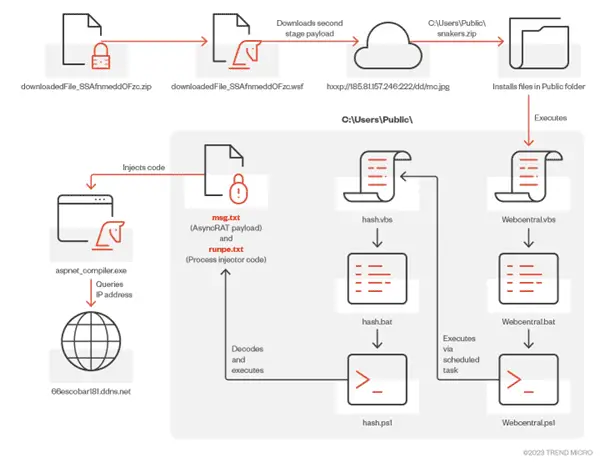
The AsyncRAT installation routine | Image Credit: Trend Micro
In the intricate tapestry of cybersecurity threats, a new contender has emerged with a menacing presence: AsyncRAT. This Remote Access Tool (RAT), identified for its versatility in keylogging and remote desktop control, has raised significant alarms across various cybersecurity platforms. In a detailed exploration, the Trend Micro Managed XDR (MxDR) team unveils the enigmatic nature of AsyncRAT, a tool that adeptly misuses aspnet_compiler.exe—a legitimate Microsoft process—for malevolent purposes.
AsyncRAT reveals the evolving tactics of adversaries. It exploits aspnet_compiler.exe, intended for precompiling ASP.NET web applications, injecting its payload to execute nefarious activities. This manipulation not only signifies the sophistication of modern cyber threats but also highlights the cunning exploitation of legitimate processes to evade detection.

AsyncRAT’s history is a testament to its adaptability. Throughout various campaigns, it has exhibited versatility in its delivery methods. In 2019 and 2020, amidst the COVID-19 pandemic, modified versions of AsyncRAT were distributed, leveraging the global crisis. Furthermore, the impersonation of local banks and law enforcement entities marked another strategy to deploy this RAT. The infamous Operation Spalax phishing campaign in 2021 further underlined AsyncRAT’s sustained usage across diverse attack vectors.
MxDR’s analysis dives into the AsyncRAT infection chain, which often begins with a seemingly innocuous download. A timeline of events from a typical AsyncRAT attack reveals a meticulously planned sequence, starting with a password-protected ZIP file download and culminating in the stealthy process injection to aspnet_compiler.exe. This approach cleverly bypasses antivirus defenses, employing reflective loading and dynamic DNS for discrete payload deployment.
Reflective loading emerges as a pivotal technique in AsyncRAT’s arsenal. This method allows attackers to discreetly deploy their payloads, thereby evading traditional detection mechanisms. The meticulously crafted payloads are embedded within legitimate processes, significantly complicating the task of identifying and neutralizing the threat.
AsyncRAT has displayed remarkable adaptability, constantly evolving its techniques to stay ahead of cybersecurity defenses. From exploiting pandemic themes to mimicking authoritative institutions, it demonstrates a chameleon-like ability to adapt and thrive in various cyber environments. Its use of dynamic DNS and reflective loading techniques exemplifies its resilience and determination to remain a potent threat.
AsyncRAT stands as a stark reminder of the evolving nature of cyber threats. Its ability to exploit legitimate processes, adapt to changing circumstances, and evade detection underlines the need for continuous vigilance and advanced cybersecurity measures.