Image: Malwarebytes Labs
PikaBot, a malware family that surfaced in early 2023, has swiftly morphed from being distributed via malspam campaigns to employing a more insidious delivery method: malvertising. This year, Malwarebytes Labs observed a notable increase in the utilization of malicious ads, especially through search engines, targeting businesses and exploiting browser vulnerabilities combined with social engineering tactics.
PikaBot was initially identified by Unit 42 in February 2023 as a potential Matanbuchus drop from a malspam campaign. The threat actor TA577, previously involved in the distribution of payloads such as QakBot, IcedID, SystemBC, and Cobalt Strike, as well as ransomware distribution, was attributed with the moniker PikaBot. Researchers at Cofense noticed a rise in malspam campaigns following the takedown of the QakBot botnet in August 2023, with PikaBot being one of the payloads delivered.

PikaBot distinguishes itself with its sophisticated infiltration methods. Typically, the distribution chain begins with an email containing a link to an external website. Unsuspecting users are lured into downloading a zip archive containing malicious JavaScript. This JavaScript creates a random directory structure and retrieves the malicious payload, which is then executed via rundll32. Remarkably, PikaBot’s core module is injected into the legitimate SearchProtocolHost.exe process, and its loader conceals its injection using indirect syscalls, rendering the malware extremely stealthy.
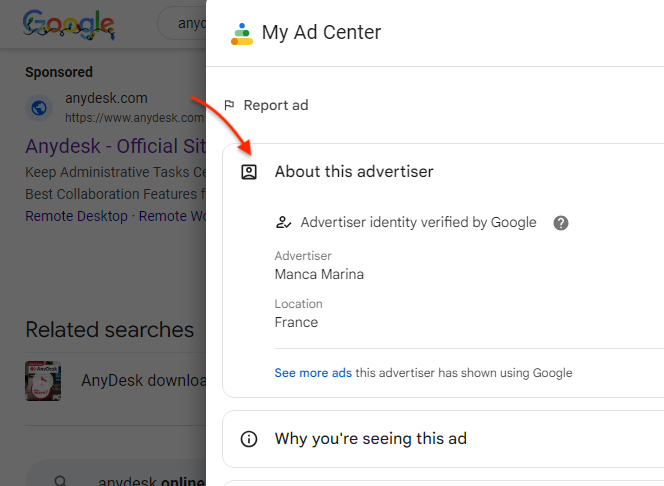
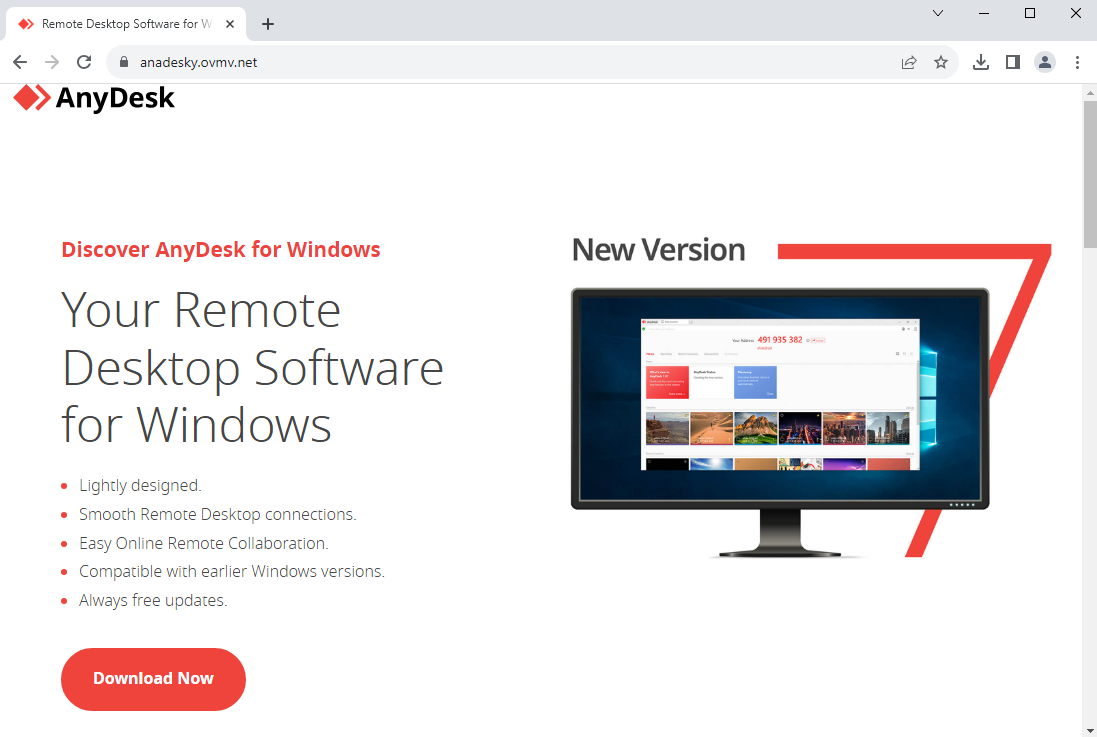
The malvertising campaign associated with PikaBot particularly targets Google searches for the remote application AnyDesk. A decoy website is set up, and the download is a digitally signed MSI installer. Interestingly, at the time of its collection by Malwarebytes Labs, this installer had zero detection on VirusTotal. The execution flow of this campaign involves bypassing Google’s security checks with a tracking URL via a legitimate marketing platform, redirecting to a custom domain behind Cloudflare. The threat actors perform fingerprinting via JavaScript to determine user environments and ensure the download link does not function in a virtualized environment.
PikaBot’s emergence marks a significant shift in the landscape of cyber threats. Previously, exploit kits were the primary malware distribution vector via drive-by downloads. As browser vulnerabilities became less effective, threat actors shifted focus to spam to target businesses. Now, with malvertising, threat actors have found a powerful delivery vector that does not require compromising websites. They exploit search engines by purchasing ads that reach their targeted audience.
Malwarebytes Labs has taken proactive measures by detecting the malicious MSI installers and the web infrastructure used in these malvertising campaigns. The malicious ads and download URLs have been reported to Google and Dropbox. Businesses can mitigate this risk by allowing their end users to install applications only via their trusted repositories, thus building a digital fortress against such insidious threats.
In conclusion, the advent of PikaBot, distributed via malicious search ads, underscores the need for constant vigilance and adaptive cybersecurity strategies.