Image: Volexity
Volexity, a leading cybersecurity firm, has revealed a novel attack technique employed by the Russian APT group GruesomeLarch (also known as APT28, Fancy Bear, etc.). Dubbed the “Nearest Neighbor Attack,” this method involves compromising Wi-Fi networks to target organizations in close physical proximity.
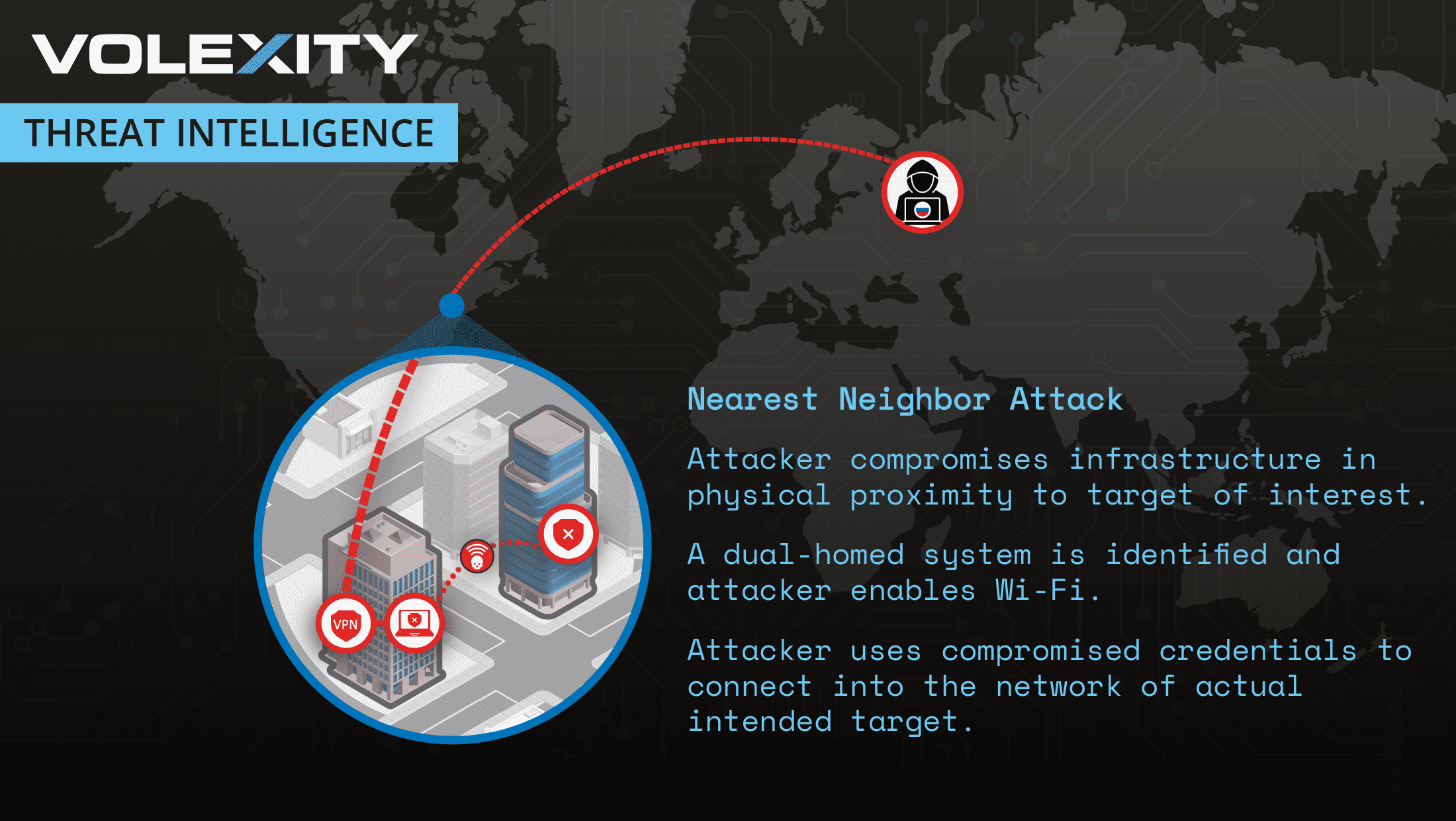
The Nearest Neighbor Attack represents a novel method of compromising enterprise Wi-Fi networks without direct physical proximity. Here’s how the operation unfolded:
- Credential Acquisition: Using password-spray attacks, the threat actors validated user credentials against public-facing services of the target organization. Multi-factor authentication (MFA) protected these services, but the organization’s Wi-Fi network lacked similar safeguards.
- Proximity-Based Exploitation: Unable to connect remotely to the target’s Wi-Fi, the attackers infiltrated nearby organizations, leveraging dual-homed systems connected to both wired and wireless networks. From these systems, they authenticated to the target’s Wi-Fi using compromised credentials.
- Lateral Movement: By “daisy-chaining” through multiple organizations, the attackers exploited network proximity to establish access to their ultimate target, Organization A.
The attackers meticulously covered their tracks, deploying living-off-the-land techniques to minimize their digital footprint. Tools like Cipher.exe were used to securely delete evidence, a method Volexity had never seen before. They also leveraged PowerShell scripts to locate accessible networks and compromised accounts for stealthy pivots.
“The Nearest Neighbor Attack effectively amounts to a close access operation, but the risk of being physically identified or detained has been removed,” Volexity noted.
The attack underscores a critical vulnerability in Wi-Fi network security. Even as organizations have fortified remote access services with MFA and other controls, Wi-Fi networks often remain less secure, creating an exploitable gap.
Volexity emphasized the importance of treating Wi-Fi networks with the same level of security as VPNs or email services. Key recommendations include:
- Implementing MFA for Wi-Fi Access: Strengthen authentication requirements for enterprise networks.
- Segregating Wi-Fi and Ethernet Networks: Prevent cross-access between sensitive systems.
- Enhanced Monitoring: Employ detection rules for anomalous use of utilities like Cipher.exe and netsh.
- Improved Forensics and Logging: Ensure robust data collection to track and respond to threats.
The Nearest Neighbor Attack exemplifies the ingenuity and resourcefulness of advanced persistent threats like GruesomeLarch. The report concludes that “Organizations need to place additional considerations on the risks that Wi-Fi networks may pose to their operational security.”
Related Posts:
- Volexity: Indian APT hacker organization Patchwork target US think tanks
- Over 2,100 Ivanti VPNs Compromised: The GIFTEDVISITOR Webshell Threat