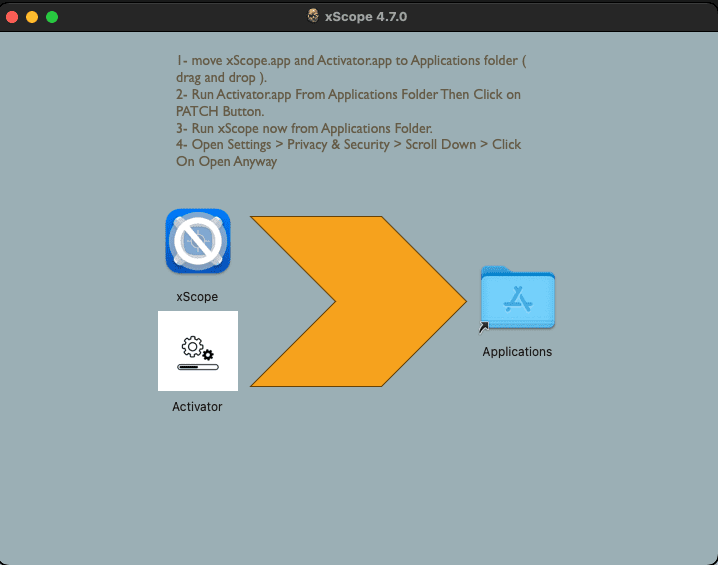
Window with installation instructions
In an Internet age where convenience often trumps security, the allure of cracked applications continues to be a trojan horse for unwary macOS users. A recent investigation by Kaspersky Labs has shed light on a sophisticated malware campaign that exploits this very vulnerability in human nature, deploying a multi-stage backdoor that’s as cunning as it is damaging.
The saga begins on pirated websites that offer cracked PKG files. These repackaged applications, laced with a Trojan proxy and a post-install script, mark the first step in a meticulously planned infection process. The newly discovered macOS malware family, embedded within these applications, extends its reach far beyond a mere unauthorized proxy server setup.
Upon the installation of the compromised software, users are introduced to “Activator.app,” a seemingly benign application that runs on macOS Ventura 13.6 and later. This application harbors a Python 3.9.6 installer and an extra Mach-O file, cunningly designed to execute a series of operations under the guise of a patching process. The process leverages an obsolete authorization function to gain administrative privileges, setting the stage for the actual payload delivery.

The malware’s ingenuity shines through its communication with the command-and-control (C2) server. By assembling a URL from hardcoded lists and a random sequence, the malware disguises its network traffic as an ordinary DNS request for TXT records. This approach not only evades detection but ensures the successful download of the payload, a Python script designed to execute arbitrary commands and transmit sensitive information back to the C2.
Initially, the downloaded script appeared outdated, with no response from the C2 server. However, persistence led to the discovery of a payload that transformed the script into a fully functional backdoor. Capable of executing received commands and harvesting a plethora of information from the infected system, this backdoor signifies the malware’s ultimate goal: to establish a persistent, covert presence on the macOS.
The malware campaign’s audacity culminates in its targeting of cryptocurrency wallets. By replacing legitimate cryptowallet applications with infected counterparts, the malware ensures a continuous stream of stolen cryptocurrency, exploiting the trust placed in digital wallets for financial security.
This intricate malware campaign, facilitated by cracked applications, serves as a stark reminder of the risks associated with bypassing official software channels. The blend of technical sophistication and psychological manipulation employed by these malicious actors underscores the ever-evolving threat landscape in cyberspace. For macOS users, the price of free software can often be far greater than anticipated, with privacy and security hanging in the balance.