Source: Anurag
Cybercriminals are once again exploiting social engineering tactics to trick unsuspecting users into installing malicious Android applications. A recent analysis by malware researcher Anurag uncovered a phishing campaign that spreads a fake SBI Bank Reward APK via WhatsApp messages. The fraudulent app is designed to steal banking credentials, debit/credit card details, OTPs, and personal information, putting victims at serious financial risk.
The attack begins with a WhatsApp message that appears to come from State Bank of India (SBI), claiming that the recipient’s reward points worth ₹9980 will expire soon. The message urges users to install the SBI Bank Reward App and redeem their points by depositing cash into their account. The message reads: “Your SBI BANK Reward Points (Rs 9980.00) will expire today. Now Redeem through SBI BANK
REWARD App install & Claim Your Reward by Cash Deposit Your Account.” Attached to this message is an APK file named “SBI REWARDZ POINT 1.apk“, which is a Trojan masquerading as an official banking rewards application.
Upon decompiling the APK, the researcher found that it requested an alarming number of dangerous permissions, including access to:
- SMS & Call Logs – Likely to intercept OTPs.
Contacts – Possibly for spreading the malware further.
Storage – To access and exfiltrate sensitive files.
The AndroidManifest.xml file revealed suspicious background services such as:
- SmsReceiver – To intercept SMS messages, including OTPs.
- BootBroadcastReceiver – To launch automatically upon device restart.
- BackgroundService – To run malicious activities silently
The malware communicates with command-and-control (C2) servers, sending stolen data via hardcoded URLs, including:
- https://superherocloud.com – Used for exfiltrating stolen banking credentials.
wss://socket.missyou9.in – A WebSocket connection for real-time data theft.
The researcher noted that “persistent communication over WebSocket could be classified as beaconing behavior, as it periodically updates the server with device status and other details.”
Running the APK in an Android emulator revealed that upon installation, the malware:
- Connects to its C2 server to register the infected device.
- Captures device information (model, Android version, mobile ID, SIM details).
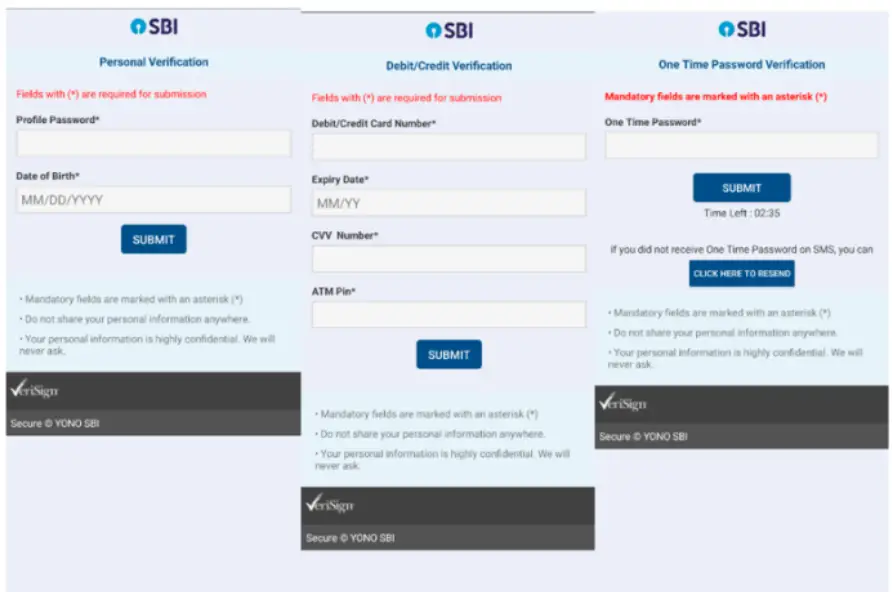
- Displays phishing screens that mimic SBI login pages to steal:
- Username & password
- Bank account & CIF number
- Debit/Credit card details, including CVV and PIN
- One-Time Passwords (OTPs)
Captured API logs confirmed that stolen credentials were sent to superherocloud.com for use in fraudulent transactions. When submitted to VirusTotal, the APK was flagged as malicious by 25 out of 67 security engines.
The C2 domains used by the malware were recently registered, indicating an active campaign.
- superherocloud.com – Registered 2 months ago.
- socket.missyou9.in – Registered 5 months ago and linked to other fake banking apps
The fake SBI Reward APK demonstrates sophisticated evasion techniques and real-time data theft, making it one of the more dangerous Android banking Trojans observed recently.
As Anurag warns, “While this particular APK was quickly identified as malicious, many others might slip through the cracks, targeting unsuspecting users.”
Related Posts:
- Last year, Google paid $ 2.9 million for the Vulnerability Reward Program
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs