wep
wep is a proof-of-concept Python script which generates VBA code that can be used in Office macros or templates. It was designed with automation and integration in mind, targeting locked down environment scenarios. The tool enumerates Software Restriction Policies (SRPs) and EMET mitigations and dynamically identifies safe binaries to inject payloads into. wep integrates with existing exploitation frameworks (e.g. Metasploit, Cobalt Strike) and it also accepts any custom payload in raw format.

Download
git clone https://github.com/ghost123gg/wep.git
pip install termcolor
Use
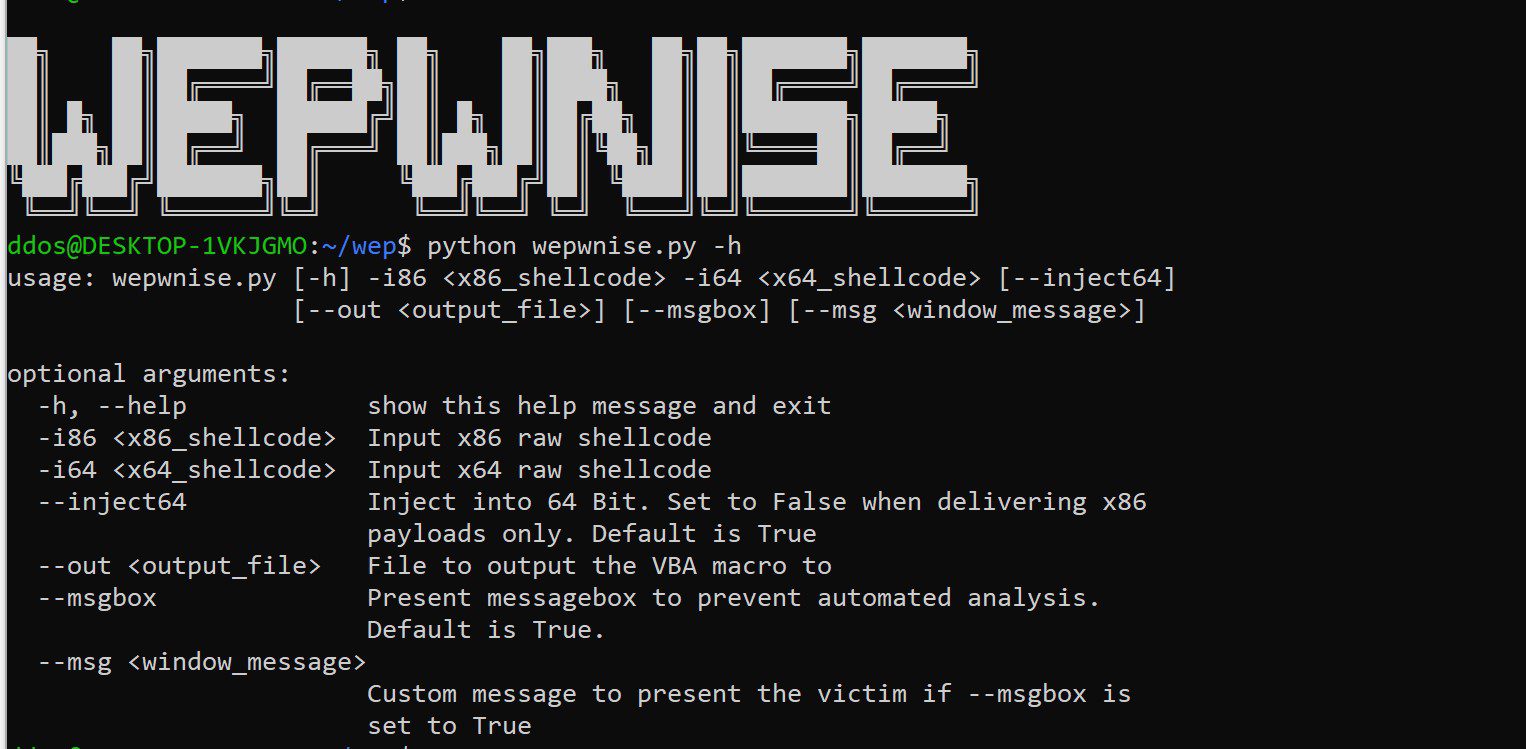
To start using wep, first take a look at the options it supports:
wep requires both 32 and 64-bit raw payloads in order to be able to deliver the appropriate type when it lands on an unknown target. However, if only an x86 architecture is targeted, a dummy 64-bit payload must be provided to replace the missing code.
In order to defeat certain automated analysis configurations, a message box opens upon execution of the code. The text of the message box can be altered by defining its value in the –msg parameter. To disable this functionality set the –msgbox parameter to False.
Due to performance conditions that may be introduced as a result of long SRPs/EMET policies, wep reads two configuration files (binary-paths.txt and directory-paths.txt) that contain a list of executables and directories which are less likely to be monitored to be checked first. By editing the contents of those files the user can define their own choices instead. If the files are empty, wep will directly start reading the SPRs/EMET policies as these would be defined within the Registry and make its injection choice purely based on the retrieved information.
Usage examples
The following sections describe some basic usage examples of wep.
Metasploit payloads
First the payloads for both x86 and x64 architectures in raw format and ensure that the Metasploit listeners are configured appropriately.
Then point wep to the generated payloads and direct the output to msf_wepwn.txt
Cobalt Strike payloads
To generate a raw payload in Cobalt Strike, navigate to the following menu and from the Output dropdown select the Raw format. Repeat the process and enable the x64 checkbox to produce a 64-bit payload.
Attacks > Packages > Payload Generator
Enter the generated payloads into wep to generate the VBA code.
Custom payloads
In certain cases, it may be the case that only an x86 payload be available. As wep expects both a 32-bit and 64-bit payloads, in order to disable 64-bit injection create a dummy 64-bit file and set the –inject64 parameter to False.
Similarly, to generate 64-bit payloads only, create a dummy x86 file and supply it in wep’s -i86 command line parameter.
Copyright (c) 2016 MWR InfoSecurity All rights reserved.
Source: https://github.com/ghost123gg/