in the theft of a substantial volume of sensitive data.
Mandiant identified a campaign targeting Snowflake customer databases with the intent of data theft and extortion. Despite thorough investigations, there is no evidence to suggest unauthorized access resulted from a breach of Snowflake’s enterprise environment. Instead, compromised customer credentials have been the primary vector of attack.
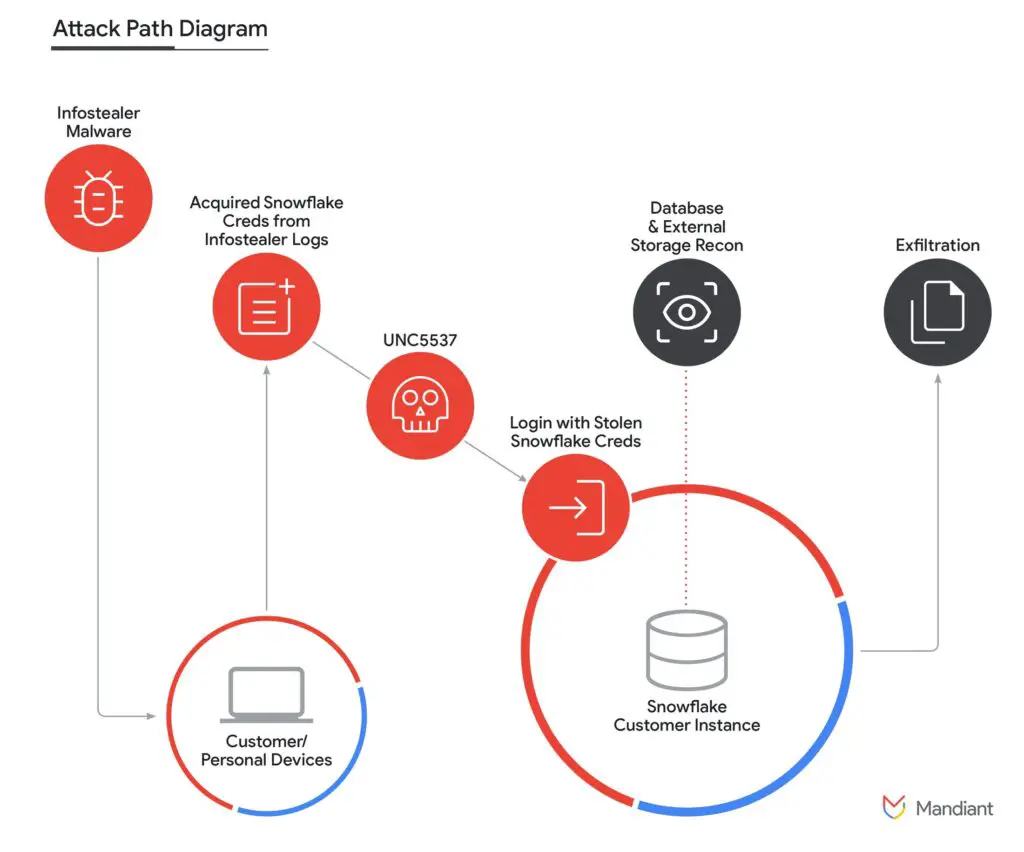
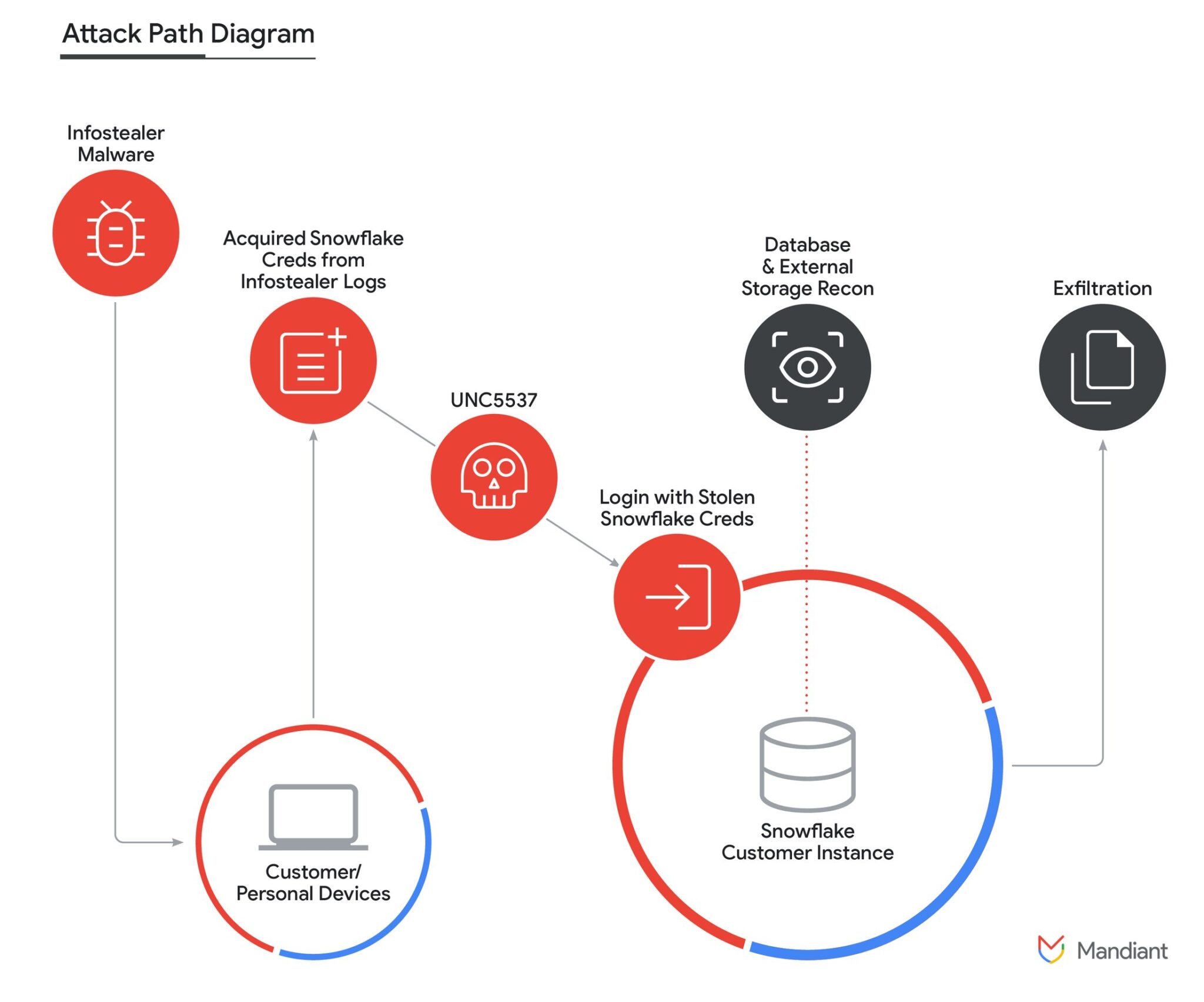
UNC5537 has leveraged stolen customer credentials, predominantly obtained through various infostealer malware campaigns, to access multiple Snowflake customer instances. The threat actor’s methodology involves using these credentials to exfiltrate valuable data and subsequently attempting to extort victims or sell the data on cybercrime forums.
The first instance of this campaign was identified in April 2024, when Mandiant received intelligence on compromised database records from a Snowflake instance. The investigation revealed that the affected organization’s Snowflake account was accessed using credentials stolen by infostealer malware. At the time of the breach, the account lacked multi-factor authentication (MFA).
Mandiant’s investigation revealed that the majority of the stolen credentials were obtained from infostealer malware such as VIDAR, RISEPRO, REDLINE, RACOON STEALER, LUMMA, and META. Notably, a significant portion of these credentials dated back to infections as early as 2020. Approximately 79.7% of the compromised accounts had prior credential exposure, highlighting the persistent risk of infostealer malware and the necessity of timely credential rotation.
The threat actor often exploited contractor accounts, where compromised personal devices used for both professional and private activities were the initial point of infostealer infection. These contractor devices, sometimes employed across multiple organizations, posed significant risks, especially when used to access critical systems with elevated privileges.
Initial access typically occurred via Snowflake’s web-based UI or command-line interface. UNC5537 also utilized a custom utility named “rapeflake” (tracked by Mandiant as FROSTBITE) for reconnaissance. This tool, available in both .NET and Java versions, interacted with Snowflake drivers to list users, roles, IPs, session IDs, and organization names.
For data exfiltration, UNC5537 executed a series of SQL commands across numerous Snowflake instances. Commands such as SHOW TABLES, SELECT * FROM, CREATE (TEMP|TEMPORARY) STAGE, and COPY INTO were used to stage and transfer data. The final exfiltration was achieved using the GET command, compressing data into GZIP files to reduce size before transferring to local directories.
Mandiant has identified UNC5537 as a North America-based group with at least one member collaborating from Turkey. The threat actor uses VPN services like Mullvad and Private Internet Access (PIA) for accessing victim instances and VPS systems from ALEXHOST SRL for data exfiltration. Stolen data is often stored on international VPS providers and cloud storage services such as MEGA.
Mandiant assesses that UNC5537 will continue targeting similar SaaS platforms, emphasizing the urgent need for robust credential monitoring, mandatory MFA enforcement, and securing authentication protocols. Organizations must also restrict traffic to trusted locations and promptly alert on abnormal access attempts.